Detecting attempts to run untrusted code by using trusted executables in Azure Security Center
In February 2017, FireEye documented a sophisticated spear phishing campaign targeting individuals within the Mongolian government. In the initial part of this attack, they were bypassing AppLocker restrictions by using Regsrv32.exe, which enables the attacker to run untrusted code. This technique was used in many others attack campaigns. By using virtual machine behavioral analysis, Security Center can detect attempts to bypass AppLocker. When Security Center detects an attempt to run untrusted code by using trusted executables, it will trigger an alert similar to the one below. 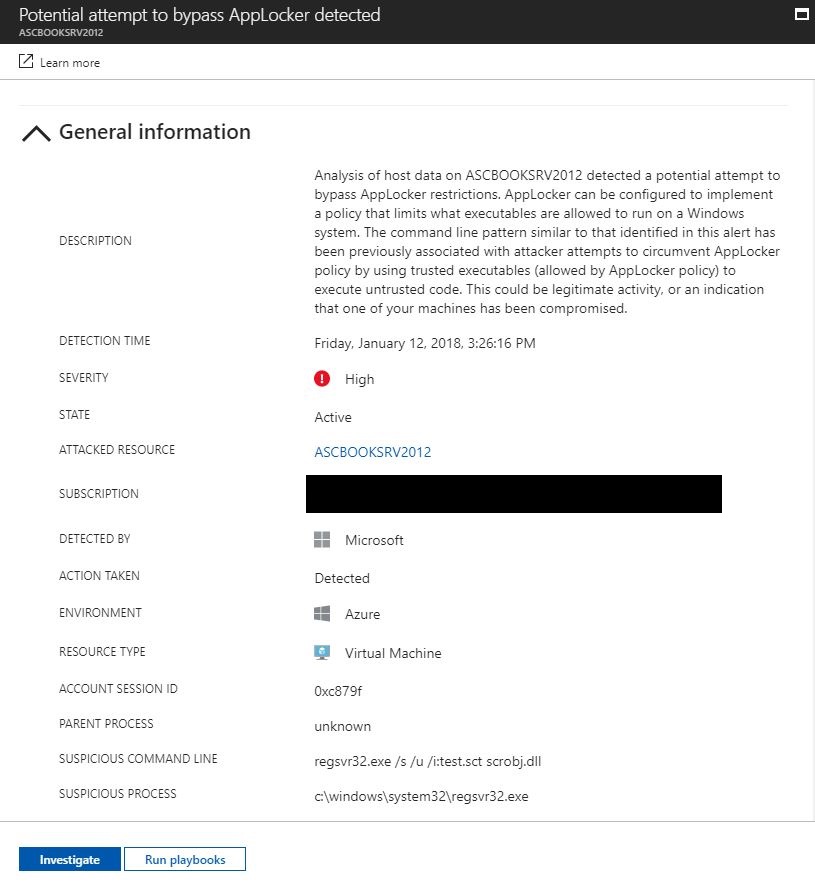
While Security Center can help you to detect this attack, you can use EMET to mitigate it. Besides that, always remember to implement least privilege administrative model, and privilege access workstations .
Note: EMET was discontinued November 2016, and if you are using Windows 10, follow the recommendations from Moving Beyond EMET, and read the section Use a Windows Defender Application Control policy to control specific plug-ins, add-ins, and modules from this article (thanks Kurt Falde for recommending this article).