Windows Azure Connect–Certificate Based Endpoint Activation
If you have deployed Windows Azure Connect endpoint before, you know that the endpoint will be required to present an activation token (which you can get from Windows Azure Management Portal) for activation. This activation token can be specified in the .cscfg file for Windows Azure Roles (this can also be done via Visual Studio). For the endpoints that live on your corporate network (local endpoints), the activation token is part of the install link. We are happy that you like the ease of use and simplicity of this approach. We also heard some of you request an option for secure activation.
To address this feedback, we introduced certificate based activation in our latest CTP Refresh. You can now choose to use existing activation model (token based only - this is the default) or certificate based activation (token + certificate). In this refresh, certificate based activation is only available for local endpoints.
If you already have PKI and/or have a mechanism to securely distribute X509 certificates (private + public key pairs) to your endpoints within your organization, you are just few steps away from benefiting from this new feature:
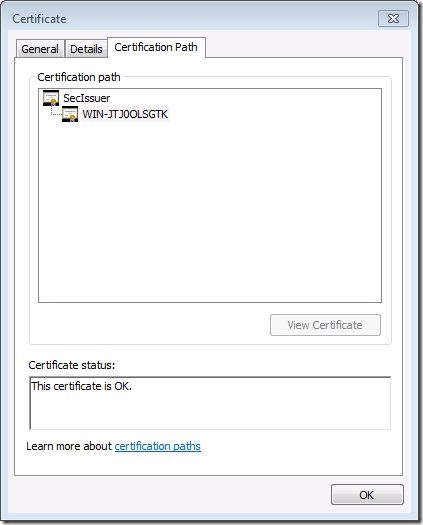
1. On your corporate network, pick a Certificate Issuer that issues certificates to endpoints via manual/auto-enrollment policies.
For example, the above snapshot shows that a machine that receives certificate from the issuer with CN=SecIssuer. In this case, the public key (.cer file) of CN=SecIssuer will need to be exported and saved for step 3 below.
Note: If you have deeper PKI hierarchy (example: CN=RootIssuer -> CN=SecIssuer -> CN=myendpoint), make sure you export the public key of the direct/immediate issuer i.e., CN=SecIssuer.
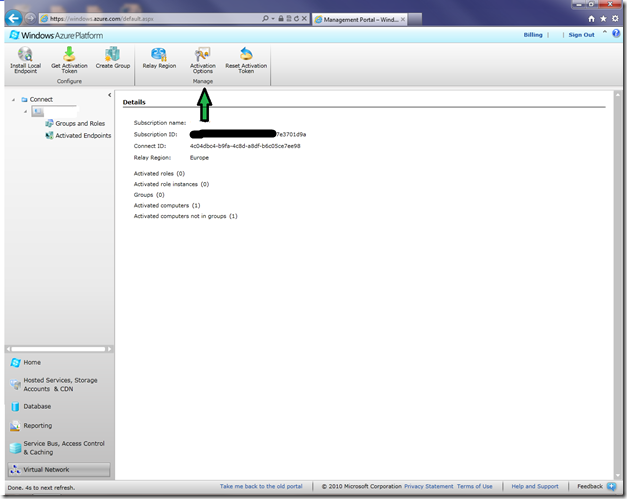
2. From the Windows Azure Management Portal, Click on the “Activation Options” as shown in the snapshot below.
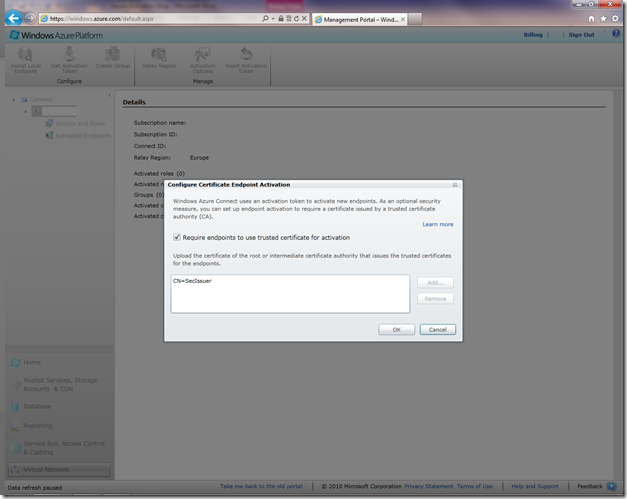
3. This will bring up the certificate endpoint activation dialog (shown in the snapshot below):
a. Check the box that says “Require endpoints to use trusted certificate for activation”.
b. Click on “Add” button and choose the certificate (.cer file with public key only) file from Step 1 above.
4. At this point, all the new endpoints (excluding Azure roles) in this subscription will be required to prove their strong identity via the possession of a certificate issued by the issuer in step 1 above. The endpoint must have private keys for this certificate, but there is no requirement for the subject name to match the endpoint’s FQDN or hostname (example: CN=myendpoint can be used on a machine with name ContosoHost.Corp.AdventureWorks.com).
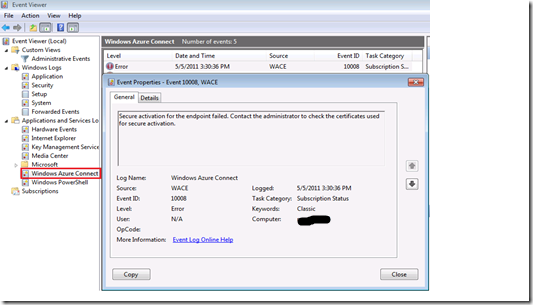
5. If you run into activation issues with this model, you can troubleshoot by checking the event viewer for any error messages such as below:
a. Verify that you have a certificate in the Local Computer\Personal\Certificates store. This certificate should have been directly issued by the issuer in step 1 above.
b. Verify that there is a private key for this certificate.