Turn a Windows Embedded-based Thin Client Into a Wireless Network Analyzer
Posted By Pavel Bansky
Program Manager
Thanks for checking back to Windows Embedded blog, I hope you won’t be disappointed. Today I want to write about an interesting usage of a Windows Embedded powered Thin Client. A friend of mine who works in Microsoft Support for Windows Phone was solving an interesting problem. One of the customers had issues accessing a particular webserver using Windows Phone. The webserver was using some certificate-based authentication and failed to authenticate the Windows Phone device. The question was: is it a problem with the phone or the server, or is the problem somewhere else? The first step was to capture and analyze the network traffic between the phone and server. Now, how to do it? There is nothing like WireShark for Windows Phone, so we can’t capture traffic there. Same on the server side, because the server is who knows where. So, I suggested capturing the traffic on the wireless router, but in order to do that we needed to build a router that allows network traffic to be captured.
Building a router
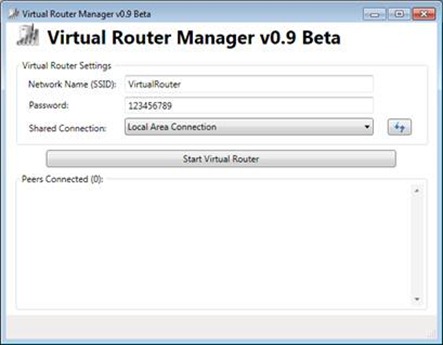
In order to build a simple network router that can host WireShark network analyzer, I took a Hewlett Packard t5740 Thin Client, that was running Windows Embedded Standard 7. These devices are pretty common and they come equipped with an Ethernet card and a Wireless card – that’s all we needed. The first thing I installed was VirtualRouter, a small but powerful CodePlex project from MVP Chris Pietschmann. VirtualRouter is a quick and simple UI for the Internet Connection Sharing feature of Windows 7. It makes your device look like a wireless hotspot for other devices and computers. The Ethernet port of the t5740 is connected to the “internet” and the Wireless port will be used for clients to connect to the router.
As a next step I installed WireShark network protocol analyzer. WireShark is a Swiss army knife for all networking professionals who are in need of capturing and analyzing network traffic. In order to install WireShark on t5740e, one needs to increase the size of the RamDisk so the uncompressed files will fit the \Temp directory.
Capturing packets
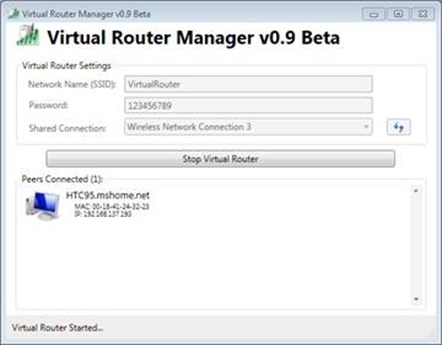
Now, the setup is ready to do some packet captures. First I started the VirtualRouter and connected my phone to the VirtualRouter wireless network. The phone will appear as a client in VirtualRouter manager UI.
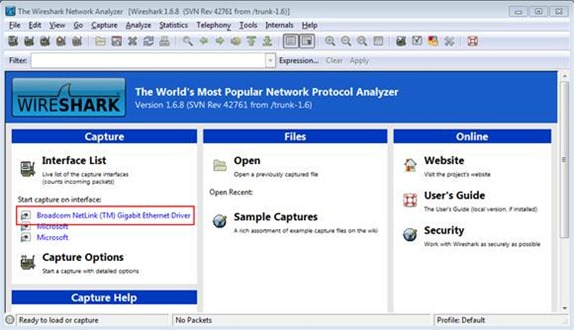
Next I started packet capturing on the BroadCom Netlink Gigabit Network Driver. The driver on your device might be different but t5740 comes equipped with this particular chipset. I took the phone and pointed browser to the specific website that was causing the troubles.
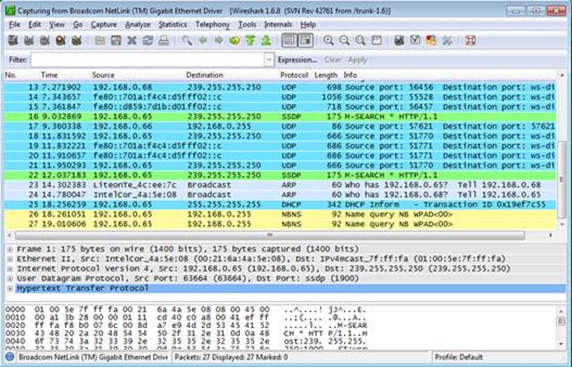
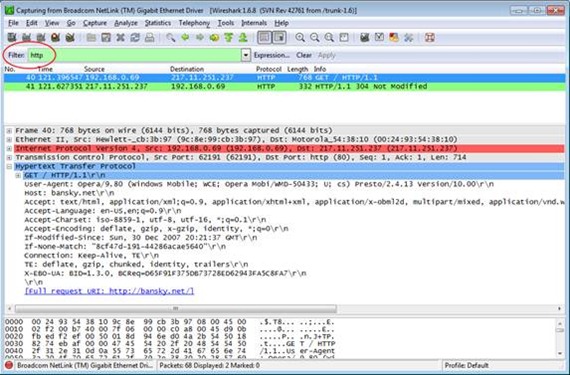
As you can see on the picture, WireShark will capture all traffic coming from and to your network interface. This was not very helpful as I was looking for specific authentication sequence. Now, for the sake of the article I’m not showing those specific certificate authentication packets but I’ll show general HTTP packets instead.
WireShark comes with a very efficient filter mechanism, so let’s type ‘http’ into the filter field as it’s shown on the picture. Suddenly the traffic does not look that bad and I can see the GET request for my website bansky.net/. Pretty easy huh!
In this article I wanted to show how a Thin Client powered by Windows Embedded that might be kicking around in your office can be easily reused as a very handy tool. I would certainly recommend taking a look at the VirtualRouter source code, it will give you some ideas on how to improve your homebrew router. Specifically in combination with WinPcap API, you can turn you router into a neat spy device J
I hope you’ll have fun exploring your network traffic!