Using HORM with unprotected volumes
HORM imposes the following restriction on volumes –
- All volumes must be protected by EWF.
[OR]
- All unprotected volumes must be dismounted before capturing the HORM state.
Note 1: Volumes residing on removable devices are excluded from this restriction.
Note 2: Boot and System volumes should not be dismounted. Hence they must always be protected by EWF when using HORM.
In this article we will describe how HORM can be safely used with unprotected volumes. We shall also describe how these unprotected volumes can be used to store event logs and paging files.
Case 1:
If all volumes are protected by EWF, the steps to use HORM are straightforward –
- Enable hibernation.
- Powercfg.exe /h ON
- Enable EWF on all volumes.
- Ewfmgr.exe /all /enable
- Activate HORM.
- Ewfmgr.exe X: /activatehorm -where X: is any protected volume. Note that HORM is not a per volume feature. It applies to the entire OS.
- Modify the system to reach the desired state.
- Capture the HORM state by hibernating the system once.
- Shutdown.exe /h
- Resume the machine. Beyond this point , each restart would cause the system to resume from the state captured in previous step.
- To deactivate HORM
- Ewfmgr.exe X: /deactivatehorm -where X: is any protected volume
- To disable EWF on all volumes.
- Ewfmgr.exe /all /disable
In RAM REG mode an additional step is required
- Ewfmgr.exe C: /commit -where C: is the volume containing the OS
Case 2:
If you wish to leave one or more volumes unprotected, additional steps are required
- Enable hibernation
- Powercfg.exe /h ON
- Enable EWF on all protected volumes
- Ewfmgr.exe /all /enable
- Activate HORM
- Ewfmgr.exe X: /activatehorm -where X: is any protected volume. Note that HORM is not a per volume feature. It applies to the entire OS.
- Modify the system to reach the desired state
- Deal with unprotected volumes
- a. Stop applications and / or services that have open handles to the unprotected volumes.
- b. Dismount unprotected volumes. (Details below)
- Capture the HORM state by hibernating the system
- Shutdown.exe /h
- Resume the machine. Beyond this point, each restart would cause the system to resume from the state captured in previous step.
- Deal with unprotected volumes
- a. Mount unprotected volumes (Details below)
- b. Start applications and / or services that need these unprotected volumes.
- To deactivate HORM
- Ewfmgr.exe X: /deactivatehorm -where X: is any protected volume
- To disable EWF
- Ewfmgr.exe /all /disable
In RAM REG mode an additional step is required
- Ewfmgr.exe C: /commit -where C: is the volume containing the OS
Registering for power transitions
Applications can receive notification when specific power events occur. This is documented in MSDN. Specifically , PBT_APMRESUMESUSPEND indicates the system has resumed from a lower power state. This can be used to automatically trigger the actions needed post resume.
Mounting and dismounting unprotected volumes
- Writing your own code - You can write your own application that makes use of the following FSCTLs to lock / unlock and mount / dismount volumes
- FSCTL_LOCK_VOLUME and FSCTL_UNLOCK_VOLUME
- FSCTL_DISMOUNT_VOLUME and FSCTL_MOUNT_VOLUME
A detailed MSDN article dealing with this topic is available here.
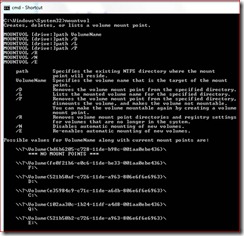
- Using Mountvol.exe – In WES 7, this utility can be found in the “Core File systems” package. It is a simple utility that lets you mount / dismount volumes.
To lock and dismount a volume use the “/P” option. In the above example, we can lock and dismount F: by issuing
Mountvol.exe F: /P
To mount back a volume use the volume GUID identifier listed for each volume. In above example, we re-mount F: by issuing
Mountvol.exe F: \\?\Volume{fe0f21b6-e0c6-11de-be33-001aa0ebe436}\
Dealing with applications that use unprotected volumes
General Guideline: Before dismounting a volume it is necessary to close all applications and/or services that may have open handles to files in this volume. You should start them again after the volume is mounted back.
As an example, we will show how to deal with Windows Event Log service configured to store logs in an unprotected volume.
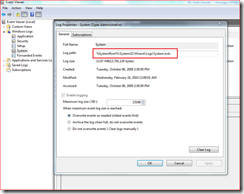
Windows Event Log Service manages the event logging in Windows. It can be configured to store logs in any desired location by modifying the “Log Path”.
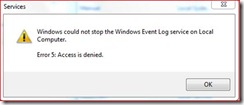
If you have configured Event Logs to be stored in an unprotected volume, it is necessary to stop the Event Log service before dismounting the volume.
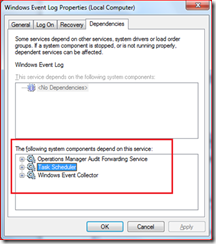
Take a look at the properties of Event Log service; it has other services that depend on it. Specifically, the “Task Scheduler” service cannot be stopped by usual means. This prevents the Event Log service from being stopped on the fly.
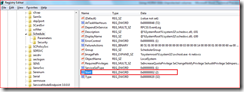
You will have to turn Task Scheduler service off by editing the registry. The” Task Scheduler” service is named “schedule”. Change the following value
Key: HKLM\System\CurrentControlSet\Services\Schedule
Value: Start Value Type: REG_DWORD
Existing value: 2 (AUTO). Change it to 4 (DISABLED). Restart the system for the change to take effect. Note that if you have applications that rely on task scheduler they will not work until it is re-enabled.
Now you can cleanly turn off the Windows Event Log service. You can turn it back ON post resume after the unprotected volume has been mounted back.
Using Page Files with HORM
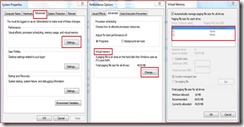
When using with EWF, paging Files must reside on unprotected volumes. This will avoid the problem of writes to paging files filling up the overlay. You can modify paging file location and size as shown below.
However, having a paging file on an unprotected volume will not allow the volume to be dismounted. To work around this, enable paging files post resume. This must be done after mounting back the unprotected volumes. Note that on Windows 7, enabling a paging file takes effect immediately; it is not required to restart the system. Paging can also be enabled programmatically using the WMI class Win32_PageFileSetting. See below for a sample VB script that creates and enables a page file of size 2048 MB using this WMI class.
'
' Adds a new instance of a system page file
'
'
' Connect to WMI locally
'
strComputer = "."
Set objWMIService = GetObject("winmgmts:" _
& "{impersonationLevel=impersonate,(CreatePagefile, Shutdown)}!\\" & strComputer & "\root\cimv2")
'
' Create a new instance
'
Set objNewPageFile = objWMIService.Get("Win32_PageFileSetting").SpawnInstance_
'
' Fill out properties
'
objNewPageFile.Name = "C:\\pagefile.sys"
objNewPageFile.InitialSize = CInt( 2048 )
objNewPageFile.MaximumSize = CInt( 2048 )
objNewPageFile.Put_
'
' Commit instance, this will overwrite an existing
' instance if present for the specified volume.
'
objWMIService.Put(objNewPageFile)
- Srikanth
Technorati Tags: Embedded Standard