Using AppLocker in Standard 7
* Updated 4/5/10 with clearer instructions for step 1*
In my last blog, I gave an overview of how AppLocker can help you lock down what applications can run on your Windows Embedded Standard 7 device. To demonstrate how AppLocker works, I’ll walk through an example of how to create a rule to block Internet Explorer from running. Here’s how, step by step:
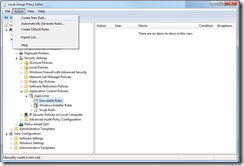
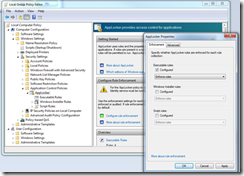
1. AppLocker can be configured through wizards in the Local Group Policy Editor, which you can start by running “gpedit.msc”. AppLocker is located under “Computer Configuration -> Windows Settings -> Security Settings -> Application Control Policies” in that window. Navigate to the Executable Rules option in the navigation on the left. In the Action menu, click Create New Rule.
2. The wizard will show an introduction screen. Click Next to continue past it.
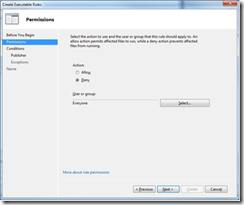
3. Because we want to deny Internet Explorer, choose Deny. You can also create Allow rules if you have a complex system where you want to allow applications that might violate other rules you create. For now, let’s keep it simple. This screen also selects which users you want this rule to apply to. I have chosen to apply this rule to Everyone. Click Next to continue.
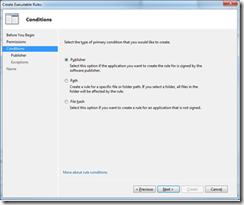
4. The next screen shows the various options AppLocker provides – it can block applications based on their file hash, path, or publisher information if the file is signed. Publisher rules have been improved over SRPs and are the most flexible and reliable, so we’ll use them. Click Next to create one.
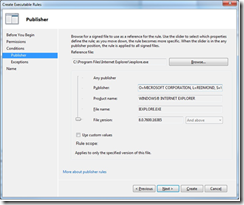
5. Publisher rules are based on the signed certificate of a given file, so you must navigate to the file for which you wish to make a rule in order to parse its certificate. Browse to Internet Explorer and select it. That will populate the fields below.
This screen demonstrates AppLocker’s flexibility. You can choose whether to deny based on Publisher (all Microsoft products), Product Name (all versions of Windows Internet Explorer), File Name (all files named iexplore.exe), or File Version (all versions of Internet Explorer less than 8, or greater than 7, etc.). I chose to block all versions by leaving the slider on the bottom and clicking Next.
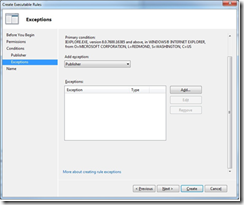
6. You can specify exceptions to the rule you just created. For example, if you chose to block all Microsoft products, you could make an exception for Office 2007. We don’t want to make any exceptions, so just skip this screen by clicking Next.
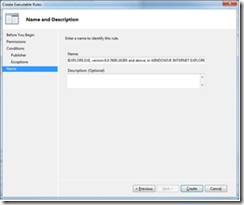
7. Now you can name your rule whatever you’d like, or leave it as the default. To finish creating your rule, click Create.
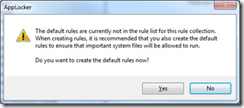
8. When you click Create, AppLocker will prompt you to create its default rules. These allow applications in Program Files and your Windows directory to run, as well as ensuring Administrators can run anything. These are strongly recommended. If you don’t include them, important Windows executables will be prevented from running and your system will likely become unstable or unusable. I clicked Yes to create them.
Now your rules are created and there’s just a bit of housekeeping to do to make sure everything works.
1. First, before leaving the AppLocker control panel, click on the root AppLocker node in the left navigation pane and click the Configure Rule Enforcement link on the main screen. You must ensure that Executable Rules are configured to either be enforced or audited. For this example, I will make them enforced.
2. Next, check that the Application Identity service is running – it is necessary for AppLocker to function. You can do this from the Services manager. In the Start Menu, search for “services”. Right-click the Services item and click Run as Administrator. Then find the Application Identity service and start it. You should also set it to start automatically so rules will be enforced even after you reboot.
3. Next, you have to update your Group Policy settings to make these rules begin working. From a command prompt, execute “gpupdate /force”.
4. Wait a minute – AppLocker rules take a minute or so to take effect.
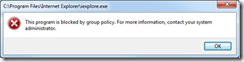
Now try and run Internet Explorer. If you set your rule correctly and set your rules to be enforced, you should see the message in the following screenshot, congratulations!
Using the templates feature in Windows Embedded Standard 7, we can take this functionality and capture it to use repeatedly on your images to avoid all this manual work, but that will have to wait for another time.
- Robert
Technorati Tags: Embedded Standard,Applocker