WGA Notifications and download and install telemetry
We’ve gotten a few questions recently about the fact that our latest WGA Notifications package sends install telemetry when installed or canceled. Given past concerns about data WGA sends out I wanted to take a moment to explain what is happening with this latest release and why.
First, all downloads that flow through Windows Update return success/failure telemetry. This is because of the large scale of distributions over Windows Update. When sending out an update package to potentially millions of customers it’s important to gather basic data on successful installations, install failures and user rejections or cancelations at any point in the process. Second, this event is one time only. Also, if the system isn’t connected to the internet nothing will be sent nor will it be if an attempt to send fails.
By learning at what point in the install process some users decide to abandon, we can put more effort into the right places in the installation wizard. Remember our goal with the wizard is to give more information so customers will be better informed. We heard from customers that they wanted more information about what the software was and how it worked so we created the install wizard to provide that greater context. Knowing this kind of information about the install wizard installations is critical for us to continue to improve the customer experience of WGA. If we are not hitting that mark, we can use this method to improve.
Just to allay any fears that Microsoft is using any personal information, here an example of the actual XML that is returned when a user cancels an installation. We’ve also added a data type and detailed description of each field. This XML schema is common to a number of products so some fields are not used in this case.
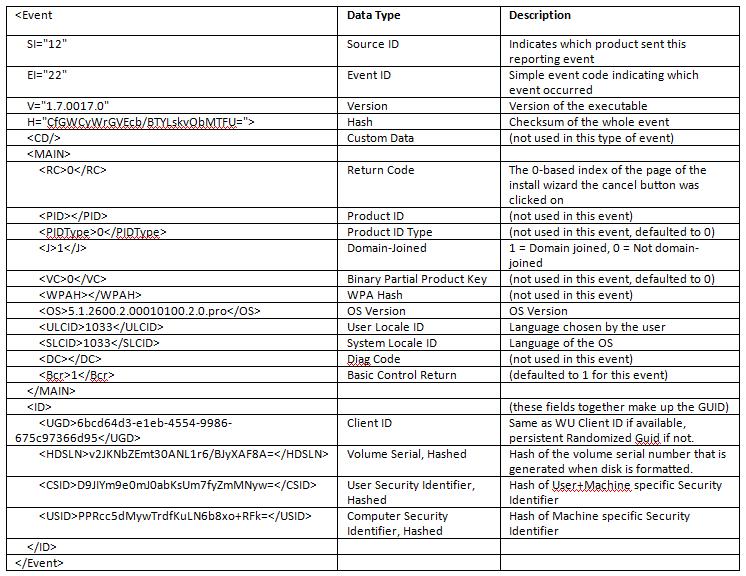
For completeness (and for our lawyers) I’d like to point out that disclosure of this type of install telemetry is made in the Windows Update privacy statement. All the information that is sent as a result of WGA Notifications being installed is covered by WGA-specific disclosures such as the EULA presented in the installation wizard and our privacy statements. Our commitment on privacy is oft-stated and we do not use any of the information collected through WGA to identify or contact any user. For more info on WGA Notifications see these pages.