Leveraging OMS Log Search to Help Planning and Tuning of Audit Policies
In this post, we look at how we can leverage the Security and Audit solution in OMS and using log searches to provide insights into the volume of security events collected to help plan and tune the audit policies accordingly.
In ACS, there are 4 Planning related SSRS audit reports available out-of-the-box that allow the user to identify high volume events occurring in their IT environment:
- The Planning: Event Counts Report,
- The Planning: Event Counts by Computer Report,
- The Planning: Hourly Event Distribution Report, and
- The Planning: Logon Counts of Privileged Users Report
The Security and Audit solution in OMS Log Analytics however provides a comprehensive view into your organization’s IT security posture with built-in search queries for notable issues that require your attention.
Adding the Security and Audit solution to an OMS workspace will allow Windows security events, Windows application events, and Windows firewall logs to be collected using direct agents or MMA agents that the user enabled.
For further information, refer to Security and Audit solution in Log Analytics by Bill Anderson.
To retrieve and analyze the security events highlighted by these 4 ACS Audit Reports in OMS Log Analytics, the SQL query search conditions used in these reports can be used as the filter expressions in OMS log search queries against records collected by the Security and Audit solution.
Planning: Event Counts Report:
The report shows the number of events collected, grouped by Event Id within a given date/time range.
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
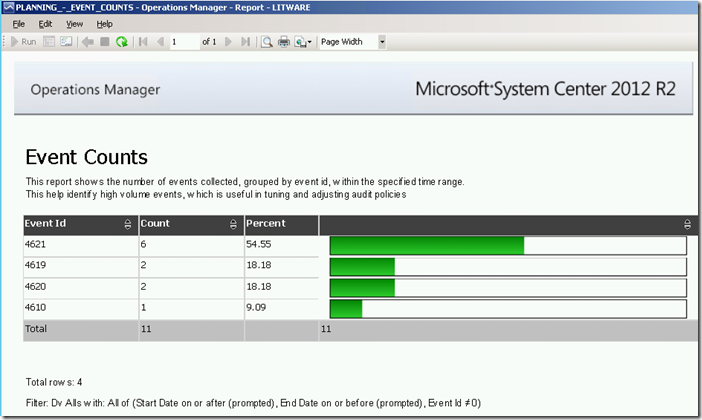
The RDL file of the Event Counts Report uses a Semantic Query, with the following filter condition:
Dv Alls with: All of (Start Date on or after (prompted), End Date on or before (prompted), Event Id ≠ 0)
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
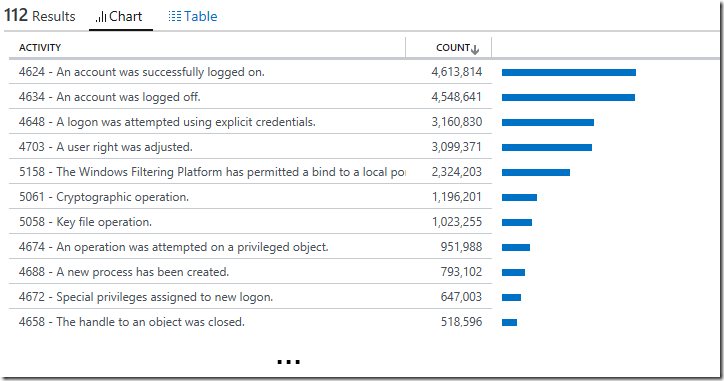
A query to compare the number of records of type SecurityEvent with EventID field ≠ 0, grouped by Activity in sortable order within a specific time period:
SecurityEvent
| where EventID!=0
| summarize Count=count() by Activity
| order by CountHere is an example of what the records returned would look like when using this log search query:
Planning: Event Counts by Computer Report
The report shows the number of events collected for a specific computer, grouped by Event Id, within a given date/time range.
The following figure shows the input parameters for this SSRS Report in the Reporting workspace in the OpsMgr Operations Console or the Reporting site:
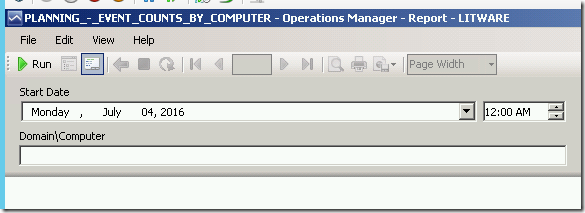
The RDL file of the Event Counts by Computer Report uses a Semantic Query, with the following filter condition:
Dv Alls with: All of (Start Date on or after (prompted), End Date on or before (prompted), UPPER(Domain\Computer) = (UPPER(Parameter: Domain\Computer) & "$"))
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
Queries to compare the number of records of type SecurityEvent for a specific computer, grouped by Activity or Event ID in sortable order within a specific time period:
let computerName = ""; //Enter Computer Name
SecurityEvent
| where Computer==computerName
| summarize Count=count() by Activity
| order by Countlet computerName = ""; //Enter Computer Name
SecurityEvent
| where Computer==computerName
| summarize Count=count() by EventID
| order by Count
Planning: Hourly Event Distribution Report
The report shows the event distribution on an hourly interval, within a given date/time range.
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
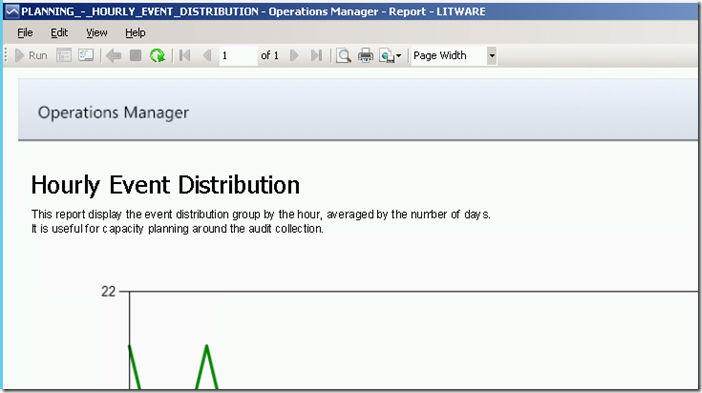
The RDL file of the Hourly Event Distribution Report uses a Semantic Query, with the following filter condition:
Dv Alls with: All of (Start Date on or after (prompted), End Date on or before (prompted))
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
A query to show the distribution of records of type SecurityEvent with EventID field ≠ 0, on an hourly interval within a specific time period:
SecurityEvent
| where EventID!=0
| summarize Count=count() by bin(TimeGenerated,1h)
| render timechartHere is an example of what the line graph returned would look like when using this log search query:
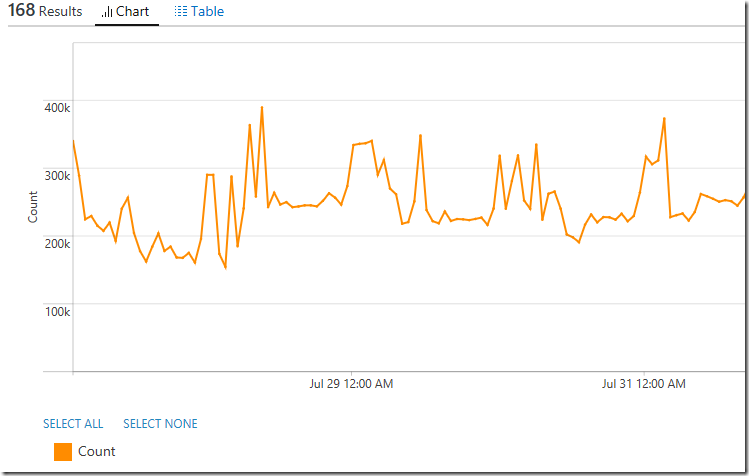
Note: Use the search query below to drill into the distribution of individual or a specific range Event Ids on an hourly interval within a specific time period if required:
let x=1; //Replace with start EventID
let y=10000; //Replace with end EventID
SecurityEvent
| where EventID between (x .. y) or EventID!=0
| summarize Count=count() by Activity, bin(TimeGenerated,1h)
| render timechart
Planning: Logon Counts of Privileged Users Report
The report returns information on logon counts of privileged users within a given date/time range by searching for security event 4672 stored in the ACS database.
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
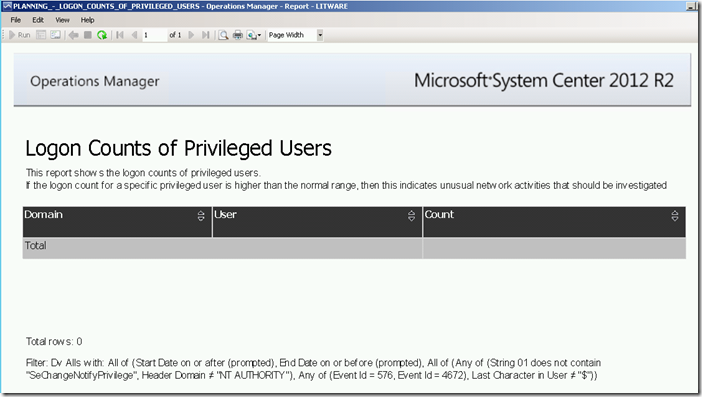
Here is an example of a 4672 – Special privileges assigned to new logon security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4672, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4672
The RDL file of the Logon Counts of Privileged Users Report uses a Semantic Query, with the following filter condition:
Dv Alls with: All of (Start Date on or after (prompted), End Date on or before (prompted), All of (Any of (String 01 does not contain "SeChangeNotifyPrivilege", Header Domain ≠ "NT AUTHORITY"), Any of (Event Id = 576, Event Id = 4672), Last Character in User ≠ "$"))
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
A search query to return all records of type SecurityEvent with EventID field containing 576 or 4672, SubjectDomainName field not containing the word “NT AUTHORITY” and AccountType ≠ “Machine”, limiting the result to the SubjectAccount and PrivilegeList fields:
SecurityEvent
| where EventID==576 or EventID==4672
| where SubjectDomainName!="NT AUTHORITY" and AccountType!="Machine"
| project SubjectAccount, PrivilegeList
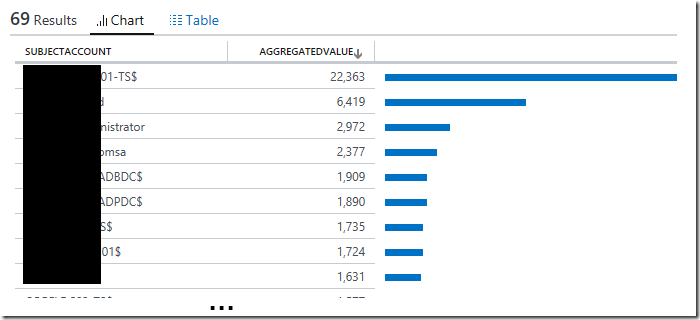
A query to compare the number of records of type SecurityEvent with EventID field containing 576 or 4672, SubjectDomainName field not containing the word “NT AUTHORITY” and AccountType ≠ “Machine”, grouped by SubjectAccount in sortable order within a specific time period:
SecurityEvent
| where EventID==576 or EventID==4672
| where SubjectDomainName!="NT AUTHORITY" and AccountType!="Machine"
| summarize count() by SubjectAccount
| order by count_Here is an example of what the records returned would look like when using this log search query:
To view the complete mapping between all Audit Collection Services (ACS) SSRS reports and search queries used in OMS Log Analytics, refer to:
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/25/mapping-acs-reports-to-oms-search-queries/