Leveraging OMS Log Search for Account Management and Audit Reporting
In this post, we look at how we can leverage the Security and Audit solution in OMS and using log searches for account management and reporting. This involves identifying security events related to changes made to accounts based on the audit events the Audit Collection Services (ACS) in OpsMgr collects and reports on.
In ACS, there are 4 Account Management related SSRS audit reports available out-of-the-box that allow the user to report on security events related to changes made to accounts occurring in their IT environment:
- The Account Management: Domain and Built-in Administrators Membership Changes Report,
- The Account Management: Passwords Change Attempts by Non-owner Report,
- The Account Management: User Accounts Created Report, and
- The Account Management: User Accounts Deleted Report
The Security and Audit solution in OMS Log Analytics however provides a comprehensive view into your organization’s IT security posture with built-in search queries for notable issues that require your attention.
Adding the Security and Audit solution to an OMS workspace will allow Windows security events, Windows application events, and Windows firewall logs to be collected using direct agents or MMA agents that the user enabled.
For further information, refer to Security and Audit solution in Log Analytics by Bill Anderson.
To retrieve and analyze the security events highlighted by these 4 ACS Audit Reports in OMS Log Analytics, the SQL query search conditions used in these reports can be used as the filter expressions in OMS log search queries against records collected by the Security and Audit solution.
Account Management: Domain and Built-in Administrators Membership Changes Report:
The report returns information on membership changes in the Domain and Built-in Administrators group within a given date/time range by searching for security events 4728, 4729, 4732, 4733 , 4756 or 4757 stored in the ACS database.
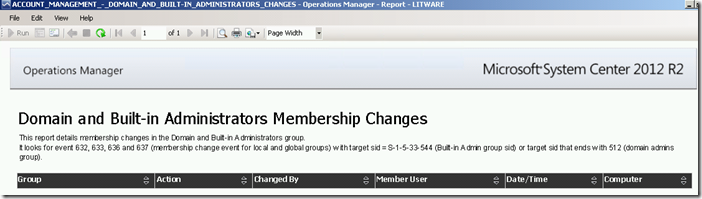
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
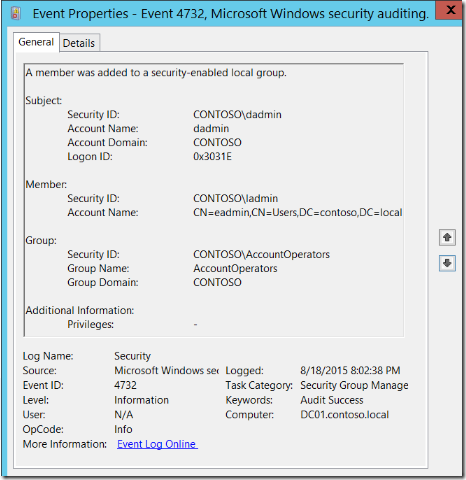
Here is an example of a 4732 – A member was added to a security-enabled local group security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4732, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4732
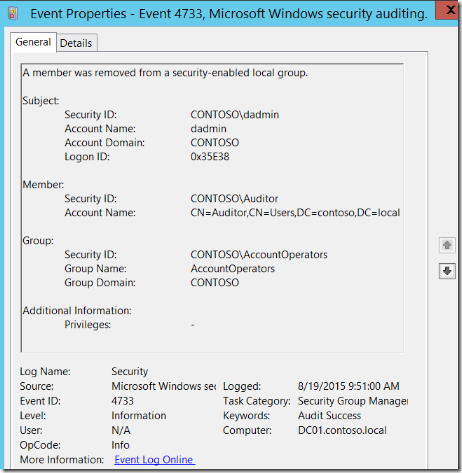
Here is an example of a 4733 - A member was removed from a security-enabled local group security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4733, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4733
The main SQL query used in the RDL file of the Domain and Built-in Administrators Membership Changes Report is:
SELECT TargetUser, Action, ChangedBy, MemberUser, DateTime, ComputerFROM AdtServer.dvAll5 WHERE (EventId=4728 OR EventId=4729 OR EventId=4732 OR EventId=4733 OR EventId=4756 OR EventId=4757) AND CreationTime >= @StartDate AND CreationTime <= @EndDateAND (TargetSid LIKE '%-512' OR TargetSid = 'S-1-5-32-544')….. |
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
A search query to return all records related to members being added to a security-enabled local group of type SecurityEvent with EventID field containing 4728 or 4732 or 4756 or 632 or 636 or 660 and each record containing a key string of “*512” or “S-1-5-32-544”, limiting the result to the Action, TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, Computer fields:
SecurityEvent
| where EventID==4728 or EventID==4732 or EventID==4756 or EventID==632 or EventID==636 or EventID==660
| search “S-1-5-32-544” or “512”
| project Action=”Add Member”, TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, ComputerA search query to return all records related to members being removed from a security-enabled local group of type SecurityEvent with EventID field containing 4729 or 4733 or 4757 or 633 or 637 or 661 and each record containing a key string of “*512” or “S-1-5-32-544”, limiting the result to the Action, TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, Computer fields:
SecurityEvent
| where EventID==4729 or EventID==4733 or EventID==4757 or EventID==633 or EventID==637 or EventID==661
| search “S-1-5-32-544” or “512”
| project Action=”Remove Member”, TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, Computer
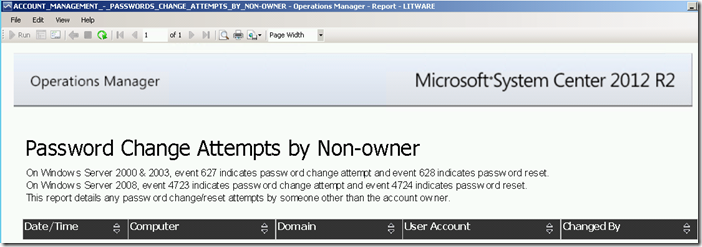
Account Management: Passwords Change Attempts by Non-owner Report
The report returns information on password change attempts within a given date/time range by searching for security events 4723 or 4724 stored in the ACS database.
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
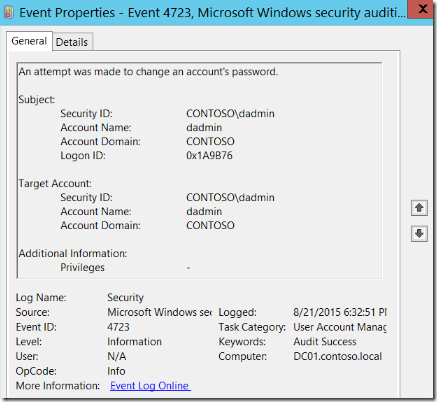
Here is an example of a 4723 – An attempt was made to change an account's password security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4723, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4723
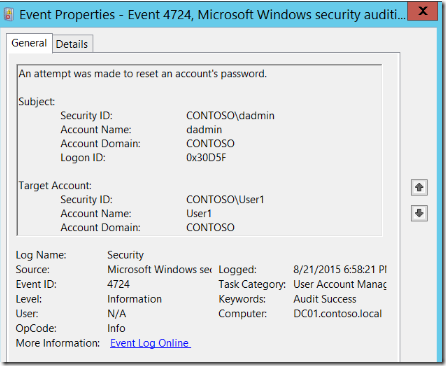
Here is an example of a 4724 – An attempt was made to reset an account's password. security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4724, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4724
The main SQL query used in the RDL file of the Passwords Change Attempts by Non-owner Report is:
SELECT DateTime, Computer, Domain, UserAccount, ChangedByFROM AdtServer.dvAllWHERE (EventId = 4723 OR EventId = 4724) AND (TargetDomain <> PrimaryDomain) AND (PrimaryUser <> 'ANONYMOUS LOGON') AND (CreationTime >= @StartDate) AND (CreationTime <= @EndDate) OR (EventId = 4723 OR EventId = 4724) AND (PrimaryUser <> 'ANONYMOUS LOGON') AND (CreationTime >= @StartDate) AND (CreationTime <= @EndDate) AND (TargetUser <> PrimaryUser) ….. |
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
A search query to return all records related to password changes of type SecurityEvent with EventID field containing 627 or 628 or 4723 or 4724, and SubjectAccount not equal to TargetAccount, limiting the result to the TimeGenerated, Computer, TargetAccount and ChangedBy fields:
SecurityEvent
| where EventID==4723 or EventID==4724 or EventID between (627 .. 628) and SubjectAccount != “ANONYMOUS LOGON” and TargetAccount!=SubjectAccount
| project TimeGenerated, Computer, TargetAccount, ChangedBy=SubjectAccount
Here is an example of what the records returned would look like when using this log search query:
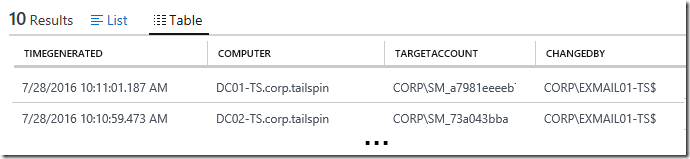
Note: To find out whether these security events were collected by OMS Log Analytics in the first place, use the following search query first before running the long query above:
SecurityEvent
| where EventID==4723 or EventID==4724 or EventID between (627 .. 628) and SubjectAccount != “ANONYMOUS LOGON” and TargetAccount!=SubjectAccount
| summarize count() by EventID
Account Management: User Accounts Created Report
The report shows user accounts created within a given date/time range by searching for security event 4720 in the ACS database.
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
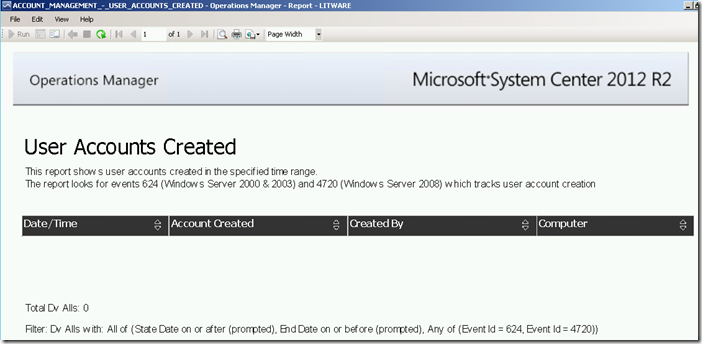
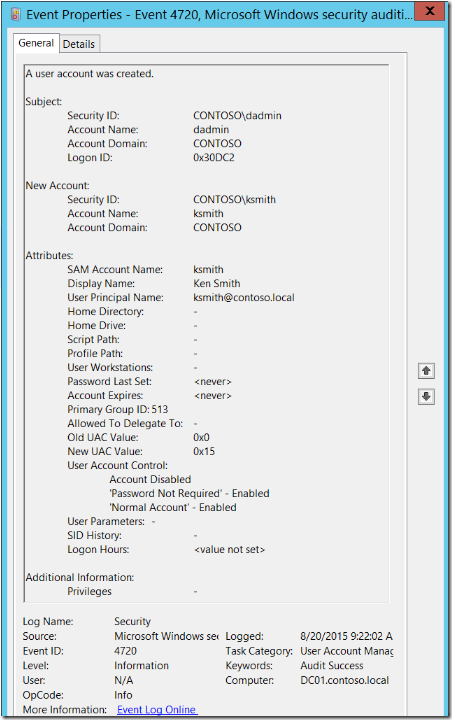
Here is an example of a 4720 – A user account was created security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4720, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4720
The RDL file of the User Accounts Created Report uses a Semantic Query, with the following filter condition:
Dv Alls with: All of (State Date on or after (prompted), End Date on or before (prompted), Any of (Event Id = 624, Event Id = 4720))
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
A search query to return all records of type SecurityEvent with EventID field containing 624 or 4720, limiting the result to the TimeGenerated, TargetAccount, CreatedBy and Computer fields:
SecurityEvent
| where EventID==624 or EventID==4720
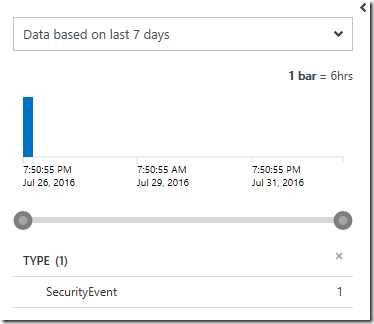
| project TimeGenerated, TargetAccount, CreatedBy=SubjectAccount, ComputerHere is an example of what would be shown on the time selector in the user interface of the portal if this log search query found some matching records:
Account Management: User Accounts Deleted Report
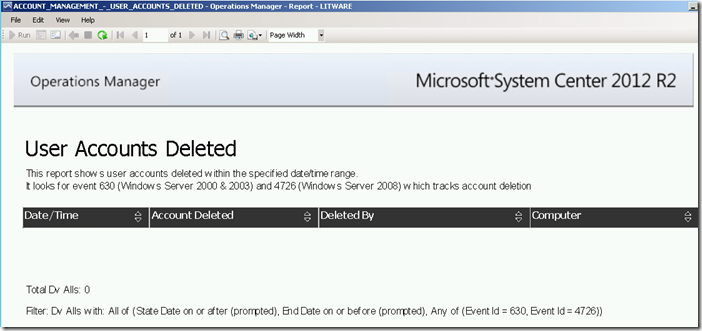
The report shows user accounts deleted within a given date/time range by searching for security event 4726 in the ACS database.
Running this report for a specific date/time range via the Reporting workspace in the OpsMgr Operations Console or the Reporting site will produce the following SSRS Report:
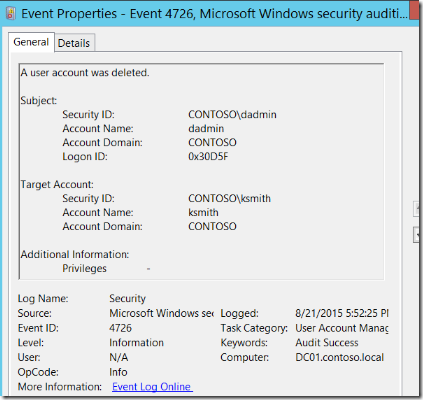
Here is an example of a 4726 – A user account was deleted security event as shown at the Windows Security Auditing technical documentation on TechNet:
For more information about Event 4726, visit https://technet.microsoft.com/en-us/itpro/windows/keep-secure/event-4726
The RDL file of the User Accounts Deleted Report uses a Semantic Query, with the following filter condition:
Dv Alls with: All of (State Date on or after (prompted), End Date on or before (prompted), Any of (Event Id = 630, Event Id = 4726))
The search condition from this SQL Query can be used as the filter expression of OMS log searches against Security and Audit solution records like the following example:
A search query to return all records of type SecurityEvent with EventID field containing 630 or 4726, limiting the result to the TimeGenerated, TargetAccount, CreatedBy and Computer fields:
SecurityEvent
| where EventID==630 or EventID==4726
| project TimeGenerated, TargetAccount, DeletedBy=SubjectAccount, Computer
To view the complete mapping between all Audit Collection Services (ACS) SSRS reports and search queries used in OMS Log Analytics, refer to:
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/25/mapping-acs-reports-to-oms-search-queries/
Additional Resources:
Well-known security identifiers in Windows operating systems
https://support.microsoft.com/en-au/kb/243330