Accessing Azure SQL DB from an Azure VM Using the External IP Address
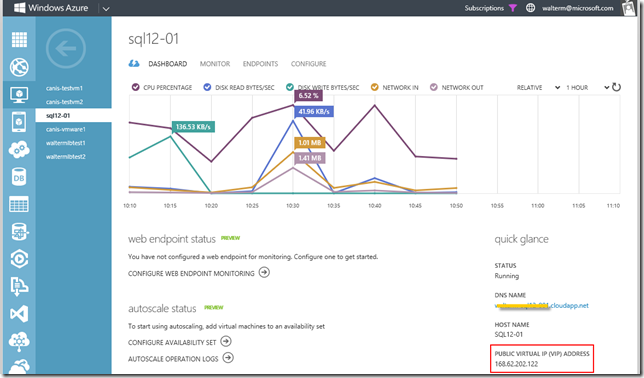
A customer asked me the other day how they can disallow arbitrary machines from within the Windows Azure environment to have access to their Azure SQL Database servers, while still allowing specific machines within the Azure environment to have access to their Azure SQL Database servers. This is pretty simple to implement so I thought I would crank out a quick blog post to demonstrate how it is done. So here goes. First, identify the public Virtual IP Address of the virtual machine you wish to access your Azure SQL Database server, as seen below (in my case, it is an IaaS virtual machine since it makes testing easier, but this will of course work the same for a PaaS virtual machine).
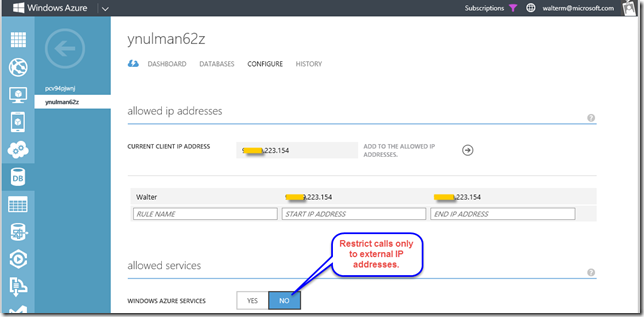
Now head over to the Azure SQL Database server you would like to secure, select the Configure tab, and then select the No button for Windows Azure Services, as seen below. You will then have to save this change.
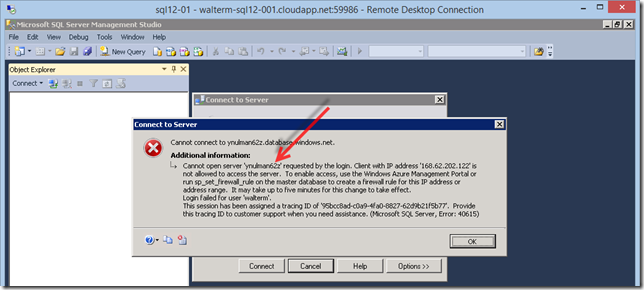
In order to test that I no longer have access to the Azure SQL Database server from within the Azure platform, I try to connect to it from SQL Server Manager on the virtual machine that I want to provide access. As you can see below, the connection fails.
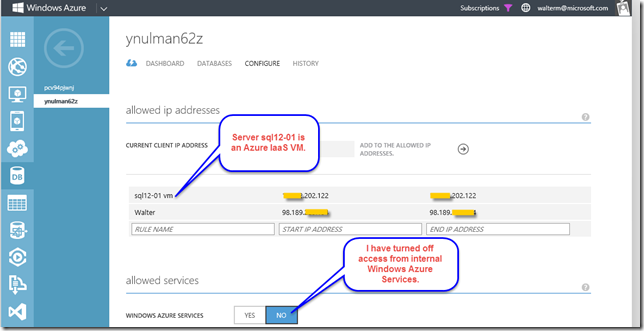
Now I head back to the configuration for the Azure SQL Database server and add a rule to the server whitelist using the external VIP address of the desired virtual machine, as seen below.
I now attempt to connect to the Azure SQL Database server and can successfully connect, as seen below.
We’re now done. If only all things in Azure were this easy!