An unusual reason to enable MAC spoofing
By default, Hyper-V will not let software inside of a virtual machine attempt to generate network traffic with a MAC address other than the address that Hyper-V has assigned to the virtual machine (known has MAC address spoofing). The reason why this is not allowed by default is that it is relatively uncommon to need to do this, and MAC address spoofing can be used for malicious purposes.
However, I found that I needed to enable this on one of my virtual machines recently.
For a while now I have been running Hyper-V on my primary desktop system – which means I have been unable to run Virtual PC on it directly. I have a couple of other computers handy (including my laptop) where I run Virtual PC instead. But there are times when I am working on my desktop computer – and I do not want to switch to another computer in order to confirm something about Virtual PC. To solve this problem – I simply run Virtual PC inside a Hyper-V virtual machine!
This has been working fine for me – and I have mostly been using Windows XP mode with the default settings. But the other day I needed to do some advanced networking operations, that would not work with the default network setting of using Shared Networking (NAT). After changing the virtual machine to use the host network adapter directly – I was surprised to see that I was unable to get an IP address from my DHCP server:
It took me a while to figure it out – but Virtual PC uses MAC address spoofing in order to generate network traffic that looks like it is coming from the virtual machine (and not from the host). I quickly enable MAC address spoofing and everything was good-to-go.
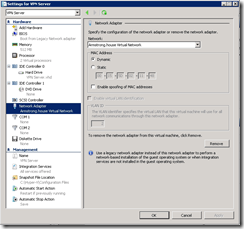
For the curious – the user interface for enabling this setting can be found on the network settings page on Windows Server 2008 R2:
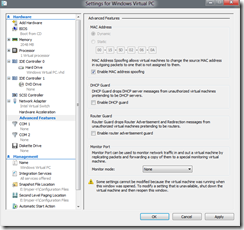
And under the Advanced Features section of the network settings page on the Windows 8 Developer Preview (which is what I am running at home at the moment):
Cheers,
Ben