How to Update Certificates for AD FS
How to Update Certificates for AD FS
Active Directory Federation Services (AD FS) 3.0 is a server role included in Windows Server 2012 R2.
Active Directory Federation Services (AD FS) 4.0 is a server role included in Windows Server 2016.
Certificates used by federation servers
Each federation server is required to have a server authentication certificate and a token-signing certificate before it can participate in AD FS communications. The trust policy requires an associated certificate, known as a verification certificate, which is the public key portion of the token-signing certificate.
| Server authentication certificates | The federation server uses Secure Sockets Layer (SSL) server authentication certificates to secure Web services traffic for communication with Web clients or the federation server proxy. These certificates are requested and installed through the Internet Information Services (IIS) snap-in. |
| Token-signing certificates | Each federation server uses a token-signing certificate to digitally sign all security tokens that it produces. Because each security token is digitally signed by the account partner, the resource partner can verify that the security token was in fact issued by the account partner and that it was not modified. This helps prevent attackers from forging or modifying security tokens to gain unauthorized access to resources.Digital signatures on security tokens are also used in the account partner when there is more than one federation server. In this situation, the digital signatures verify the origin and integrity of security tokens that are issued by other federation servers in the account partner. The digital signatures are verified with verification certificates. |
Replacing the SSL Certificate for an AD FS farm
Normally the SSL certificate for the AD FS farm comes from a trusted third-party CA, like DigiCert or Verisign. This is a traditional SSL cert like you would use in IIS for any secure web server. You may use a Single-name, subject alternative name (SAN), or wildcard cert for this purpose as long as it's valid and trusted by internal and external AD FS clients. You can find more information about the certificate requirements here.
Now you can use Azure AD Connect Tool to update the SSL certificate for an Active Directory Federation Services (AD FS) farm. AD Connect is the preferred method for changing the SSL certificate.
You can perform the whole operation of updating SSL certificate for the AD FS farm across all federation and Web Application Proxy (WAP) servers in three simple steps:
- Provide ADFS Farm Information
- Provide new SSL Certificate
- Select Servers for update
Prerequisites
- AD FS Farm: Make sure that your AD FS farm is Windows Server 2012 R2-based or later.
- Azure AD Connect: Ensure that the version of Azure AD Connect is 1.1.553.0 or higher. You'll use the task Update AD FS SSL certificate

Step 1: Provide AD FS farm information
Azure AD Connect attempts to obtain information about the AD FS farm automatically by:
-
- Querying the farm information from AD FS (Windows Server 2016 or later).
- Referencing the information from previous runs, which are stored locally with Azure AD Connect.
You can modify the list of servers that are displayed by adding or removing the servers to reflect the current configuration of the AD FS farm. As soon as the server information is provided, Azure AD Connect displays the connectivity and current SSL certificate status.

If the list contains a server that's no longer part of the AD FS farm, click Remove to delete the server from the list of servers in your AD FS farm.

Note - Removing a server from the list of servers for an AD FS farm in Azure AD Connect is a local operation and updates the information for the AD FS farm that Azure AD Connect maintains locally. Azure AD Connect doesn't modify the configuration on AD FS to reflect the change.
Step 2: Provide a new SSL certificate
After you've confirmed the information about AD FS farm servers, Azure AD Connect asks for the new SSL certificate. Provide a password-protected PFX certificate to continue the installation.

After you provide the certificate, Azure AD Connect goes through a series of prerequisites. Verify the certificate to ensure that the certificate is correct for the AD FS farm:
-
- The subject name/alternate subject name for the certificate is either the same as the federation service name, or it's a wildcard certificate.
- The certificate is valid for more than 30 days.
- The certificate trust chain is valid.
- The certificate is password protected.
Step 3: Select servers for the update
In the next step, select the servers that need to have the SSL certificate updated. Servers that are offline can't be selected for the update.

After you complete the configuration, Azure AD Connect displays the message that indicates the status of the update and provides an option to verify the AD FS sign-in.

- Tip:Use the DigiCert SSL Installation Diagnostics Tool to confirm that the certificate and all intermediate certs are installed correctly, This tool works with any third-party CA certificate, not just DigiCert's.
Replacing the Token-Signing and Token-Decrypting Certificate
The Token-Signing and Token-Decrypting certificates are normally self-signed certificates good for one year, dated from the time the primary AD FS server was installed. The Office 365 portal will warn you when these certs are about to expire and that user access to all Office 365 services will fail.
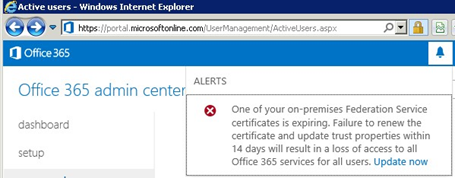
By default, Token-Signing and Token-Decrypting Certificates will expire one year after your ADFS was setup. Near to the expiration period you will get the following notification on your Portal Admin Page.
This notification does not apply to SSL Certificate, also known as Service Communications Certificate.
The number of days represents the day where the service will stop. Due to certificate change.
How to calculate the effective day:
The new Certificate will be generated 20 days before the certificate expirations date:
1) Go to Powershell
2) Connect-MsolService
3) Get-MsolFederationProperty
4) Check [CertificateGenerationThreshold: 20]
The new certificate will be promoted to Primary after 5 days:
1) Go to Powershell
2) Connect-MsolService
3) Get-MsolFederationProperty
4) Check [CertificatePromotionThreshold: 5]
Knowing that AD FS Service only uses the primary certificate, as we will switch the certificates 15 days before the current primary certificates expires the service will stop 15 days before the current certificate expiration.
This is not true if the Relying party has been updated on the 5 days that exist between the new certificate creation and the promotion.
Example:
Certificate expires on 30-01-2014.
New certificate will be created on 10-01-1014 and will be marked as Secondary [20 days before expiration].
On the 15-01-2014 the Secondary Certificate is promoted to Primary [5 days after new certificate generation].
If we see the message on the portal on the day 05-01-2014 this should be informing that the service will stop in 10 days, if federation metadata information is not updated.
ADFS default configuration:
Default configuration on AD FS regarding Token Signing and Token Decrypting certificates includes an auto-renewal process, [AutoCertificateRollover].
If you did not change this value from “True” to “False”, no renewal operation regarding token certificates is needed, this will happen automatically based on triggers explained below.
Default values of ADFS - [see details below for default values]:
The Rollover interval is checked by the AD FS service every 720 minutes (12 hours).
If the existing primary certificate (Token Signing or Token Decryption) expiration time is within the window of the CertificateGenerationThreshold value (20 days), then a new certificate is generated and configured as the secondary certificate.
Noted by event ID 335 in the event logs: It will remain as the secondary certificate until the CertificatePromotionThreshold value is observed (5 days). So, 5 days after creation of the certificate, it will be promoted and the existing primary will be configured as the secondary until the next CertificateGenerationThreshold window is observed.
Once the Promotion event has occurred, the Token Service will sign/encrypt all issued tokens with the new primary certificate.
This does not cause a service outage of AD FS 2.0, but an application issue when the token is received and signed with something other than the expected certificate. This is true for O365 or any other application.
With AutoCertificateRollover enabled, AD FS 2.0 will continue to function as expected.
Validate your ADFS configuration:
To validate your configuration, connect to your primary ADFS Server and follow these PowerShell instructions:
Open the Windows PowerShell
Add-PSSnapin Microsoft.ADFS.PowerShell
Get-ADFSProperties
CertificateCriticalThreshold: 2 - Days prior to expiry of the certificate before a new certificate is generated and promoted if AutoCertificateRollover has not performed naturally.
CertificateDuration: 365 - Validity period of the auto-generated Certificate.
CertificateGenerationThreshold: 20 - Days before expiration of current primary a new certificate will be generated.
CertficatePromotionThreshold: 5 - Days the newly generated certificate will exist before being promoted from secondary to primary.
CertificateRolloverInterval: 720 - Interval in minutes at which we check to see if a new certificate needs to be generated.
CertificateThresholdMulitplier: 1440 - Number of minutes used in calculation of other threshold counters (default value is 1440 minutes or 24 hrs. X 60 minutes, which makes threshold values equal to full days).
To have single sign on with ADFS the federation certificates need to be updated with the online platform. O365 is now automatically pulling the certificates from the AD FS server via the public metadata endpoint on a regular basis.
You may need to manually update the federation metadata using the PowerShell in complement to the Microsoft pull mechanism, as this will not pull the certificates on all scenarios.
How to Enable and Immediately Use AutoCertificateRollover
If you have turned off AutoCertificateRollover in the past and you want to turn it back on, there are a few things you need to consider
- Simply turning AutoCertificateRollover back on via PowerShell will not immediately cause the self-signed certificates to be generated
- The self-signed certificates will only be generated once the critical threshold (close to expiration) of your existing certificates has been met
- There is a way to immediately cause the self-signed certificates to be generated, but this will cause service outage with your partners until they have refreshed from your federation metadata. We recommend causing the certificate generation after hours to avoid an outage.Alternatively, you could work closely with your partners to ensure that they are ready to immediately update via federation metadata (causing a short outage).
if you decide to let the existing certificates hit the critical threshold instead of invoking the certificate generation process, then you only need to re-enable AutoCertificateRollover.
If you decide that you want to immediately generate new self-signed certificates, then you need to first re-enable AutoCertificateRollover and then issue a PowerShell command to invoke immediate certificate generation.
PowerShell command to re-enable
AutoCertificateRollover:
Add-PSSnapin Microsoft.Adfs.Powershell
Set-ADFSProperties -AutoCertificateRollover $true
PowerShell command to immediately generate new self-signed certificates:
Add-PSSnapin Microsoft.Adfs.Powershell
Update-AdfsCertificate -Urgent
NOTE: Be aware that there is an AD FS service outage incurred when the Token-Decrypting or Token-Signing certificates are updated because the relaying parties must update their configuration to expect the new certs. Do this work when users are least impacted by the outage.
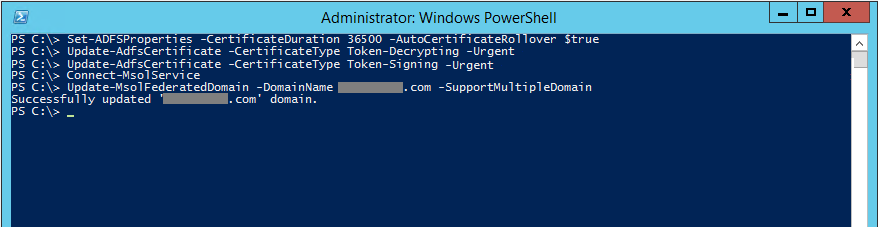
Before you renew the Token-Signing and Token-Decrypting certificates I recommend that you increase the AD FS certificate lifetime for self-signed certs.
- Logon to the primary AD FS server and open an elevated PowerShell prompt. Run the following to configure the AD FS server to generate self-sign Token-Signing and Token-Decrypting certificates that last 10 years and enable Auto Certificate Rollover:
Set-ADFSProperties CertificateDuration 3650 -AutoCertificateRollover $true
- These cmdlets will generate new self-signed Token-Signing and Token-Decrypting certificates which will be promoted immediately and then disable auto certificate rollover again. Relay partners will need to update their metadata to accept the new signed claims:
Update-AdfsCertificate -CertificateType Token-Decrypting -Urgent
Update-AdfsCertificate -CertificateType Token-Signing -Urgent
Set-ADFSProperties -AutoCertificateRollover $false
- Update the Office 365 metadata using Windows Azure PowerShell:
Connect-MsolService
Update-MsolFederatedDomain -DomainName domain.com -SupportMultipleDomain
- Remember that you'll need to update other relaying party metadata, if you use them. For example, Yammer on-prem (not Office 365) must be updated manually by Microsoft by opening a support ticket in the Office 365 portal. You will need to supply them with the Token-Signing and Token-Decrypting certificates (minus the private keys).
A Note About WAP Servers
If your organization uses Windows Application Proxy (WAP) servers for your AD FS deployment, there's nothing else you need to do regarding Token-Signing and Token-Decrypting certificates. WAP servers only use the Service Communications SSL cert.