Microsoft's New Identity Landscape
PDC has come and gone, and Microsoft's identity landscape has changed. New products emerged, services appeared or underwent profound transformations: but the remarkable thing is that all elements, none excluded, are part of a single,company-wide, consistent strategy that aims at putting the user in control of his/her identities.
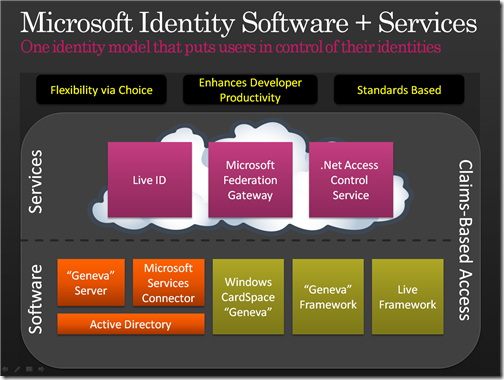
Many words will be spent about those products, singularly and as a whole. After all, a lot of people waited a long time for this moment: I know I did. I can't tell you the joy of seeing this coming together so nicely in the last months! Here I'll just give you a short vademecum the various products and services we unveiled last week during PDC, without going too much in details. As you go through my little tourist guide, always remember my disclaimer. However in the interest of clarity, in case somebody would be confused by my little landscaping stunt up there ("omg he's out of control"), below you can find the official slide that was included in each and every identity session @ PDC and shows the breadth of our identity S+S portfolio.
All of those technologies were described in Kim's & your truly's session, and they all had a role in the big demo in the same session.
"Geneva" Server
Ah, if I'd have a coin for every time I've heard conjectures about Microsoft eventually coming out with an "STS product", whatever flavor people gave to the term at the moment, I'd need a much bigger piggy and I'd sprout my very own ferromagnetic-enhanced field.
Here, we've done it! Happy now? :-) And what a product we have in our hands! "Geneva" Server is a shrink-wrapped server product which picks up the torch from ADFS and brings to your environment all the capabilities you need for taking full advantage of the claims based access approach. A partial list of the things you get:
- WS-Trust, WS-Federation and SAML-P support
- Full integration with AD, both as authentication and attributes store (but the two concepts are kept separated!)
- All the management goodness you expect from a server product: MMC, WMI, events...
- Proxy for extranet/edge access
- CardSpace support: STS endpoints, card issuance, the works
We've gone a long way since SimpleSTS.cs, didn't we. You don't have to write a single line of code for using geneva server: you can literally point&click your way through federation relationships creation & management, in fact I'm expecting my ITPro colleagues to play with it way more than I'll personally do. I'll tell you a secret, come closer: with Geneva Server finally available, you should think twice before deciding to write a custom STS. Per the 80-20 rule, I'd expect the vast majority of cases to be addressable by the server: and you get all the scalability/manageability goodness that derives from a team dedicated to deliver a quality server product. Trust me, you don't want to reinvent that wheel unless you are really forced to.
The entry point for all things Geneva is https://www.microsoft.com/geneva (one URL you can actually remember!), closely followed by the connect site; however, as you'll see below, Geneva is more than just the Server. Some specific links are the server overview, a getting started, how-to guides, the step by step guide, and of course the downloads (x86 and x64). Stuart and Caleb gave a great overview in their PDC session.
"Geneva" Framework
This is not really a new entry; rather, it's friend that moved from the town to the city. That's right, Geneva Framework is the new name (and the new build) of Zermatt. The new beta has a lot of improvements: I am especially fond of the new pipeline, the improved support for the ActAs scenarios, and the exceptional new service that can automagically turn your WS-Security tokens into windows tokens! As you heard at PDC, Geneva Server is literally built with the Geneva Framework: what better testament to our commitment to produce an awesome API than this?
You can expect really a lot of reference material that will help you to develop with the Geneva framework. Apart from all the excellent documents available at release time (Keith's revamped paper, David Chappell's paper, the super-useful change matrix, Jan's PDC session) and the renown URI-addressable forum, the Geneva team is starting to blog! Since the URI is the same as the former CardSpace blog, I am sure many of you already have it in the aggregator; if you don't, that's the moment to let go of any hesitation: those guys are writing the product, I expect their posts to be normative. Download the x86 version here; the x64 version is here.
Windows CardSpace "Geneva"
The long anticipated beta of the new version of CardSpace is here, and it lives under the Geneva umbrella too. Rich gave a great intro to it at PDC, and the team already blogged about it here. The most visible news you'll encounter are the new UI experience, the reduced size & streamlined install experience, and the snappy responsiveness that derive from the full rewrite in native code. You can download the x86 version here; the x64 bits are here.
Microsoft Federation Gateway
You know, from this pages I almost always describe the company I work for as a technology/platform provider (for lack of better term): for architect and developers Microsoft is the company who provides the technology (developer products, platform APIs, servers) for building their own solutions and services. But Microsoft can wear also a different hat, the one of the services provider. Some examples? Dynamics CRM Online. Exchange online. What if your company would like to take advantage of those? Think of what you'd do with any other business partner: you may decide to enter in a federation relationship. That would boil down to exchange some metadata addresses, and the federation products would work its magic. Well, with Microsoft it's not different. The Microsoft Federation Gateway is a service that you can use for gaining federated access to Microsoft services; that means that once the relationship is established, your employees can simply follow a link from your LAN and gain SSO access to CRM online or the service of your choice. Everything is done according to open standards (WS-Federation, WS-Trust) hence any directory software that is understands those standards is game: relationships can be easily self provisioned, as described in this exhaustive document.
Microsoft Services Connector
If you have Active Directory and you want to access Microsoft services, you could be 4 clicks or so away from making that wish a reality. The Microsoft Services Connector is a free tool that can help you to establish a federation between your AD and the Microsoft Federation Gateway by shielding you completely from the details you'd need to make available in case of direct self provisioned federation as described above. If you've seen PDC's Keynote 1, you've seen Dave Thompson giving it a swirl directly from stage; Lynn & Tore blogged about it and gave a great PDC presentation on the subject, and there's even a whitepaper for your reading pleasure. If you want to play with it, start at https://www.microsoft.com/servicesconnector/ (another URL you can remember! what's happening to us :-)) and download the CTP of the Microsoft Services Connector here. Ah, I was almost forgetting: about that "consistent company-wide approach" thinghy, the Microsoft Services Connector is built on Geneva technology :-)
Live Identity Services
Live Identity Services is the collective name of Microsoft's public identity provider functions. Jorgen gave an excellent session at PDC where he went in the details of the offering, but I am sure you all already heard about the new Live ID OpenID technical preview. It was covered everywhere! But of course, web auth, delegated auth and federation are great topics to explore too.
Live Services Framework
The Live Services Framework is the new SDK which gathers APIs and tools for simplifying development against live services, including the identity-related ones. If you want a big picture of the live framework, check out the coolest poster in town :-)
.NET Access Control Service
Here there's another old friend. The .NET Access Control service leverages WS-Trust, WS-Federation and claims transformation rules for covering the security needs of other .NET services and, if you choose so, your applications as well. Justin gave 2 great talks about it at PDC (here and here), and the entry point for the official documentation is here (dev center intro here). If you want to explore it with a pretty original visual experience don't forget to download the Azure Services Training Kit and try the MMC!
Ah, did I mention that the .NET Access Control Service is built on Geneva technology, too? ;-)
That's it. I hope this will help you at least to stay on top of the naming as you drink from the fire hose. There are tons of links in the text above, and I fully expect to see more resources to become available in the next days/weeks/months. Among other things here and there, my humble contribution will be a series of posts where I break apart the big demo in its main parts, showing the details of how things come together.