XSSDetect: Tool for finding Cross Site Scripting bugs
About a month back, ACE Engineering released "XSSDetect", a stripped down version of the "Code Analysis Tool for .NET code bases (CAT.NET)".
A Cross site scripting (XSS) vulnerability exists in a web application whenever user controlled input, without proper validation or encoding is echoed back to the browser.
To find XSS (and other injection flaws) in an application, you need to enumerate all user input. User inputs can be through query string, form fields, cookies etc. Then you need to do a manual data flow analysis for each user input by reading through the code and by using the web site. The goal is to find all instances of user input that, without validation or encoding, are being echoed back to the browser. This may be if the input is assigned to a label control, or is used in a "Response.Write" statement etc. Without doubt this is a tedious process.
XSSDetect automates this process of finding XSS bugs. It has predefined sources of user input and then does a data flow analysis. If the input ends up in a predefined list of sinks that are vulnerable, it flags it as a XSS bug.
I wanted to give an idea of the sort of issues XSSDetect finds. For this, I ran the tool on a demo site that the ACE Security Team uses for its Secure Application Development/ Testing Training course.
1. Once you install XSSDetect, it is visible as a snap-in in the Visual Studio IDE.
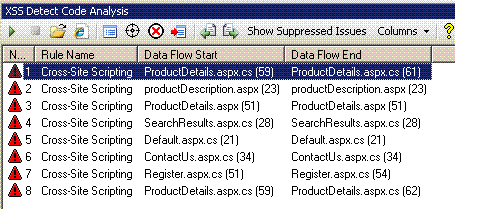
2. After loading the solution in Visual Studio and clicking on the green "GO" button, XSSDetect's analysis window shows the list of potential issues that it has found in the application.
3. Clicking on the issue, takes you to the source code where the issue exists.
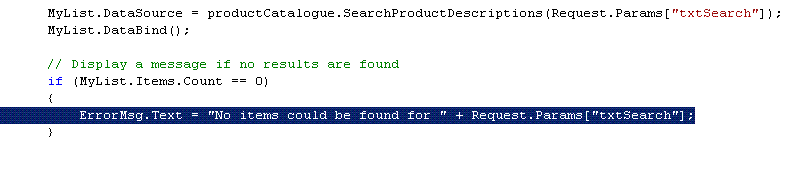
In this particular case, user controlled input, without validation is being assigned to a label control.
4.
Here the RegisterStartUpScript method is being used to add script. The script contains user controlled input which is again not validated or encoded.
5.
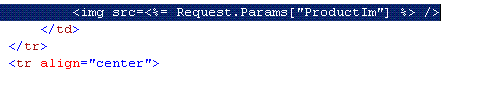
In this vulnerability, user controlled input is being directly assigned to an image "src" property through an embedded code block.
XSSDetect only finds non-persistent XSS. This is because it is a stripped down version of the CAT.NET tool. The CAT.NET tool, other than finding persistent XSS, also finds various other vulnerabilities like SQL injection, Redirection to user controlled site, exception details being shown to user, file canonicalization bugs, LDAP injection etc and has many more features including integration with MSBUILD and FxCop.
You can download XSSDetect from here.