Windows Azure Security Best Practices -- Part 1: The Challenges, Defense in Depth
 Every conversation I have with developers about moving their application to the cloud revolve around two main issues.
Every conversation I have with developers about moving their application to the cloud revolve around two main issues.
- One is business. What are the economies of scale around moving your app to the cloud?
- And close on its heals, come the questions around security. “How secure is the cloud, especially Windows Azure? What benefits does Windows Azure provide? What do I need to do to secure my application?”
And also, often unstated, “How do I make my user experience as easy as for users as it is for on-premise applications?”
As ISVs we want to provide authorized users, clients and systems access to the data they require at any time, from any technology, in any location, while meeting basic security requirements for confidentiality, availability and integrity.
And equally important, we want to keep bad guys from getting to this same data.
This is the first of several posts about the challenges in designing your software and what you can do in your software to insure access to those who should have access and prevent access those who do not.
The intent of this series is to provide a context for you to learn more and empower you to write great applications for the public cloud.
Threats
I’ll begin with a brief summary of the challenges. The threats to your application are in many ways, similar to the threats that you think of for on premises applications. However with on premises applications, some of the key points are mitigated because your application runs behind the firewall.
When moving to the Windows Azure cloud, the some of those threats are heightened, some reduced. And mitigating those threats becomes a deeper partnership than when you host your own application. When you host your application on your own servers, you control the physical access to the server, the operating system, the patching, how users access it, and more. And with that comes the added responsibility for maintaining the infrastructure, insuring backups are performed, load balancers are configured.
But when you partner with Microsoft, the Global Foundation Services team handles many customer requirements and is responsible for some of your application’s security.
In the same way you think of the differences between Infrastructure as a Service (IaaS) where you are responsible for the infrastructure and and Platform as a Service (PaaS) where you share the infrastructure with Microsoft.
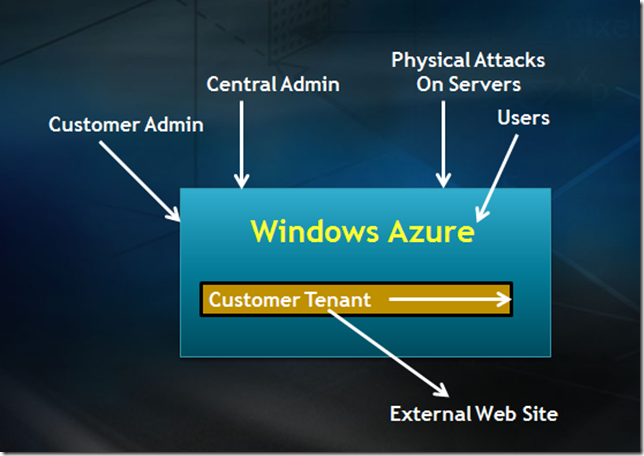
In either environment, you can think of seven vectors for attacks.
- Customer admin where you administer the application. How is your application deployed, updated, and data accessed? Who has access and how is that authenticated?
- Central administration of the hosting service. How, when, where, who has access and what monitors the hoster administrators?
- How do you physically access the server? Is it under a desk? Under armed guard? Who can touch the server and who has physical access to the devices?
- What can users access and how is data presented to those users? What are they authorized to see?
- How can a customer attack Windows Azure from inside an application? How can they jailbreak and compromize the system?
- And what happens when a customer uses Azure to attack other Web sites?
Traditional threats still exist, even though you are moving your application to the Cloud. For example, you’ll still need to consider cross site scripting attacks (XSS), code injection attacks. And providers need to account for DNS attacks, network flooding.
Some threats are expanded such as data privacy that you need to consider. You’ll need to be aware of the location of the data and segregation of data, especially in multi-tenant environments. You’ll also need to handed privileged access.
New threats are introduced by the nature of the cloud service provider. For example:
- New Privilege Escalation Attacks (VM to host or VM to VM)
- Jailbreaking the VM boundary
- Hyperjacking (rootkitting the host or VM)
And yet certain old threats are mitigated due to patching being automated and instances are moved to secure systems. In addition, cloud resiliency improves failover.
Through the next several posts in this series, I’ll describe what you can do to protect your data. And I’ll explain what Windows Azure provides. I’ll also provide the basic references that you can view for more details.
Defense in Depth
The Online Services Security and Compliance (OSSC) team manages the manages security for the Microsoft cloud infrastructure and is a part of the Global Foundation Services division. Securing The Microsoft Cloud shows how the coordinated and strategic application of people, processes, technologies, and experience results in continuous improvements to the security of the Microsoft cloud environment.
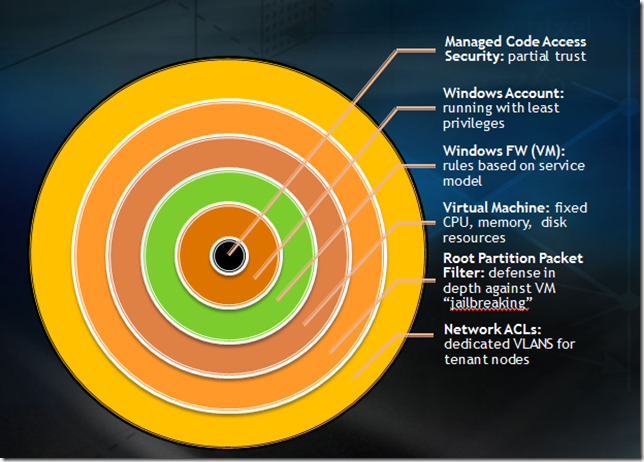
Having a defense-in-depth approach is a fundamental element in how Microsoft provides a trustworthy cloud infrastructure. Applying controls at multiple layers involves employing protection mechanisms, developing risk mitigation strategies, and being capable of responding to attacks when they occur.
Physical security
Use of technical systems to automate authorization for access and authentication for certain safeguards is one way that physical security has changed as security technology advances.
OSSC manages the physical security of all of Microsoft’s data centers, which is critical to keeping the facilities operational as well as to protecting customer data. Established, precise procedures in security design and operations are used in each facility. Microsoft ensures the establishment of outer and inner perimeters with increasing controls through each perimeter layer.
Data Security
Microsoft applies many layers of security as appropriate to data center devices and network connections. For example, security controls are used on both the control and management planes. Specialized hardware such as load balancers, firewalls, and intrusion prevention devices, is in place to manage volume-based denial of service (DoS) attacks. The network management teams apply tiered access control lists (ACLs) to segmented virtual local area networks (VLANs) and applications as needed. Through network hardware, Microsoft uses application gateway functions to perform deep packet inspection and take actions such as sending alerts based on—or blocking—suspicious network traffic.
A globally redundant internal and external DNS infrastructure is in place for the Microsoft cloud environment. Redundancy provides for fault tolerance and is achieved through clustering of DNS servers.
Identity and Access Management
Microsoft uses a need-to-know and least-privilege model to manage access to assets. Where feasible, role-based access controls are used to allocate logical access to specific job functions or areas of responsibility, rather than to an individual. These policies dictate that access that has not been explicitly granted by the asset owner based upon an identified business requirement is denied by default.
Application Security
The rigorous security practices employed by development teams at Microsoft were formalized into a process called the Security Development Lifecycle (SDL) in 2004.
References
Learn more at Global Foundation Services Online Security. The Global Foundation Services team delivers trustworthy, available online services that create a competitive advantage for you and for Microsoft’s Windows Azure.
Next Up
In Windows Azure Security Best Practices -- Part 2: What Azure Provides Out-of-the-Box. I explain that security with Windows Azure is a shared responsibility, and Windows Azure provides your application with security features that go beyond those that you need to consider in your on premises application. But then, it also exposes other vulnerabilities that you should consider. In addition, I’ll explore the compliance.
In other upcoming parts, I’ll describe the steps you can take to embrace security in your overall application design, development, and deployment.
Here are links to the articles in this series:
- Windows Azure Security Best Practices -- Part 2: What Azure Provides Out-of-the-Box.
- Windows Azure Security Best Practices – Part 3: Identifying Your Security Frame.
- Windows Azure Security Best Practices – Part 4: What Else You Need to Do.
- Windows Azure Security Best Practices – Part 5: Claims-Based Identity, Single Sign On.
- Windows Azure Security Best Practices – Part 6: How Azure Services Extends Your App Security.
- Windows Azure Security Best Practices – Part 7: Tips, Tools, Coding Best Practices.
Bruce D. KyleISV Architect Evangelist | Microsoft Corporation
Special thanks to the Global Foundation Services team for the content in this post.