Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Sometimes unlike post 2, you may not know where to start, but hopefully you know some piece of data to search on.
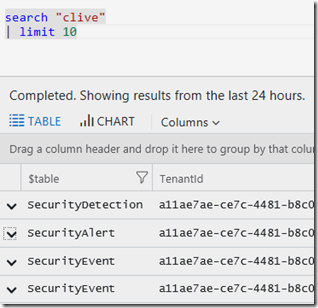
An example I often use is a persons name, I’ll use my own. Search can look through a lot of data so you may want to scope the time to a period you think is likely. This is a great use of the search operator.
Tip – please note using search is not efficient, and you should switch as soon as possible to the right data Type, like I show at the end of this page.
Now that I have some records, I can refine the query, by opening one of the rows I can visually see ‘clive’ in AlertName and Displayname 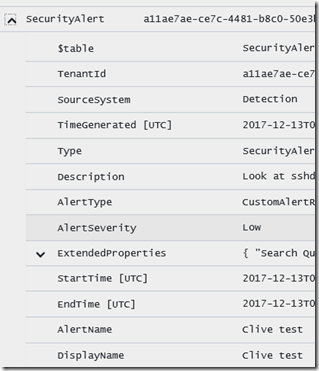
I may also have looked to see where ‘clive appears in each data type. This query using summarize shows ‘clive’ appears most often in SecurityEvent.
Question :Why am I appearing in so many Security Events? 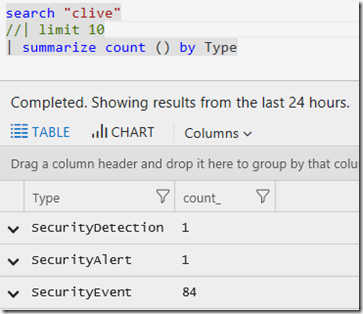
So I can now flip the syntax to just look in the SecurityEvent table (again reducing the query time and getting us focussed).
SecurityEvent
| search "clive"
| limit 10
When I open a row, I see ‘clive’ in the TargetUserName
So I can now do be more specific and drop the search (to make the query more efficient, faster – and this uses less CPU for the backend Log Analytics system) :
SecurityEvent
| where TargetUserName == "CLIVE"
| limit 10
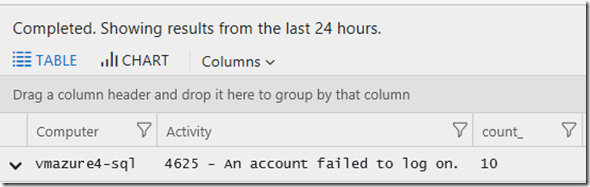
In this case I also wanted to see what Computer was involved, so I added a summarise, now I have a list just computers and the count of times ‘clive’ was found.
SecurityEvent
| where TargetUserName == "CLIVE"
| limit 10
| summarize count () by Computer, Activity
Answer: So this is why I’m in the SecurityEvent table so often, “EventID: 4625 – An Account Failed to log on.” 10 times (if I remove the limit its actually 84 times).