Ask Learn
Preview
Ask Learn is an AI assistant that can answer questions, clarify concepts, and define terms using trusted Microsoft documentation.
Please sign in to use Ask Learn.
Sign inThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this series so far, we've seen how email authentication is a great thing at stopping phishing under some circumstances, and where it isn't that useful in other circumstances. A circumstance where it isn't that useful is a variant of Business Email Compromise (BEC) that we call an Impersonation Attack. An Impersonation Attack is when the phisher uses a visual display trick and makes you think that who you are communicating with is a person that you know, but in reality is not that person.
You may think "That's what Business Email Compromise is" and you're right, but those can be further classified into Exact-Domain attacks (where the sender and recipient domain is the same), or Springboard attacks (where the sender and recipient have a relationship, but the sender domain is spoofed).
An Impersonation Attack is more general and makes use of many different techniques to fool the user:
But, what sets them apart is that the sending domain is not being spoofed.
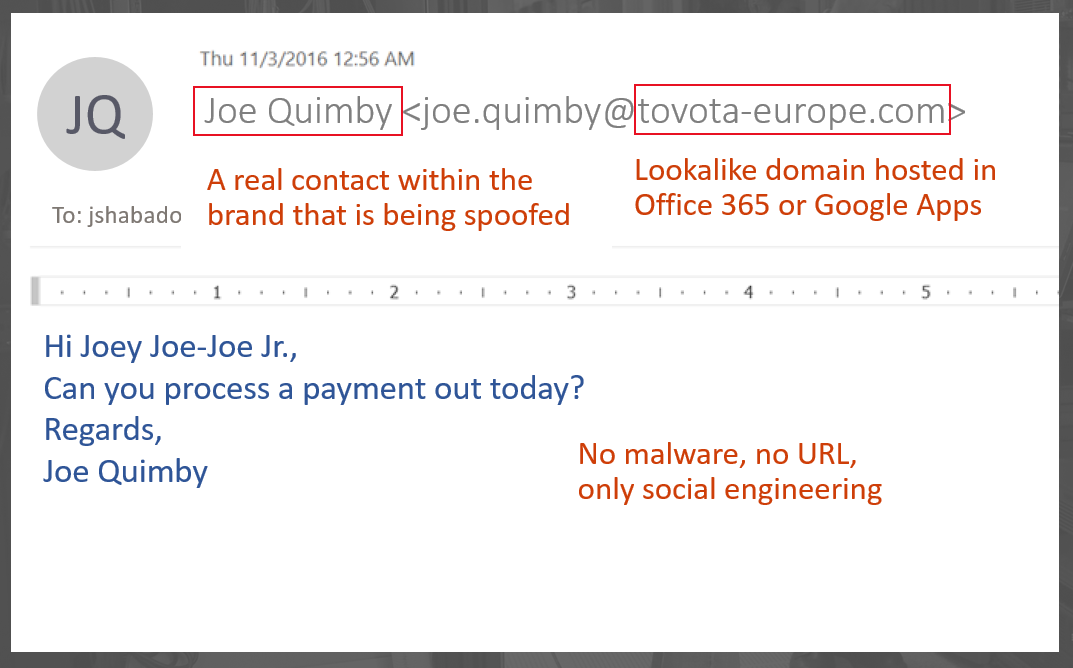
For example:
In this above example:
The key point is #1 and #2. The phisher has registered this domain for the intent of sending phishing messages, and they have even set up SPF records for the domain. Using email authentication to detect this as a spoof will fail, because it is not spoofing the domain; instead, it is spoofing the brand by using a heuristic that is easy for humans to interpret (and be fooled by), but hard for machines to interpret meaningfully. The filters do not have a lot of content to pick up, and the sending infrastructure is legitimate.
The Impersonation Attack is one of the more difficult phishing attacks to defend against.
.
Stopping Impersonation Attacks with techniques other than email authentication
Disclaimer: As I say in other blog posts where we haven't released the protection yet to the general public, this is me theorizing about how something could be done, not that it will be done this way.
One method that we are thinking about within Office 365 is leveraging Safety Tips to give users visual warnings when something in their email stream is out of place.
Edit 2016-01-12 - I've had to remove this part, will put it back later when we come up with something more concrete.
Conclusion
At this point, we've seen where email authentication is useful in the fight against phishing. However, we should not be lulled into a false sense of security that it solves all spoofing or phishing problems.
But what it does do is tighten up the perimeter so we can be more strict about enforcing security, forcing the cost of spamming to go up. That means the title of this post is incorrect; while email authentication falls flat when fighting Impersonation attacks, what it can do is drive a wedge into unauthenticated email and force phishers and spammers into places where they can be identified instead of hiding behind a mask.
There is no such thing as perfect security, only defense-in-depth. We use email authentication to protect ourselves, protect others from us being spoofed, and then add in other pieces of technology to stop the rest.
Ask Learn is an AI assistant that can answer questions, clarify concepts, and define terms using trusted Microsoft documentation.
Please sign in to use Ask Learn.
Sign in