Ask Learn
Preview
Please sign in to use this experience.
Sign inThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
On this blog, I've written a lot about email authentication and preached its virtues. If you are a domain owner, you should definitely set up SPF, DKIM, and DMARC records both so that emails to you can be identified between authentic and not, and so that other email receivers (e.g., Gmail, Hotmail/Outlook.com, Comcast, etc.) can identify which ones are legitimate and which are not.
If you're an Office 365 customer, you can find out what you need to do here:
If you don't have them set up, we still protect your domain from Exact-Domain spoofing, as I talk about here: https://aka.ms/AntispoofingInOffice365 (this is sometimes referred to as Business Email Compromise, or BEC, but I find that too broad a term and instead call it Exact-Domain spoofing because that's the technique that is used).
But that's not the only type of phishing that we see.
.
IT Phish Example 1
Where email authentication struggles is with a phishing scam that looks like the following:
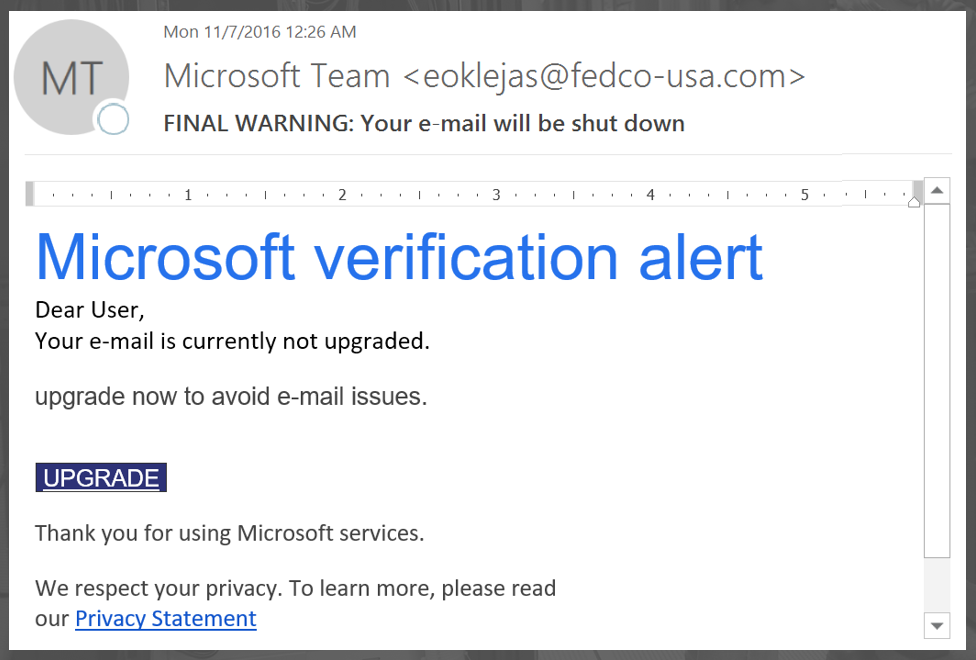
We refer to this as an IT phish, that is, a phishing message that looks like it came from your IT department. In the case above, the phisher is impersonating Microsoft and asking the user to click on a malicious link to avoid service interruptions. It's worded a little weird, but you're probably not reading it too closely before you click on the link.
Let's break down what makes it so difficult to detect:
All those features combine to make this message difficult to detect using standard antiphishing techniques, but still troublesome to the end user. These usually aren't spear phishing attacks, but instead the spammer or phisher is trying to either install malware on the end user's system when they click on the link (by executing a drive-by download, or downloading another piece of malware locally and hoping the user executes it), or by tossing up a phishing page and tricking the user into entering their user credentials.
.
IT Phish Example 2
The next example is just as insidious, yet no less difficult to catch. It, too, looks like an IT phishing message coming from Microsoft.
It is using similarly techniques to the first message:
These are two real life examples of phishing messages impersonating Microsoft brands. However, phishers will also impersonate your IT department. For example, if you are a university or a corporation, a phisher will impersonate your brand in the Display Name, and in the body of the message, in an attempt to get your students or employees to reset their passwords (but instead they get compromised). Even though the domain name in the From: address doesn't match your organization at all, users will still click. When the domain is off by a little bit, users will be fooled a little more often... and will click.
.
Stopping this type of phishing
With all the news this year about Business Email Compromise, the above examples are actually a return to traditional phishing. While spear phishing is all about targeting specific individuals, "traditional" IT phishing is about getting inside the organization for the purpose of spreading more phish or malware. Sometimes this is done to build up a botnet, but other times it's designed to be used as a springboard attack - send malicious content from the inside because it's less likely to be filtered when it originate inside the house. A phisher can also send true Business Email Compromise from a real account, rather than by impersonating one.
In terms of stopping this type of phishing, two years ago I wrote a blog post Why does spam and phishing get through Office 365, and what can be done about it?
The four things I said that you, as a customer, can do are still accurate (see that blog post for more details):
I then listed a series of features that we were working on, all of which have been completed (and then some).
However, as we've seen these types of attacks increase, over the past 6 months we've gone back and have been working on several new features to combat phishing. We still do everything I've talked about in previous blog posts, but we will be doing more.
I will not be discussing what this "more" is in great detail other than to make vague, hand-wavy motions and say it involves machine-learning, sender reputation, and big data. The reason for being so fuzzy is because phishers are constantly probing our system, trying to reverse engineer how things work. I am not going to make their job easier, and my job is hard enough.
Plus, by using industry buzz words, it makes it look more impressive.
But, as I said in my blog post about Safety Tips, you'll know when we detect phishing because we'll insert a red (Suspicious) Safety Tip:
That way, if any of your users ever start browsing through their junk email folders or spam quarantines, they'll be given an extra visual cue that the message really is malicious.
Conclusion
So, that's one of the types of phishing scams we're seeing (and you are, too). We're aware of it and are hard at work coming up with a solution.
Let me know in the comments what else you're seeing, I do plan on writing a couple more blog posts on what other sorts of phishing is common beyond Exact-Domain spoofing.
Previous: Antispoofing in Office 365
Please sign in to use this experience.
Sign in