Designing secure data transfer
As I have mentioned before on this blog, I’m currently designing an iPad app and I want to build it with security in mind. Even though I don’t think I’ll be a hacking target (not enough money in it for them, and I suck at marketing), I still want to make sure that it’s secure. I can then use myself as a model for everyone else.
My app is distributed to tablets with preloaded content. However, the strength of the app is the ability for me to upload additional content which users then pay for (or a portion thereof) if they decide to download it. But how do I distribute this data securely?
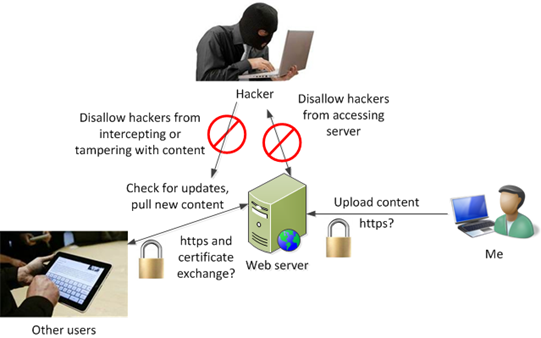
From my perspective there are three key things:
- I want to allow legitimate users to download content.
- I want to disallow hackers from stealing content when the content is in transit (a man-in-the-middle attack).
- I want to disallow hackers from calling into the server back home and pretending to be a legitimate user.
Below is what I was thinking originally:
But how can I accomplish this?
My solution is to use encryption – even if the hacker intercepts the data it is useless to him. And in order to download the data, the app has to identify itself as legitimate, or do something only a legitimate application would or could do. For the past 48 hours, I have been pondering two models:
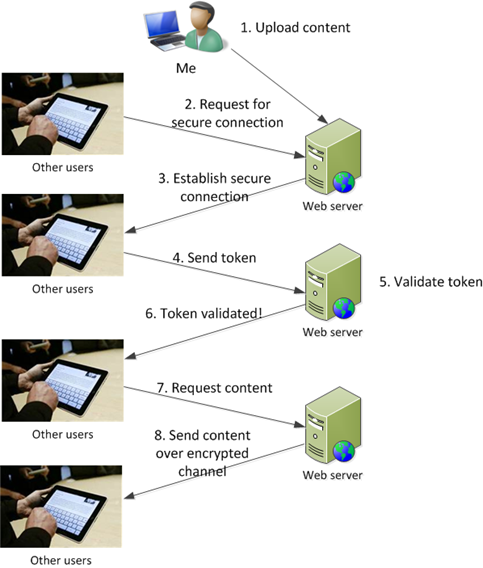
Model 1 – Transfer the data over an encrypted connection (such as SSL) and make the application identify itself
This architecture prevents a hacker from stealing the data in transit, and it also makes the user identify itself with a token that I would distribute as part of the application. Since the code isn’t public, a hacker would have to steal the code in order to reverse engineer it and present the token.
To do this option:
- I have to get a certificate so I can set up SSL.
- I have to create a cryptographic token using a 128-bit or 256-bit key and AES encryption (I want a symmetric encryption algorithm).
- I have to distribute that token with the app.
- I have to tell the web server to look for that token after the SSL connection has been established.
That’s option 1.
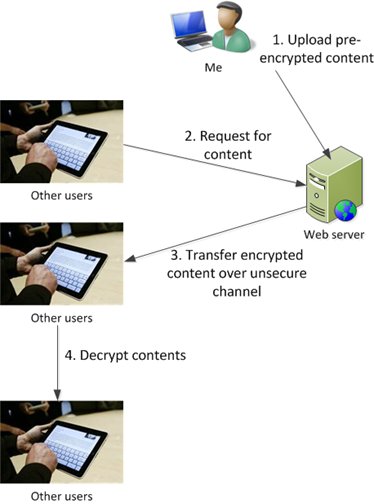
Model 2 – Pre-encrypt the data and transfer it over an unsecured connection and then decrypt it on the tablet
This architecture doesn’t care if the hacker intercepts the data in transmit or impersonates a real device. Since the data is encrypted, and since only the web server and the tablet device know the secret key, only real users can decrypt the data. The hacker would have to acquire or reverse engineer the code in order to use it, and if they can do that, I’ve got bigger problems.
To implement this option:
- I have to pre-encrypt the data every time I upload it to the server.
- I have to ensure that the app has the decryption key. I chose a symmetric encryption algorithm over an asymmetric one for performance reasons, and that’s why I chose a symmetric algorithm in Model 1 – to keep things the same during the design phase.
This option is simpler than the first one.
Which one should I go with?
I’m having a very hard time deciding. I’ve talked to people and technically speaking, there is no real advantage to doing it either way. They both encrypt the data. But there are other advantages with one model over the other:
Security – Both are pretty much the same at protecting the data (I know that there are other possible threats but that’s out-of-scope for this post).
Bandwidth – Model 1 (SSL) uses up more bandwidth because it first has to negotiate the SSL certificate and is slower to set up. Model 2 would be faster for the end user.
Simplicity – For data transfer, Model 2 is easier to set up. Just toss up a web server vs. toss up a web server and pay $70/year for the SSL with Model 1.
Maintenance – This is the tipping point. With Model 1, I set up the SSL connection and let it do its thing. Whenever I want to upload new content, I just upload it. I can concentrate on creating new content.
With Model 2, I have to always remember to pre-encrypt the data. I need to write a tool to do that. That also means that I have to design a protocol to decrypt the data on the tablet side.
Do I trust my coding ability that much to write that tool? I like to design and I can write scripts, but this is going to the general public. I’m not that skilled a programmer and I’m worried about quality. And, right now, I’m way behind in generating the content for the app (I should be writing content, not writing this blog post). I just don’t have the time to design a file-encryption-and-unpacking algorithm.
I already need to write a tool to ensure that every time I create new content it conforms to the format that it has to be in (file naming structure, xml structure, descriptions of contents, etc). Tossing this extra stuff on my plate is too much.
For that reason, I am selecting Model 1.
That’s my Secure Data Transfer model and why I am selecting it. If you have any suggestions, feel free to leave them in the comments.