The new breed of spam
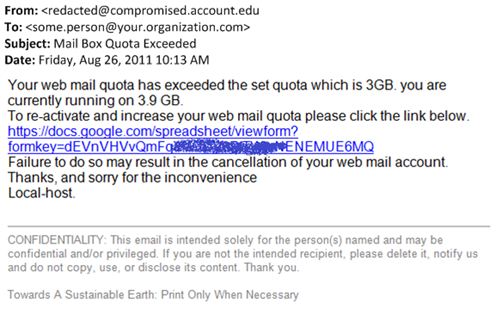
I came across the following spam message today. It was sent through a compromised account, and the payload points to a compromised Google Docs spreadsheet (hey, Google, you know spammers are going after that service, right?). Below is a screenshot image:
Peeling apart the message:
- This is resistant to IP filtering because the message comes from a hacked user’s account (the majority of mail from the IP is legitimate but “only” this user is sending spam; therefore, blocking with IP reputation would cause excessive false positives).
- This is resistant to generic URL filtering because the payload points at Google Docs, the overwhelming majority of which are legitimate (filtering on the specific link is acceptable although most URL checkers only go for the top level domain).
This illustrates what I said in my other post, that spammers now use botnets to hack user accounts and hack legitimate services and hide behind them in order to spam. They are spamming by proxy.
On the other hand, this technique isn’t that new. I remember back in the day, when image spam first hit, spammers would send spam from Hotmail accounts they signed up for themselves and send image spam hosted on Imageshack or point to a domain hosted on Geocities. Whatever the technique, these types of messages are still blocked the old fashioned way: using content filtering on the body of the message.
Sometimes the old methods are best.