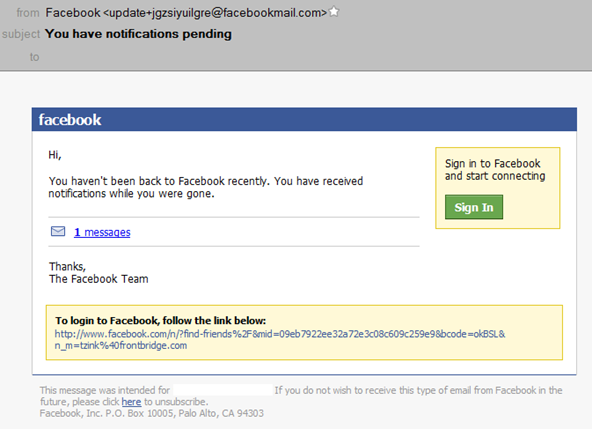
Latest Facebook scam
This past week I got a message from a spammer who was spoofing Facebook. I didn’t notice this message until this past week because our spam filters caught it and delivered it to my spam quarantine. I find that these days I don’t have the insight into new spam campaigns that I used to have because our filters are pretty good at pro-actively catching these types of malicious spoofing campaigns and I just don’t see them. I look at my quarantine reports sometimes to see how much spam I get, and only then do I notice “Oh, here’s a new one from Facebook”. Anyhow, the contents of this one is below:
The message looks pretty legitimate except that it is completely untrue that i haven’t been back to Facebook recently. The link is a link to a pharmacy spam site (or potentially one serving up a drive-by download, I didn’t bother clicking on it but it looks like pharmaspam). Anyhow, here’s an analysis of the spam message:
The URL points to a site that was registered on July 30, 2010 using eNom, Inc. The contact information is listed as a guy living in Irkutsk, Russia.
The A-record of the site is not resolveable indicating that the site has already been taken down. That’s too bad, I would have liked to have seen where it is hosted.
The IP that sent the message belongs to a web hosting service in Brazil (locaweb.com.br).
The message goes to a bit of trouble to make it look like it was sent and originated out from Facebook’s local mail servers. It started from an IP in the 10.x.x.x local IP space before being received by mta026.snc1.facebook.com. This, of course, is a spoofed header.
The message uses one of Facebook’s update email aliases - update+<random letters>.
The message avoids SPF checks by sending from a Return-Path of fh-luh.de. This has no TXT record and if you go to the site, it redirects to the University of Applied Sciences in western Germany. Thus, what the spammer has done is avoided an SPF check while attempting to make his message look like it is from Facebook to the end user since the P2 From is what is shown to the end user. A SenderID check would detect this, however.
So, while this message does have an element of smooth sophistication to it (evading some spam filters, trying to give itself a look of legitimacy, correct grammar, spoofed headers) there really isn’t anything new here. It’s one of the same old tricks we have seen before, spoofing and social engineering.