More details on the Google cyberattack
The New York times has some more details on the Chinese cyberattack that hit Google back in January, prompting Google to threaten to withdraw from China and eventually redirect all traffic to google.cn to google.com.hk. Below are some excerpts:
Ever since Google disclosed in January that Internet intruders had stolen information from its computers, the exact nature and extent of the theft has been a closely guarded company secret. But a person with direct knowledge of the investigation now says that the losses included one of Google’s crown jewels, a password system that controls access by millions of users worldwide to almost all of the company’s Web services, including e-mail and business applications.
The program, code named Gaia for the Greek goddess of the earth, was attacked in a lightning raid taking less than two days last December, the person said. Described publicly only once at a technical conference four years ago, the software is intended to enable users and employees to sign in with their password just once to operate a range of services.
The theft began with an instant message sent to a Google employee in China who was using Microsoft’s Messenger program, according to the person with knowledge of the internal inquiry, who spoke on the condition that he not be identified.
By clicking on a link and connecting to a “poisoned” Web site, the employee inadvertently permitted the intruders to gain access to his (or her) personal computer and then to the computers of a critical group of software developers at Google’s headquarters in Mountain View, Calif. Ultimately, the intruders were able to gain control of a software repository used by the development team.
In Google’s case, the intruders seemed to have precise intelligence about the names of the Gaia software developers, and they first tried to access their work computers and then used a set of sophisticated techniques to gain access to the repositories where the source code for the program was stored.
They then transferred the stolen software to computers owned by Rackspace, a Texas company that offers Web-hosting services, which had no knowledge of the transaction. It is not known where the software was sent from there. The intruders had access to an internal Google corporate directory known as Moma, which holds information about the work activities of each Google employee, and they may have used it to find specific employees.
It’s still not quite clear what exactly happened but more details are now coming to the surface. I don’t know exactly what role Gaia plays but what I can tell, here is what happened:
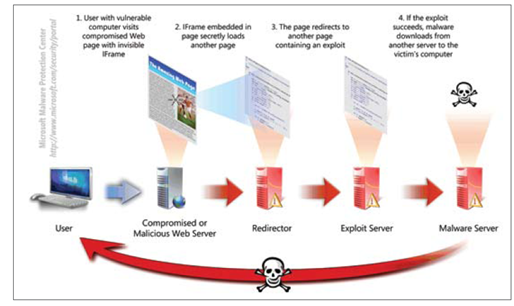
A Chinese Google employee was using Live Messenger and a hacker sent him a message with a link to a web page with a drive-by download. A drive-by download is a web page that hosts malicious content and automatically takes advantages of vulnerabilities in a browser.
This employee clicked the link in the Messenger program, launching his web browser. It went to the link and the malicious web page started to execute.
The malicious web page took advantage of the security flaw and exploited another vulnerability in Gaia, Google’s Single Sign-On solution (I would assume that Gaia helps manage access to Gmail, YouTube, Blogspot, and other Google apps).
The intruders then gained access to some of Gaia’s/Google’s internal workings and, indeed, once they got this access they were able to impersonate the real Google employee and use his credentials to poke around. They obtained access to Google’s internal employee database of activities and were able to figure what they wanted.
Poking around, the intruders gained access to some source code and copied it to servers in Rackscape, in Texas. Why they would do this is unclear, but one answer is that they wanted to go with a hosting provider and “hide” within another cloud service. In other words, they didn’t go with their own servers right away to prevent being back-traced. They then would have pulled the software off of these servers and passed them along to their intended destination (or perhaps another intermediate hop).
To me, this is indicative of a targeted attack. It is not something that would have occurred off-the-cuff, but resembles a more sophisticated operation. It would have required pre-operational work including surveillance of the targeted employees. They also would have had to figure out a security hole in the Gaia software, as well as the web browser. This implies that they were working on it well ahead of time and didn’t reveal it beforehand such that maintainers of the web browser could have issued a security patch. Once inside, they moved around really quickly and seem to have had some familiarity with internal workings of Google, which suggests that they may have had some prior exposure previously and retained the information. Finally, they covered their tracks by pushing the software to Rackspace so as not to directly leave a trail back to themselves.
If my analysis is correct, this is not the work of an amateur but instead of a professional hacking operation. Whether or not there was state sponsorship behind it is up for debate.