What do my stats say on Waledac’s takedown?
In my previous post, I wrote that other security researchers didn’t find much impact after Microsoft obtained a court order to take down 270+ domains associated with the waledac botnet. What do my own statistics say?
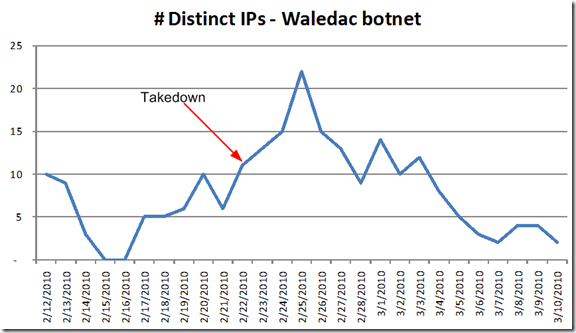
Waledac is one of the smaller botnets that send us spam traffic; but since we are enterprise mail while Hotmail is consumer, the attack vectors may be quite different. Anyhow, here’s how many distinct IPs we were seeing in the month of February before and afterwards:
Going by this, we didn’t really see much difference either. Waledac kind of bounced around before and afterwards with no real drop off in uniqueness. I then decided to compare the rest of the botnets I track and none of the other ones showed any distinguishing feature either.
Except for one.
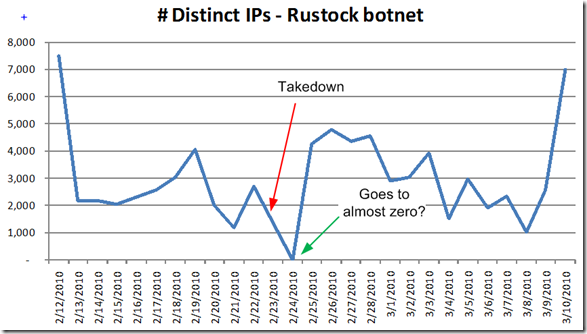
While this may be an anomaly or a reporting error in my script, the rustock botnet was affected for a short period of time following waledac’s disruption. A day after the takedown, the amount of mail it sends us went to almost zero:
You can see that it kind of oscillates around but it never gets lower than a thousand. Yet on Feb 23 (don’t let the date on the chart fool you, Excel is being weird for some reason), the amount of post-RBL spam that we get from rustock nearly disappeared. That has never happened before, rustock may fluctuate within a range but it never disappears. Admittedly, this could simply be a reporting error in my script. We have had other problems that seem to have arisen around Feb 22 for some strange reason. The problem is that none of the other botnets that I track show this odd behavior of nearly vanishing after waledac was taken offline. So, there are some possibilities here:
My data is valid. If so, then that means that there is a link between rustock and waledac. Perhaps rustock uses the waledac domains to spam, not waledac itself. Rustock also recovered quickly so perhaps waledac also recovered quickly, or else rustock has a robust infrastructure and is self-healing.
My data is invalid. I have a reporting error in my script, or some of our logs didn’t rotate, or perhaps the list of IPs didn’t download properly. I grant this as a possibility but then it means that the rustock reporting is an anomaly, or I need to revisit my other data.
Indeed, if it is point 1 then we have established a relationship between the two botnets.
Update: Upon further investigation, I discovered that my script had a reporting problem on Feb 23. It turns out that another set of numbers that I track demonstrate that every other botnet had similar disruptions in their total patterns, not just rustock. As it turns out, it was too good to be true.
That means that my data is invalid, and all I have been able to confirm is that the waledac botnet take down a couple of weeks ago doesn't appear to have made much of an impact.