FireEye knocks Mega-d offline
From the Register:
A botnet that was once responsible for an estimated third of the world's spam has been knocked out of commission thanks to researchers from security firm FireEye.
After carefully analyzing the machinations of the massive botnet, alternately known as Mega-D and Ozdok, the FireEye employees last week launched a coordinated blitz on dozens of its command and control channels. The channels were used to send new spamming instructions to the legions of zombie machines that make up the network.
Almost immediately, the spam stopped, according to M86 Security blog. Last year, the email security firm estimated the botnet was the leading source of spam until some of its servers were disabled.
…
The takedown effort is significant because it shows that a relatively small company can defeat a for-profit network that took extraordinary measures to ensure it remained operational. Not only did Ozdok reserve a long list of domain names as command and control channels, it also used hard-coded DNS servers. When all else failed, its software was able to dynamically generate new domain names on the fly.
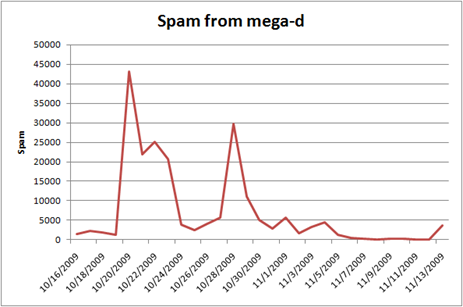
I decided to check this using our own statistics. While I don’t know if Mega-D was at one time responsible for 1/3 of all spam (my stats only go back to late July 2009), it certainly isn’t one of the big ones today. Those slots are reserved for Rustock, Bagle-cb, Cutwail, and sometimes DarkMailer. However, Mega-d certainly does register (no pun intended) on our radar. Below are the stats:
You can see that Mega-d does have a sawtooth-like sending pattern, but we definitely saw a big drop in spam from that botnet that appears to be generating a bit of a recovery today (11/13/2009). Also note that the numbers on the y-axis are not necessarily representative of the full set of spam we see from Mega-d but the general trend is representative.
The good news in all of this is yes, a relatively small company can make an impact into a major spam operation. The bad news is that these takedowns tend to be short lived. Earlier this year, when a Latvian ISP was disconnected due to its abusive practices, it made only a small dent in global spam volumes, and this small dent vanished a few days later. The spam operation is becoming more resilient to disruptions in its service.