Microsoft’s Security and Intelligence Report, v7, now available
Every 6 months or so, Microsoft releases its Security and Intelligence Report for the previous 6 months of the year. SIRv7 is now available here. This is a very comprehensive document covering topics from the entire threat landscape that Microsoft is involved with combating. This year’s report contains three key messages:
The redistribution of knowledge – Microsoft’s level of security intelligence will be unmatched and provided to individuals and organizations to help them make better security decisions.
OK, so what else is new? – The SIR contains the information that is relevant to people right now.
What do I do now? - The SIR allows people to assess where they are and what action they need to take.
I thought I would post an excerpt from the Executive Foreword. I think that this highlights the theme of this current SIR.
Welcome to the seventh installment of Microsoft’s Security Intelligence Report, which I hope you will find is the most extensive and comprehensive edition to date. The cover story in this report looks back at the major threats that have attacked customers over the last 10 years, and then the report drills deeply into the current threats that you need to understand and includes what you can do to best manage your risks.
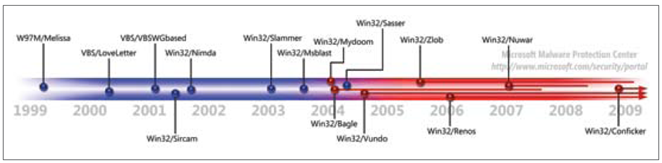
At Microsoft, we remember the pain past incidents caused our customers and we reflect on them frequently. In particular, the Slammer and Blaster attacks that disrupted the Internet in 2003 are vivid reminders of the responsibility we have at Microsoft to ensure our products are as secure and privacy enhanced as possible.
As you can see from the timeline above, 2003 and 2004 were difficult times. [tzink note: see the report for a better image] But, you can also see that since then, major security incidents have become less and less frequent. From the data in this report, you’ll also note that the scope and impact of major events have changed, as well. For example, from the press surrounding the Conficker worm that has been attacking customers over the past year, it’s easy to conclude that Conficker is just as widespread and impactful as Slammer or Blaster—but in most respects, it hasn’t been. In 2003, Blaster became one of the most prevalent threats impacting home PC users. Six years later, Conficker didn’t even make the Top 10 list among this audience. I don’t want to minimize the pain that many of our customers experienced fighting Conficker, because, as you’ll read in the report, it was the top threat detected and cleaned in enterprises in the first half of 2009, but Conficker emerged in a much different software industry than Slammer and Blaster.
Indeed, the software industry has matured a great deal since the days of Slammer and Blaster. Since 2003, the software industry has improved its ability to mobilize and coordinate resources to fight threats… The Conficker Working Group (CWG) was founded earlier this year, establishing a new model for how the collective industry can work together to mitigate global threats.
The industry was able to proactively get ahead of Conficker by discovering the vulnerability before attackers could use it in widespread attacks. The Security Science team at Microsoft was able to find the MS08-067 vulnerability, which Conficker uses to propagate, and work with the Microsoft Security Response Center (MSRC) to release its update before attackers could use it for a Blaster-type attack. Our industry partners helped protect many customers from attack via the Microsoft Active Protections Program (MAPP). MAPP supplies Microsoft vulnerability information to security software partners prior to security update releases from Microsoft… This program enabled the majority of MAPP partners to provide protections to their customers for Conficker 24 hours after the MS08-067 security update was released. This meant that many customers were protected up to a week earlier than traditionally possible, and certainly much earlier than customers could obtain such defense-in-depth protections and threat mitigations in 2003.
With the vulnerability that Slammer exploited, many administrators didn’t know whether they needed to apply a security update or that it had to be applied manually. Today, customers are notified and protected much faster; multiple communications channels exist to help customers find and understand information on security vulnerabilities. Security advisories help draw attention to security issues as they unfold, and provide customers with critical information before security bulletins become available. Microsoft’s advanced notification service provides customers with an insight into the number and nature of security updates that Microsoft will be releasing each month so they can plan more effectively for the deployment of the updates. Security bulletins provide information on vulnerabilities, along with workarounds and mitigations.
…
The progress that the software industry has made to better protect systems and customers might be small consolation to the users of those 5 million systems that were infected with Conficker in the first half of 2009. Still, it is a significant step forward, given that more than 100 times as many systems were protected from Conficker. This is in stark contrast to the Slammer and Blaster attacks of 2003 where many, many more systems were infected. The industry will continue to work together to make the frequency, scale and scope of emerging threats as minimal as possible.
We thank you for your help and efforts to protect the ecosystem, and look forward to continuing to work with you to create a safer, more trusted Internet.
George Stathakopoulos
General Manager, Trustworthy Computing Security
Trustworthy Computing Group
More excerpts to come over the next few days highlighting global trends in the threat landscape.