The multinational nature of spam
I received a spam message the other day that went to my Junk Mail Folder. I decided to take a look at it and dissect it piece by piece. It really is amazing to see how spam crosses so many international borders and exploits so many different machines. Spammers have their own globally redundant infrastructure. Below are the headers with minimum munging:
Envelope From: <>
Received: from 97-115-21-35.ptld.qwest.net (97.115.21.35) by
TX2EHSMHS041.bigfish.com (10.9.99.141) with Microsoft SMTP
Server id 14.0.482.32; Tue, 29 Sep 2009 02:09:30 +0000
Received: from [142.95.50.140] (helo=arq)
by 97-115-21-35.ptld.qwest.net with smtp (Exim 4.62 (FreeBSD))
id 125419027064-0004WM-EZ; Mon, 28 Sep 2009 18:11:10 -0800
Message-ID: <002501ca40a9$a607a510$8e5f328c@Boscoarq>
From: Salome Fields <pagadala@something.com>
To: <tzink@example.org>
Subject: Hot chixs.Ponetnce.Blue-colored-tab.
Date: Mon, 28 Sep 2009 18:07:51 -0800
Content-Type: text/plain; format=flowed; charset="windows-1252";
reply-type=original
Content-Transfer-Encoding: quoted-printable
Here is your complimentary health supply.
https://lsjo.lawdingops.com/
Let’s look at everything here:
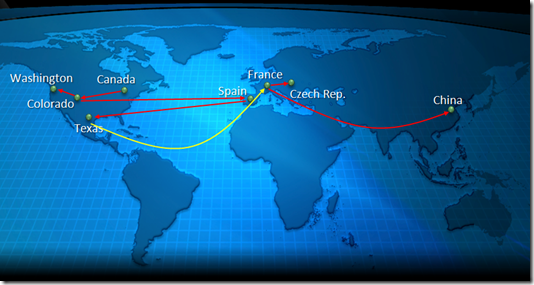
Assuming that we can trust this header, the spam originates on a system located in Ottawa, Canada (142.95.50.140), probably running Windows XP (as shown by the fact that it is encoded in Windows-1252).
That bot operating in Canada connects to a mail server running Exim, located in Denver, Colorado in the United States (97.115.21.35). This mail server is part of a botnet (different or the same, I don’t know) and sends spam to me. This IP has never sent us mail in the previous 7 months.
It is sending mail with a null sender which leads me to believe that this is either waledac or gheg. The other possibility is virus1 but the odds of that are considerably less. The spam is then sent to me where it reaches me via our data center in San Antonio.
The spam is pointing to a web page whose domain resolves to 156.35.89.137, which belongs to the ISP Universidad de Oviedo in Spain. I don’t read Spanish (I’m fluent in 6 million forms of communication but Spanish is not amongst them), but it looks like it’s a university (although I could be wrong).
While the IP belongs to a Spanish ISP, the domain is registered to a guy living in Arlington, Texas in the United States. I was quite surprised to see Whois information that looks legitimate, rather than it being anonymized. Alternatively, this information could be faked.
When I look up Whois the spammy domain on Internic’s page, I see that the registrar is ONLINE SAS which is a registrar located in France. One of the name servers is NS1.CN8.RU. The other is dns423545.communigal.net. Interestingly, GeekTool’s Whois page lists the other name server as ns2.alternativehealthpillsmeds.com.
Digging a bit deeper, let’s look at the first name server, ns1.cn8.ru. The domain, cn8.ru points to the IP 211.138.124.242 which is owned China Mobile Communications Corporation in Beijing, China. However, the name server ns1.cn8.ru points to the IP 193.165.209.3 which is owned by an ISP in the Czech Republic. So, the domain is running on an infected (?) machine in China while the name server is running on an infected machine in eastern Europe.
One thing of interest is that even though the name servers contain the Russian TLD .ru, neither the domain owner nor name servers are located in Russia.
So, going by this, here’s how it works: A malware author infects a machine in Canada (1) that relays spam to a machine in the United States (2), which contains payload that points to a machine in Spain (3) registered by a guy in the United States (4) using a registrar in France (5), which is resolved by a name server in the Czech Republic (6). That’s quite the multinational mechanism for transmitting spam, and I didn’t even dig through everything (there are multiple name servers and registrars I could have followed up on but didn’t).
Let’s count how many exploited machines there are here: the two that are involved in sending me spam plus the one where the web page is hosted is three. The guy in Texas is using name servers that look like they are located in Russia, but they are not. The one name server which resolves the spammy site is exploited (the one sitting in the Czech Republic) and then the top domain cn8.ru, sitting on a machine in China, is five. Since the the bot in Canada has to pull its instructions from somewhere, that makes 6. Whew, that’s a lot of infrastructure to maintain. This makes for a pretty fracking resilient system of sending spam.
I wonder if these guys have their own Operations department?