Real vs fake
Last week, I came across a phishing scam by a spammer who was attempting to impersonate Alliance and Leicester bank in the United Kingdom. I don’t normally call out banks specifically but I will in this case because of the bank’s poor security practices.
Here is the phish:
From: Alliance&Leicester plc [mailto:customer.care@alliance-leicester.co.uk]
Sent: Tuesday, August 11, 2009 11:49 PM
Subject: Alliance & Leicester Secure Messages Center
ONLINE BANKING INFORMATION UPGRADE
We are glad to inform you that our banking is switching to new
transaction The new Update technologies will ensure the secuirties of
your payment through our bank 1 new alert.The security upgrade will be effective immediately and requires our customers to update their access and Sign in Protection activation.
Alliance & Leicester Secure Messages Center For your security, you won't be able to gain access to your accounts until you've done this.
(Do not reply to this email. Alliance & Leicesterretains the right to send
you periodic updates on alerts and services).
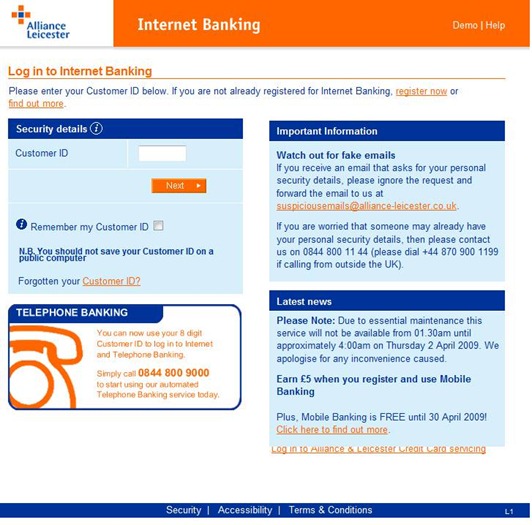
As you can see, I have removed the link to the site. Below is the phishing site:
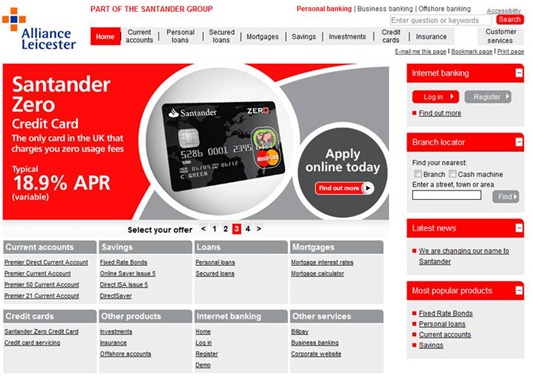
Compare this to the actual site:
They really don’t look similar at all. The first one does have some problems with it. The “Log in to Alliance & Leicester” link beneath the blue block is overrun by that blue block. Also note the text inconsistency:
Due to essential maintenance this service will not be available from 01.30am until approximately 4:00am on Thursday 2 April 2009. We apologies for any inconvenience caused.
I applaud the spammer for using the correct European date format (day-month-year) instead of the American one (month-day-year or possibly year-month-day). Still, look at what’s wrong:
- The first time (01.30am) has a leading zero while the second (4:00am) does not.
- The first time contains a period while the second contains a colon.
- Does anyone else find it odd that there is no space before the “am”?
- There is no comma after the word “Thursday”.
- The original phish email contained a typo in the word “securities.”
- The grammar in the first paragraph of the original phish is mangled.
One might expect that an actual Alliance & Leicester bank would have proper grammar. Of course, I said earlier in this post that I would take this bank to task, and I will. This bank has two things that they should fix:
They do not have SPF records set up – they aren’t soft fail or neutral, they are non-existent. Financial institutions must set these things up as a matter of best practice. Note that the spammer actually spoofed URL of the bank (alliance-leicester.co.uk).
The bank’s actual web page is http instead of https - They should switch this. The problem with calling this out is that not every bank/financial institution uses https as their landing page. Banks like Wachovia, Chase, Paypal (a pseudo-bank) and Wells Fargo use https at their landing pages. Royal Bank, UBS, Citibank and US Bank do not -- but they should.
While, er, I mean whilst, it is impossible to completely defend against phishers (the phisher could have used alliance-leicster.co.uk which looks visually similar and could easily trick people who are not watching closely), financial institutions should be making it as difficult as possible for them.