Preventing Cross-Site Scripting attacks using Microsoft Anti-XSS Security Runtime Engine!
Syed Aslam Basha here from the Information Security Tools team.
In the previous blog post I demonstrated “How to prevent Cross-site scripting attacks using Microsoft Anti-Cross Site Scripting Library V3.0 (Anti-XSS V3.0)”. Here am going to demonstrate “How to prevent Cross-Site scripting attacks using Microsoft Anti-XSS Security Runtime Engine”.
The Microsoft Anti-Cross Site Scripting Library V3.0 has two components
- Anti-XSS library
- Security Runtime Engine
The Security Runtime Engine (SRE) :
SRE is a http module. Each request which goes to website before rendering goes through this http module.
SRE protects applications from Cross-Site Scripting (XSS) attacks by leveraging the Anti-XSS library to encode data. It works by inspecting each control that is being reflected by asp.net and then automatically encodes data of vulnerable controls in their appropriate context. Data to be encoded for a specific controls is mentioned in “antixssmodule.config” file. This is useful for applications which are already deployed in production and we don’t want to rewrite code.
For example
1: using System;
2: public partial class _Default : System.Web.UI.Page
3: {
4: protected void Button1_Click(object sender, EventArgs e)
5: {
6: String Input = TextBox1.Text;
7:
8: //XSS
9: Label1.Text = Input;
10:
11: }
12: }
13:
Set ValidationRequest to false
1: <%@ Page Language="C#" AutoEventWireup="true" CodeFile="Default.aspx.cs" Inherits="_Default" ValidateRequest="false" %>
Run the above code in VS and enter <script>alert("Hello World")</script> in textbox, click on button. You will get “Hello World” alert box indicating your website is vulnerable to XSS.
You can prevent XSS using the SRE.
Steps to use SRE
- Create antixssmodule.config file using “ConfigGen.exe”
ConfigGen.exe is a Windows forms application used for generating the SRE configuration file. The utility works by comparing the controls present in your application's binaries with a master input file, encodingcontrols.xml. When it finds a match between a control in your application and a pattern in the encodingcontrols.xml file, it knows what kind of controls require encoding your application.
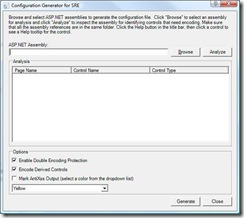
Enable Double Encoding Protection defends against double (re-)encoding of your output, and so possibly skewing your results.EncodeDerivedControls defines whether to encode controls which are derived from the classes found in the ControlEncodingContext nodes of the antixssmodule.config configuration file.
MarkAntiXSSOutput is a switch that controls whether source encoded through Anti-XSS is highlighted when displayed. The color dropdown list contains comprehensive list of colors that can be used for color coding the output.
Note:Do not use the MarkAntiXssOutput switch for applications which are in production.
-
Run ConfigGen.exe, browse and select application’s binaries, click on analyze and click on generate. It generates antixssmodule.config file save it in application path.
For the above example it generates the following:1: <?xml version="1.0" encoding="UTF-8" standalone="no"?> 2: <Configuration> 3: <ControlEncodingContexts> 4: <ControlEncodingContext FullClassName="System.Web.UI.WebControls.Label" PropertyName="Text" EncodingContext="Html" /> 5: <ControlEncodingContext FullClassName="System.Web.UI.Page" PropertyName="Title" EncodingContext="Html" /> 6: </ControlEncodingContexts> 7: <DoubleEncodingFilter Enabled="True" /> 8: <EncodeDerivedControls Enabled="True" /> 9: <MarkAntiXssOutput Enabled="True" Color="Yellow" /> 10: </Configuration>
- Copy SRE DLL’s to bin folder of your application
- Register SRE module in web.config of your application
In IIS 6.0 and IIS 7.0 in Classic .NET Application Pool
1: <system.web> 2: <httpModules> 3: <add name="AntiXssModule" type="Microsoft.Security.Application.SecurityRuntimeEngine.AntiXssModule"/> 4: </httpModules> 5: </system.web>In IIS 7.0 pipeline mode
1: <system.webServer> 2: <modules> 3: <add name="AntiXssModule" type="Microsoft.Security.Application.SecurityRuntimeEngine.AntiXssModule"/> 4: </modules> 5: </system.webServer>
- Re run the above example code snippet, the alert box will not appear.
You can refer to more articles on Anti-XSS here
-Syed Aslam Basha ( syedab@microsoft.com )
Microsoft Information Security Tools (IST) Team
Test Lead
---------------------------------------------------------
Please leave a comment if the blog post has helped you.