How to: Use CAT.NET v1.1 as a Visual studio Add-In to identify security flaws within managed code
Syed Aslam Basha here from the Information Security Tools team.
In the previous blog post I demonstrated “How to Run CAT.NET as a Custom MSBuild Task”, for more information you can refer to the blog post here. Here am going to demonstrate “How to use CAT.NET as a Visual studio Add-In to identify security flaws within managed code”.
Applications might have many security vulnerabilities like SQL injection, LDAP injection, XPath injection, Cross-Site Scripting (XSS), process command execution, file canonicalization, exception information and redirection to user controlled site. You can use CAT.NET tool to identify all of these security flaws.
What is Code Analysis Tool for .NET (CAT.NET)?
CAT.NET is a static code analysis tool, helps you to identify security flaws within a managed code (C#, Visual Basic .NET, J#) applications. It scans each assembly of the application, and then traces the data flow among application's source code statements, methods, and assemblies. This includes indirect data types such as property assignments and instance tainting operations. The engine works by reading the target assembly and all reference assemblies used in the application -- module-by-module -- and then analyzing all of the methods contained within each. It displays the issues it finds in a list that you can use to jump directly to the places in your application's source code where those issues were found. Lastly, you can export analysis data to excel.
You can run CAT.NET as;
- A Visual studio add-in
- From Command prompt
- As an FXCop rule
- Lastly, integrated into VSTF Team build as an MSBuild custom task. For more information on “Running CAT.NET as a Custom MSBuild Task refer to my blog post here)
For example:
1: //Process command execution vulnerability
2: Process aProcess = new Process();
3: aProcess.StartInfo.FileName = "someapp.exe";
4: aProcess.StartInfo.Arguments = TextBox1.Text; // source & sink
5: aProcess.Start();
6:
7: //File canonicalization vulnerability
8: File.Create(TextBox2.Text);
9:
10: //Exception information vulnerability
11: protected void Button4_Click(object sender, EventArgs e)
12: {
13: string connectionString = "Data Source=myServerAddress;Initial Catalog=myDataBase;User Id=myUsername;Password=myPassword;";
14: SqlConnection myConnection = null;
15: try
16: {
17: myConnection = new SqlConnection(connectionString);
18: myConnection.Open();
19: }
20: catch (SqlException myEx)
21: {
22: DoSomethingWithException(myEx);
23: }
24: catch
25: {
26: Label2.Text = "This is just test, so fine";
27: }
28: finally
29: {
30: myConnection.Close();
31: }
32: }
33:
34: protected void DoSomethingWithException(SqlException myEx)
35: {
36: string x = "Exception Info: " + myEx.Message; //Exception information vulnerable code
37:
38: }
39:
40: //LDAP injection vulnerability
41: protected void Button7_Click(object sender, EventArgs e)
42: {
43: DirectorySearcher searcher = new DirectorySearcher();
44: string filter = TextBox5.Text;
45: LDAP_InjectionMethod( searcher, filter );
46: }
47:
48: protected void LDAP_InjectionMethod( DirectorySearcher searcher, string filter )
49: {
50: string filterEx = filter + " Random Garbage";
51: searcher.Filter = filterEx;
52: }
53:
54: //Xpath injection vulnerability
55: protected void Button6_Click(object sender, EventArgs e)
56: {
57: XmlDocument doc = new XmlDocument();
58: XmlNode node = doc.CreateElement("Settings");
59: node.SelectSingleNode(TextBox4.Text);
60: }
61:
62: //SQL injection vulnerability
63: string connString = System.Configuration.ConfigurationManager.AppSettings.Get("connString");
64: SqlConnection myConnection = new SqlConnection(connString); //1 SQL Injection vulnerability exists here
65: SqlCommand myNaiveCommand = new SqlCommand("SELECT COUNT(*) FROM Users WHERE UserName='" + txbUsername.Text + "' AND Password='" + txbPassword + "'");
66:
67: //Redirection to user controlled site
68: string x = TextBox3.Text;
69: Response.Redirect(x); //1 Redirect vulnerabilty exists here
70:
71: //XSS vulnerability
72: string userName = txbUsername.Text;
The above code snippet has all the security flaws, you can use CAT.NET to identify them.
Steps to use CAT.NET:
- Launch the visual studio
- Create new website and copy paste the above code snippet
- Build the application
- Launch CAT.NET by clicking on CAT.NET code Analysis from Tools menu from visual studio
- Click on the Run button in the CAT.NET UI, it will analyze and show the issues as
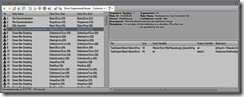
- Click on the issues to navigate to source code where issues were found
- Finally click on generate excel report button in CAT.NET to generate excel report as shown below
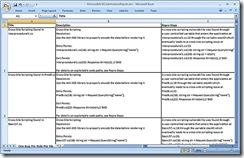
- Publish the report and log bugs
You can refer to more articles on CAT.NET here
-Syed Aslam Basha ( syedab@microsoft.com )
Microsoft Information Security Tools (IST) Team
Test Lead
---------------------------------------------------------
Please leave a comment if the blog post has helped you.