Standalone Windows Intune – Managing Systems
My last blog post provided details on how to setup and configure standalone Windows Intune in a test lab environment along with a walk through of the Windows Intune consoles and capabilities. This post will expand on options presented in the previous session and special focus will be given on leveraging Windows Intune in various Software Deployment scenarios. We will wrap up discussion by showing the various troubleshooting options available for each platform. A lot of ground to cover, let’s get started!
Endpoint Protection, Alerts, Licensing, Policy, Reports
We will start with these because not a lot of additional explanation is required since I have already covered these nodes in overview form in the previous blog post. There isn’t a need for tons of additional discussion about how to configure thee options or needed configuration as they are mostly self-explanatory.
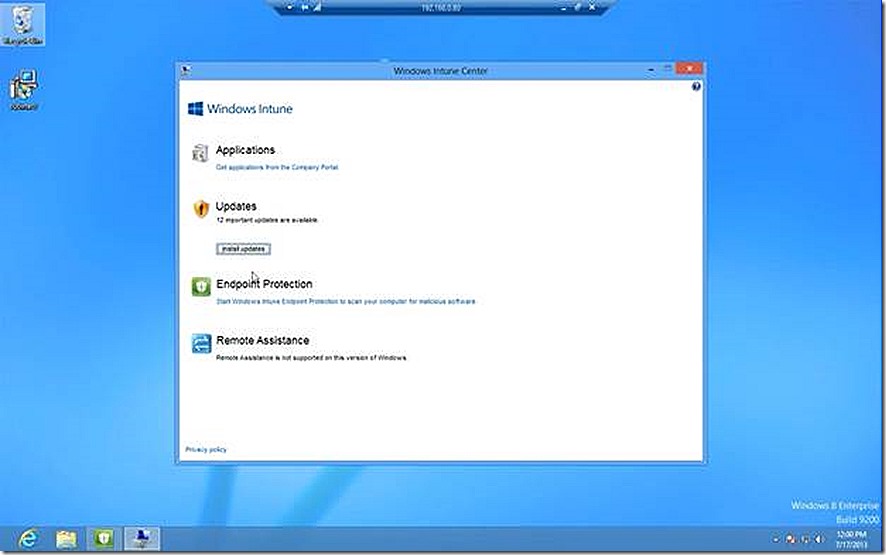
EndPoint Protection
The Endpoint Protection node allows viewing the Malware status of the environment and also provides links to schedule scans, setup policy, etc. One thing to understand here is that the Endpoint Protection settings are totally driven by the policy settings that are in place.
Alerts
The alerting node allows viewing active alerts, grouped by category. From here it is also possible to subscribe to alerts (which results in an email being sent to you when the given alert is fired), reset the category (severity) of a given alert and group alerts as appropriate for your environment.
Licensing
The licensing node allows importing Microsoft and third-party license statements. This information is then paired with software inventory data to help understand your license usage and counts.
Policy
The policy node allows deployment of default policy settings to groups of users or devices, as appropriate for the policy setting. It is also possible to use the 4 default policies as templates for creating your own custom policy that is deployed to select groups.
Reports
The reports node contains several default reports useful for understanding how your environment is responding in various areas such as detected software, software updates and License status.
Groups
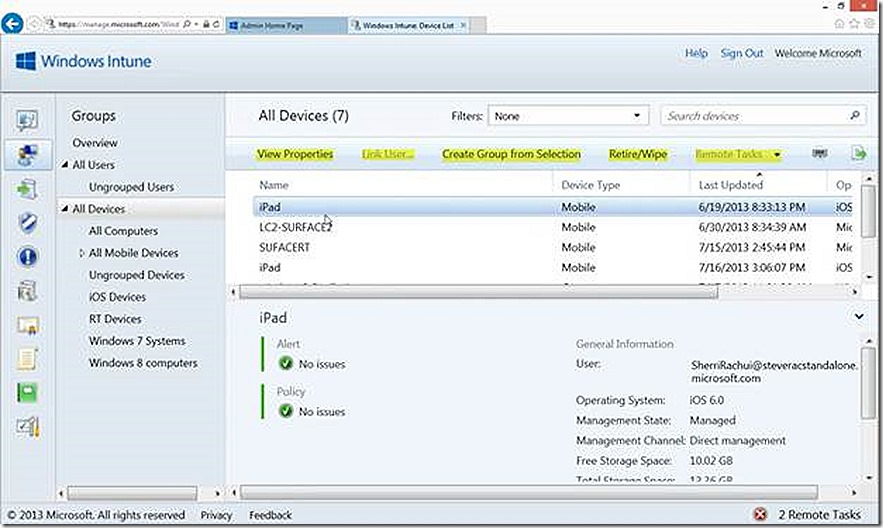
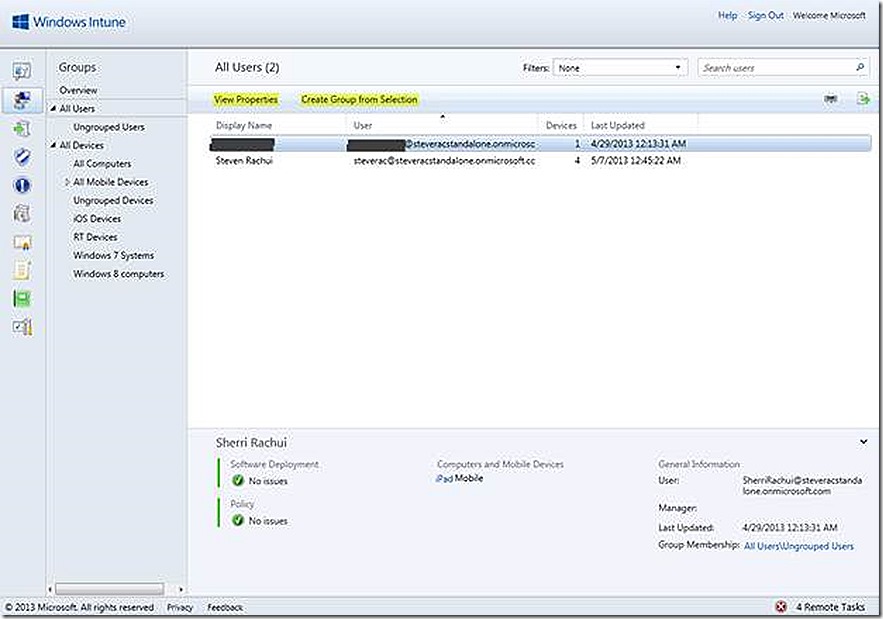
As detailed in the previous post, Group are the Windows Intune equivalent of collections and are used to organize the various devices and users into manageable units that can then be leveraged as targets of management. Once the groups are created and populated there are various actions that can be taken on members of the group. The available actions will vary depending on whether the group contains devices or users and, in the case of devices, what type of device is selected.
Device Groups
Note the options available for members of a device group. Notice that some options are grey. These options will be available on device types where it makes sense. As an example, the retire/wipe option makes sense for an iPad but doesn’t make sense for a PC. If we focus on a specific group member, whether device or user, various options present themselves.
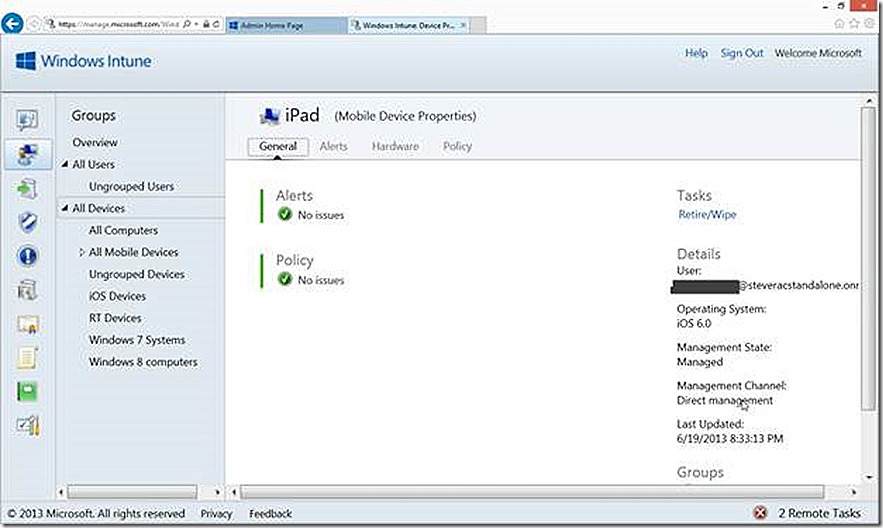
View Properties
One option available is to view device properties which will provide more detail about the selected device. If I select to view the properties I’ll see detail similar to what is shown below.
Retire/Wipe Device
This option is very useful for those scenarios where a device should either no longer be managed by Windows Intune (Retire) or where there is concern about device security due to theft, loss, whatever (Wipe). There is a difference in the way devices handle Retire/Wipe requests – the difference is dependent on the capabilities of device itself. Further, there is a difference in the speed at which a request to Retire/Wipe a device is carried out. Typically devices that are configured to use Exchange ActiveSync, even is also managed by another method, will respond to the Retire/Wipe request more quickly due to the frequency that Exchange ActiveSync communicates.
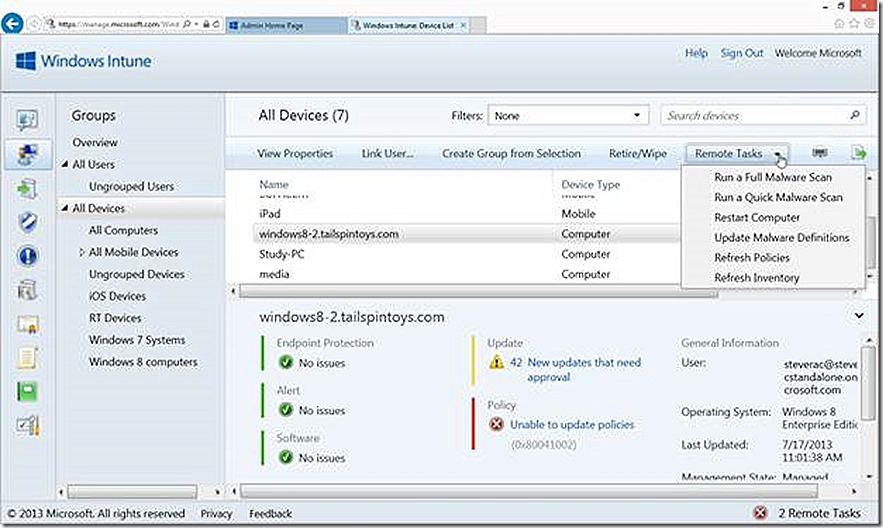
Remote Tasks
If we highlight a managed PC system the option to execute Remote Tasks becomes available. Using these options it is possible to initiate Malware scans or Malware updates. You can also Restart the target PC or Refresh Policies and Inventory on the device.
These actions typically happen very quickly.
Restart – This action will restart the target PC and the action takes place very quickly but does not happen immediately. When the action is triggered the user will be notified that a reboot has been requested and they will have a short windows in which to close down applications, save data, etc.
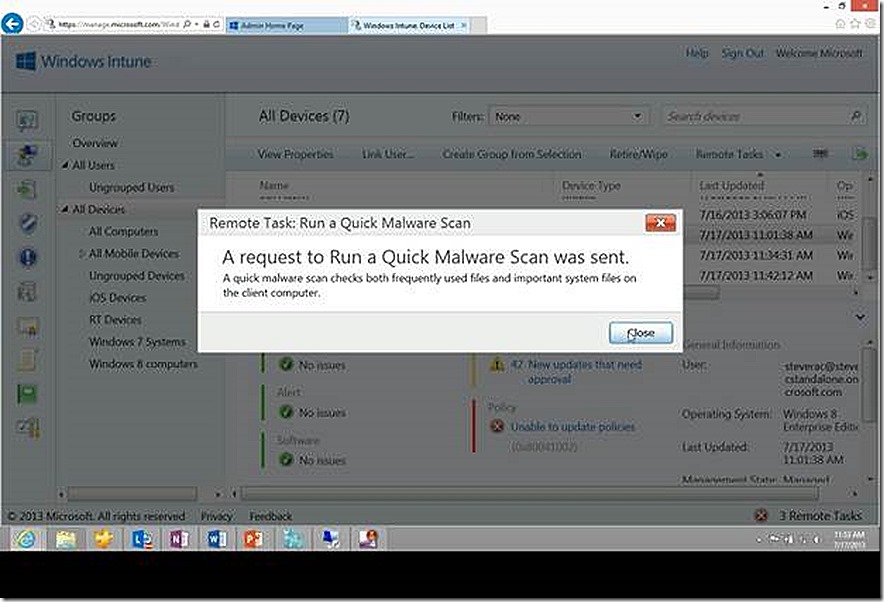
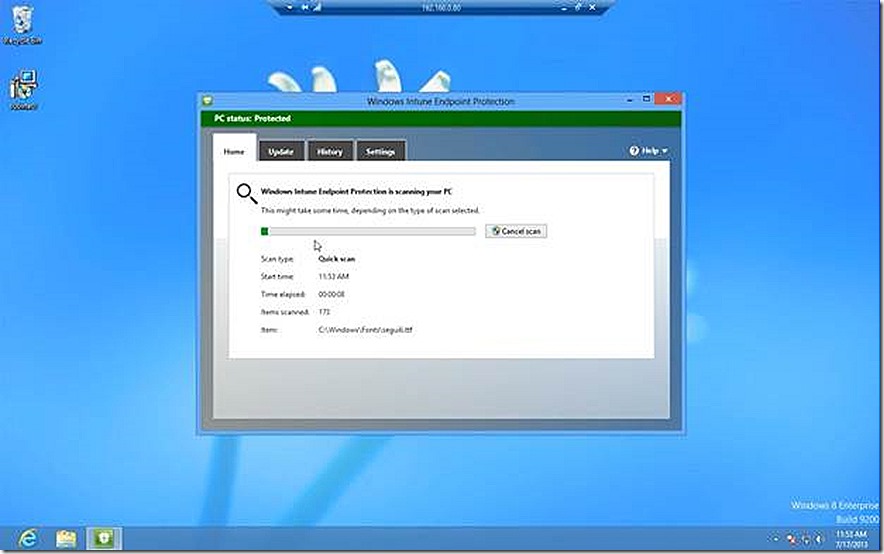
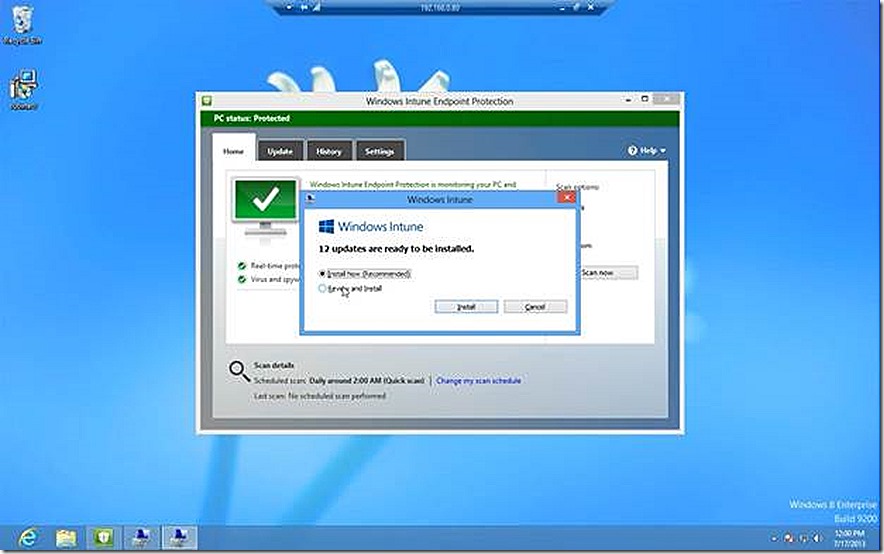
Quick Malware Scan – This action will initiate a Quick Malware Scan on the target device. It is also a useful option to demonstrate the use of Remote Tasks and also the speed.
When the Quick Malware Scan is initiated a message is presented for information and the scan is initiated.
As quickly as I can pull my Windows PC into view (less than 10 seconds), the scan has initiated.
User Groups
Note the options available for members of a user group. The options here are basic compared to those in device groups.
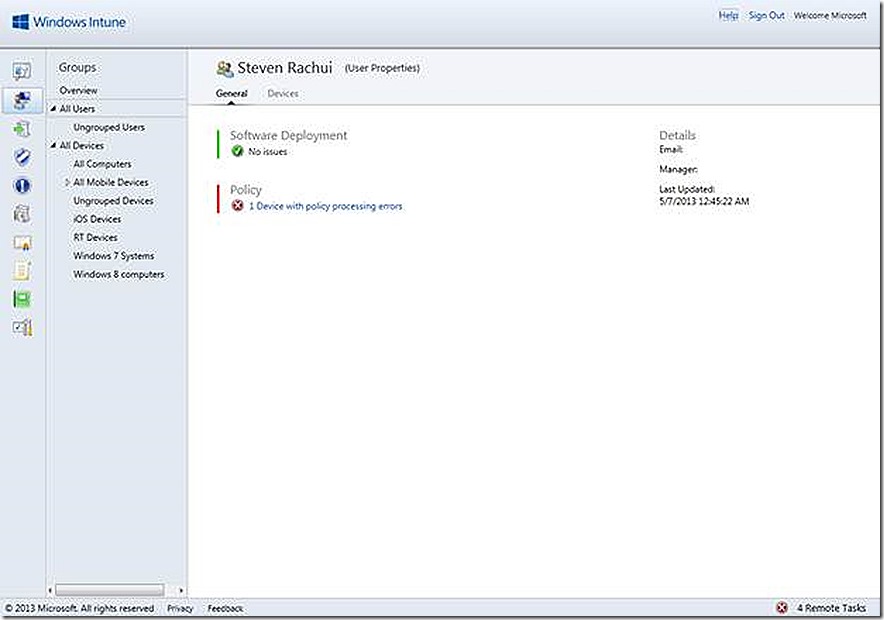
View Properties
One option available is to view properties which will provide more detail about the selected user. If I select to view the properties I’ll see detail similar to what is shown below. Here we are able to review any issues with software deployment to the user and any policy processing problems with devices associated to the user.
Software Updates
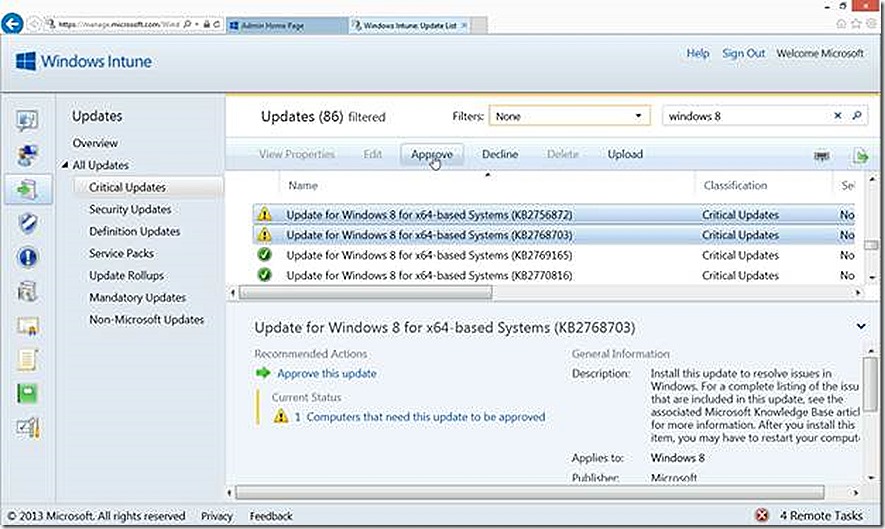
I briefly walked through the process of configuring software updates for deployment in the previous blog post. In this case I’ve highlighted some needed Windows 8 updates that show as required by at least one system (since I only have one Windows 8 system in my lab right now, I know these are applicable to my test system!). Notice the different icon associated with updates that show as all good and those that show as needed.
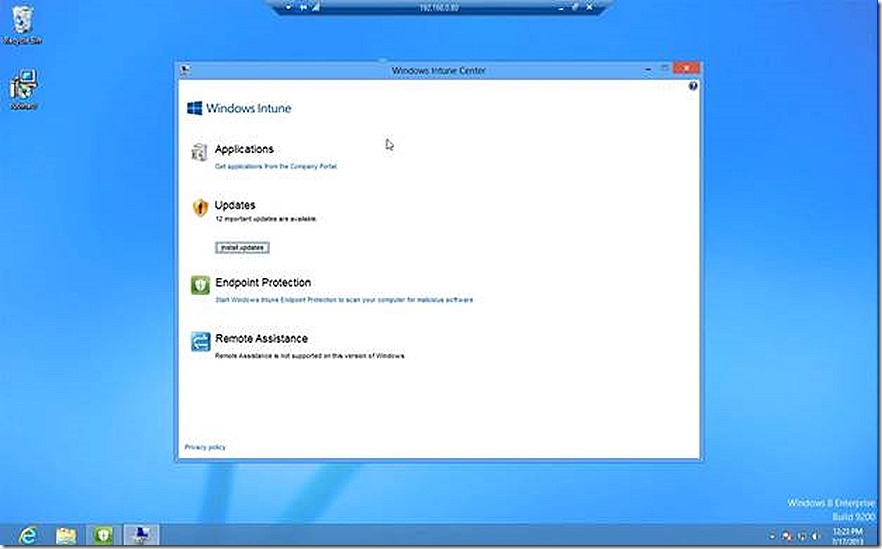
With these deployed I now move back to my Windows 8 system and open up the PC based Windows Intune Center which allows users to interact with the various pending operations to their device. One option is to check for pending software updates. When I click that option I now see there are a number of updates pending for my system which were made available by my configurations in the Windows Intune console.
If I click to install the updates I am prompted to confirm what I want to do. I make the appropriate selection and the updates begin to install.
Software
In most scenarios, deploying software to PC’s and devices will be a key component of managing with Windows Intune. The mechanisms for software deployment will vary based on the target of the deployment and also the software being deployed.
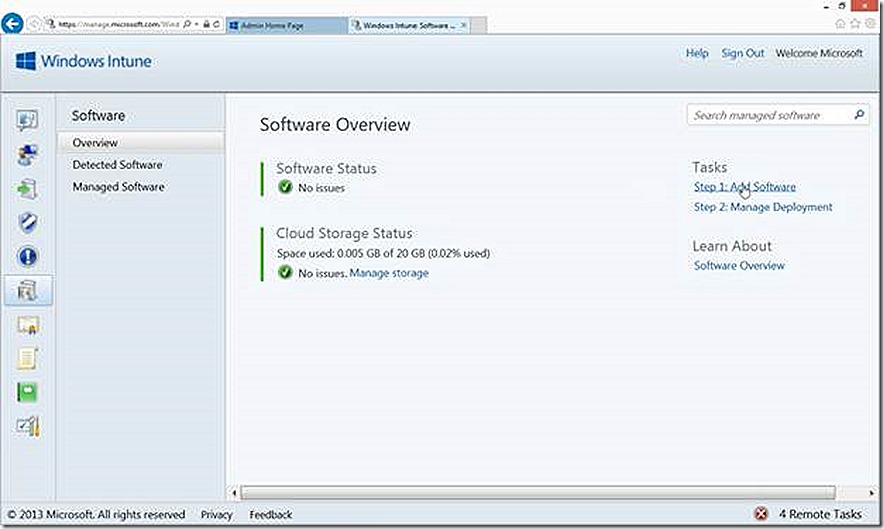
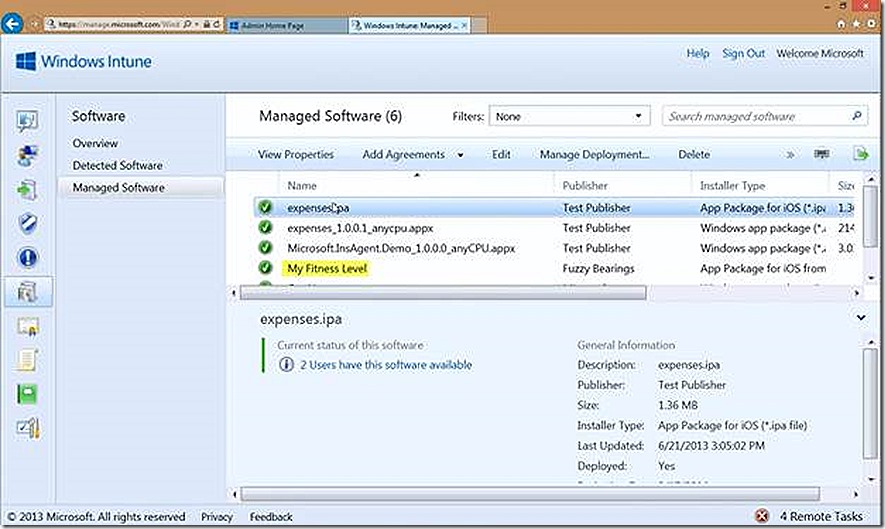
On the software page there are three options, the overview node which is where we have links to add new software or manage deployments, the Detected Software node which will show all software that has been detected across the environment (think software inventory) and the Managed Software node which will show all software that has been configured for deployment.
In all cases the software deployment process begins by selecting the Add Software task, which opens a wizard (you may need to authenticate with your Windows Intune credentials again). The Before you Begin page of the wizard is information that you can choose to bypass when the wizard runs in the future if you like. The Software Setup page is where you make all of the selections that will drive the type of deployment being configured. The defaults are for software being deployed to PC’s. This is where things start to diverge based on device types.
The best way to explain how to configure and manage software deployments is with examples. We have a test PC, Windows RT device and iPad in the lab so will deploy software to each.
PC
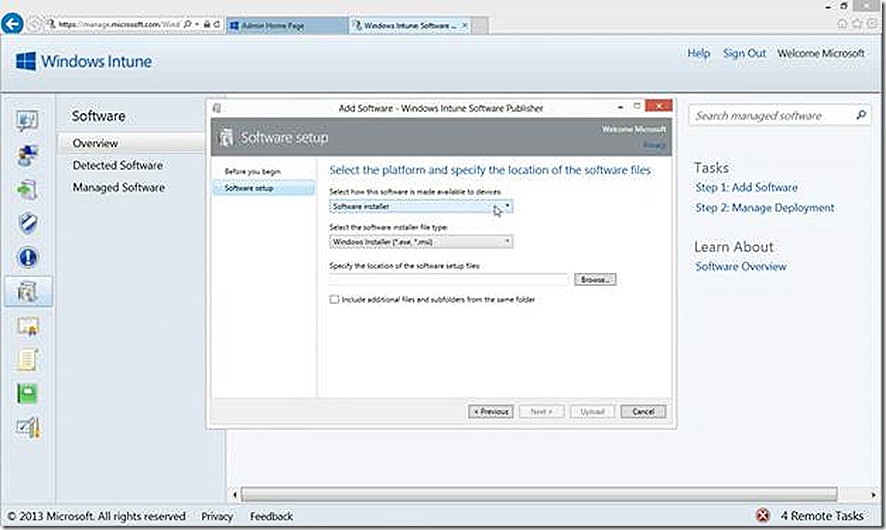
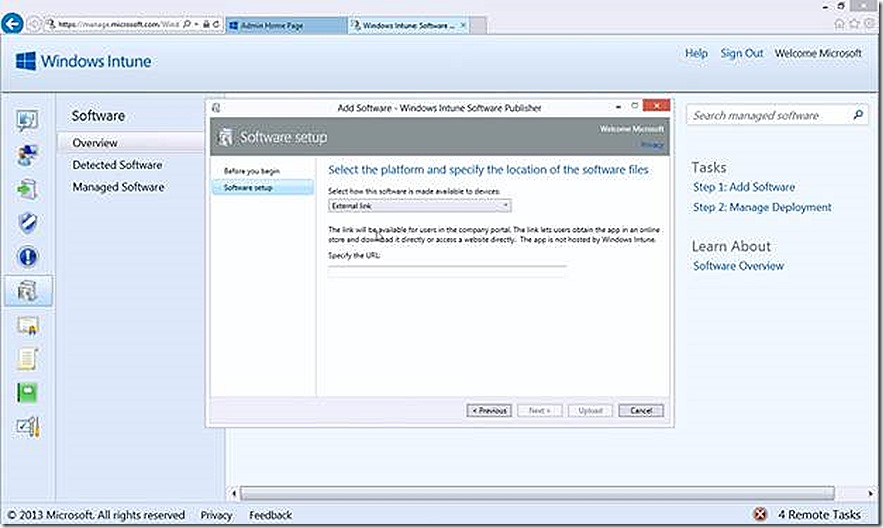
There are two choices you have when deciding how to deploy software to a PC (or device). The first is to use a Software Installer. This will be the only option applicable for most PC deployments. For Windows 8 devices forward, though, the other option, External Link, is also applicable. This option specifically allows you to provide a link to an application that already exists in the Windows store. This process is also known as Deep Linking. I’ll explain this more when we get to the Windows RT example.
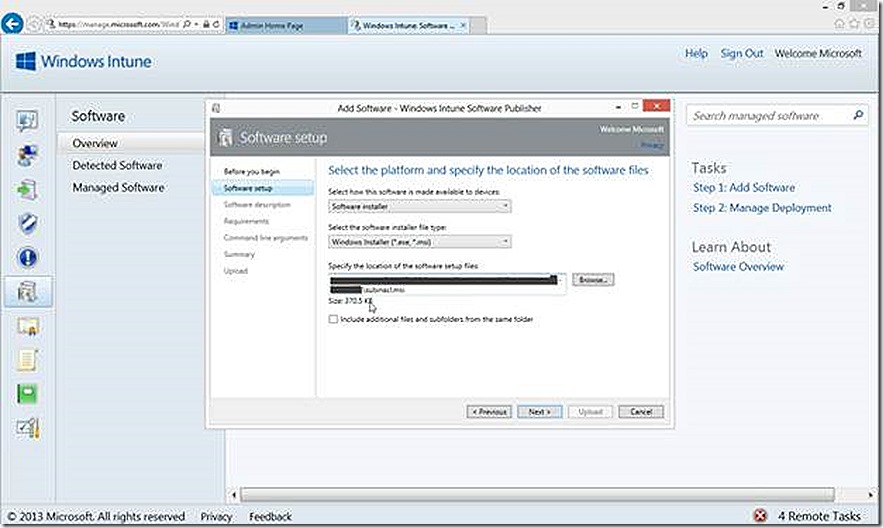
For our PC example I’ll just deploy a test .MSI, in this case subinacl.msi. I supply the UNC path to where the content is stored and click next. Notice also that I now have more options along the left hand side that are relevant to the deployment option that I’ve chosen. Further notice the Include additional files and subfolders from the same folder option. In my case I don’t need to select this because my test .MSI is self-contained. If deploying something like Office or other software that contains multiple files, you will want to check this to include all of those files. Be careful here though because you could accidentally include more than you need resulting in consuming more space than needed in your cloud storage.
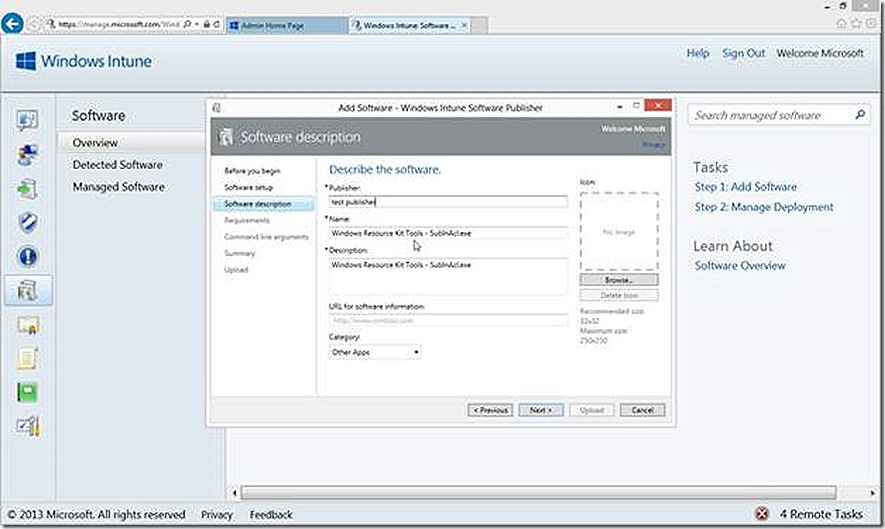
Next we have an opportunity to provide details that further describe the software deployment, such as Publisher, Name, Description (these are the only ones required), URL for additional documentation, Category and even a custom icon if you like.
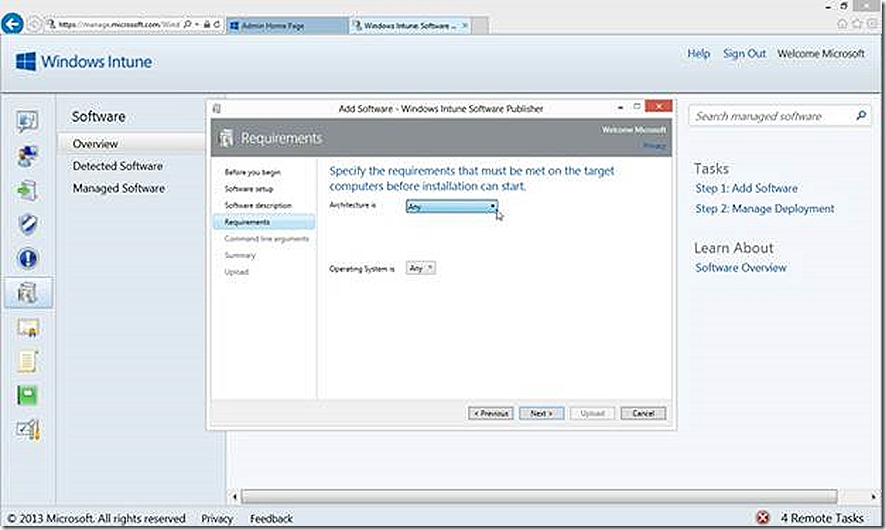
Next we choose any specific Architecture or OS types for the Deployment
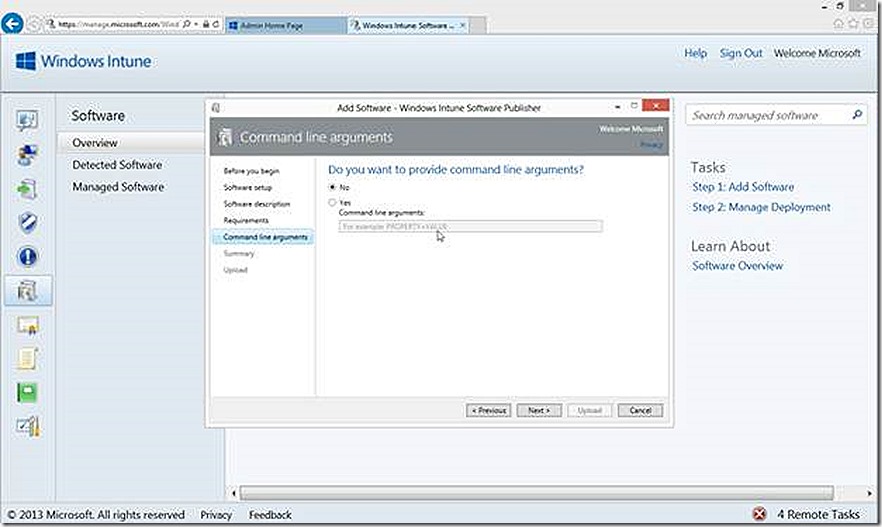
and supply any command line arguments for the deployment.
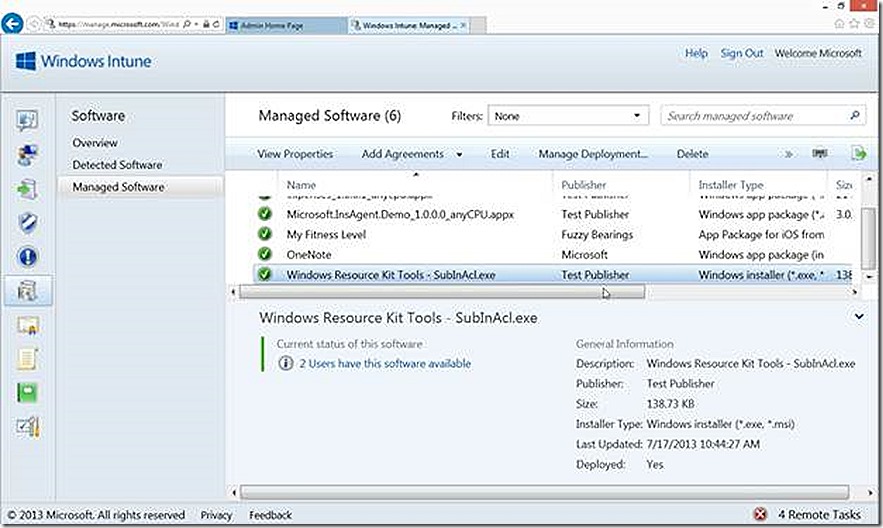
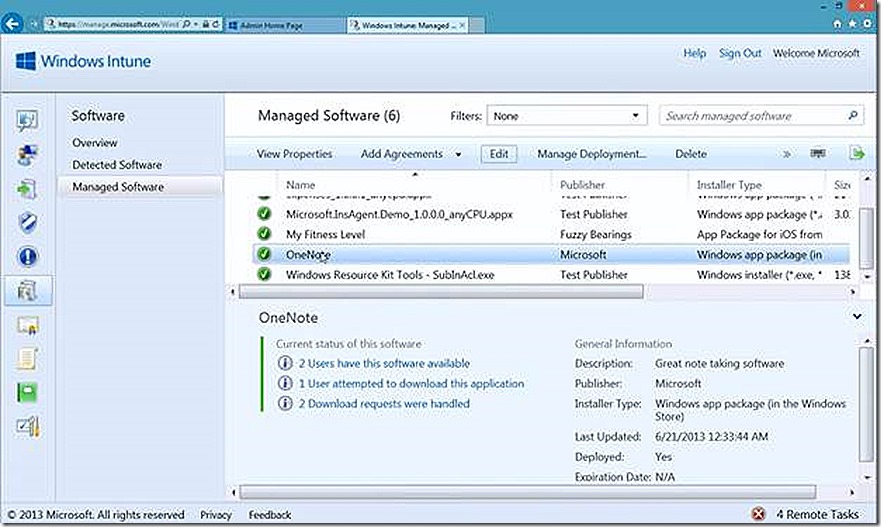
From here you can review selections on the summary page and then proceed to upload the content to the Windows Intune environment. Once uploaded the deployment will be visible in the Managed Software node where we can select to deploy the software.
We see that the software is available and is deployed to 2 users. So this points out that for PC deployments, software can either be targeted to groups of users or groups of devices. If deploying to users there is no way to set the deployment as required where with PC’s that option is available. I’ve chosen users for convenience.
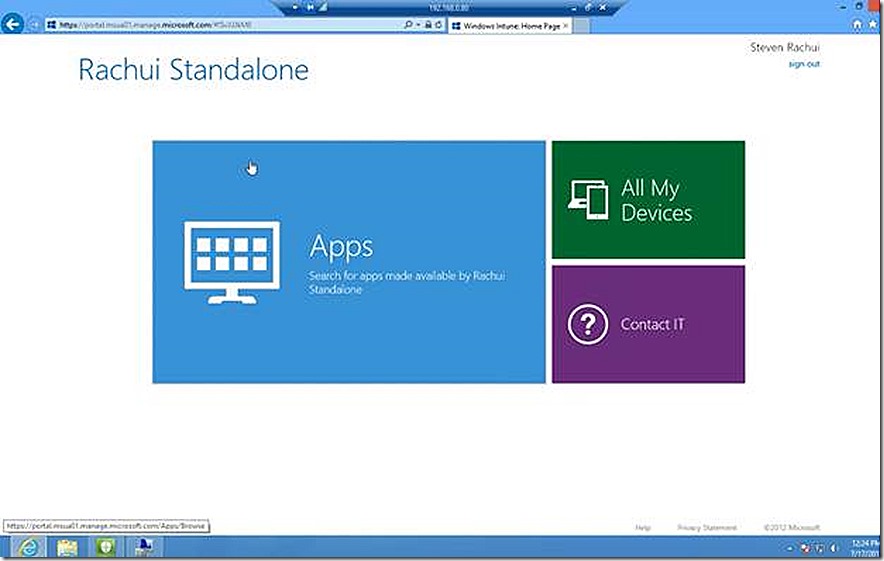
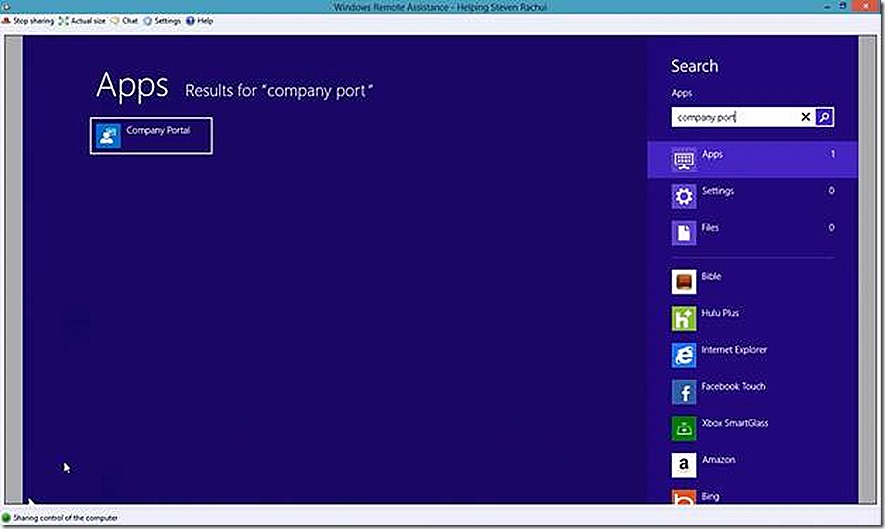
So this application should now be available to the user of my test Windows 8 PC. If I go into the Windows Intune Center and click to get applications I will be redirected to the company portal or given the change to install it if not present.
The web based view of the company portal shows up.
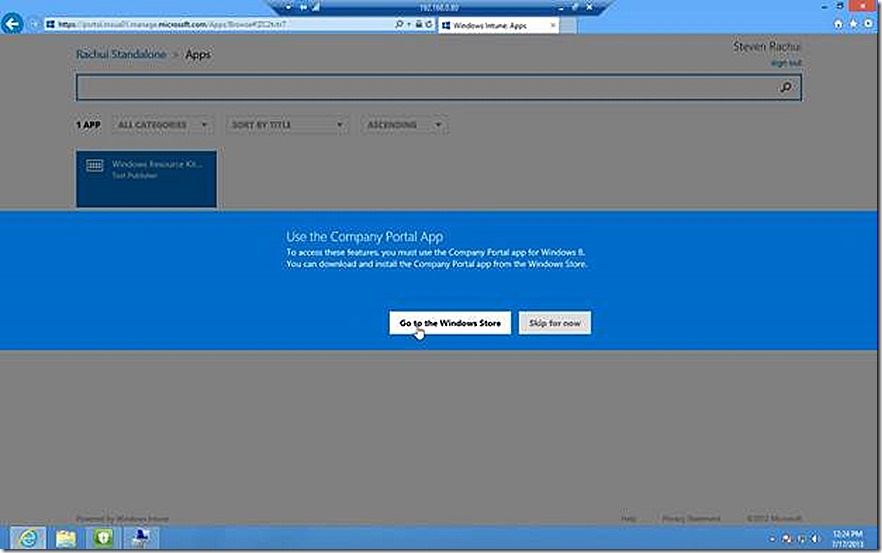
This web page is not useful for installing software, you instead need the company portal app installed on your PC. You see this when clicking on Apps. At this stage either go to the Windows store and install the Company Portal app or just redirect and launch the Company Portal apps from the start screen.
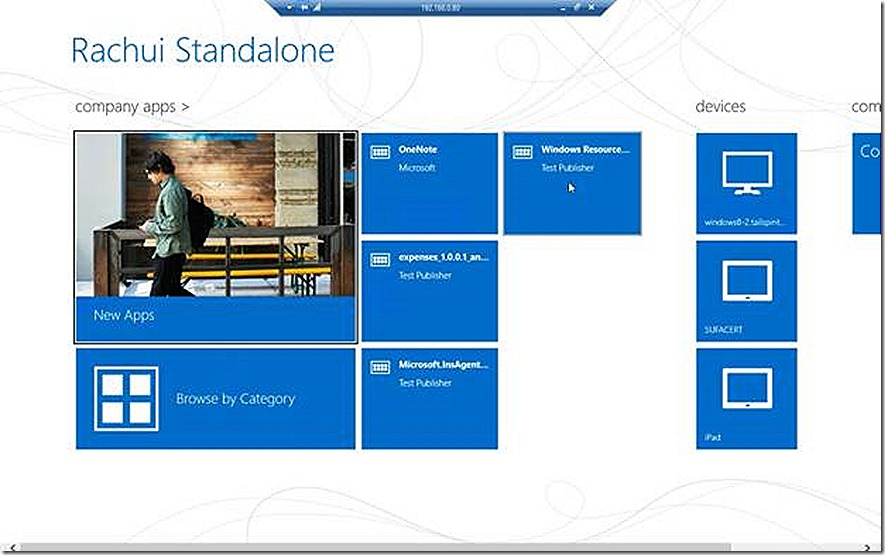
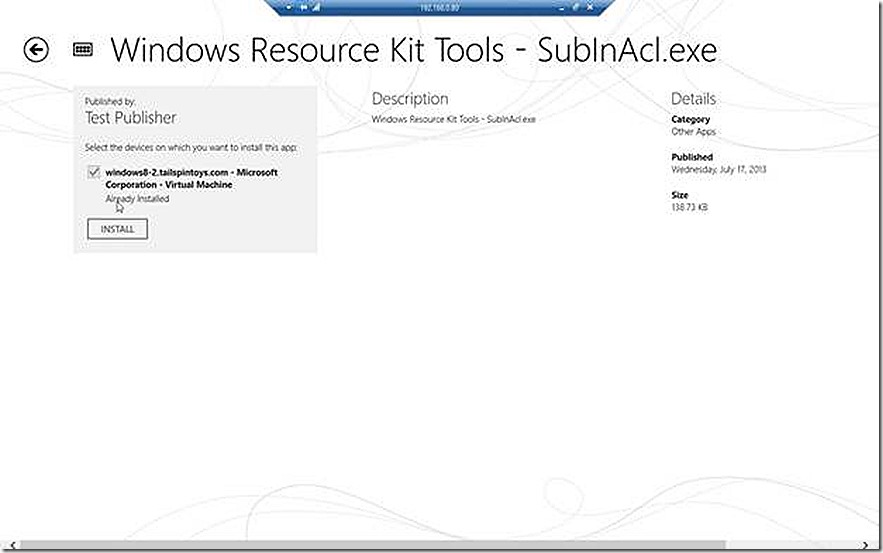
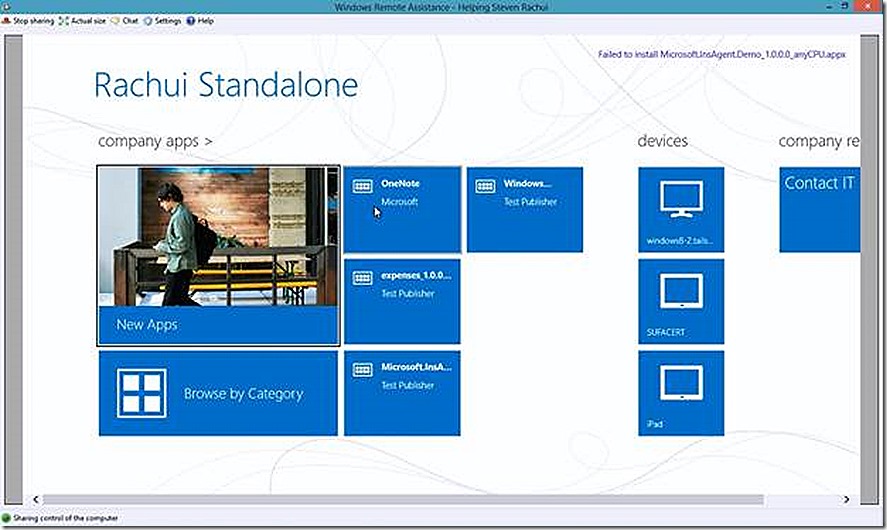
When launching the company portal app you likely will need to sign in again and then you are presented with a view that is very similar to what we just saw except this time we actually see apps available for install. Some of the apps here are available because they are targeted to the user that is logged in but they are not applicable to the PC. I see the Windows Resource kit tool subinacl listed on this main shortcut page (name truncated) and select it to begin the install.
I actually already have it installed as shown and the Install option is grey but if I didn’t this is where I would launch the install process.
So that’s it for PC’s except for showing Deep Linked deployments which are only applicable to Windows 8 + systems. Also, I showed deploying an MSI but you could just as easily deploy an .exe. OK, onward to Windows RT!
Windows RT
So now we get to Windows RT. We will use our Windows RT discussion to highlight the process of deploying an app from the windows store, a process known as Deep Linking and the process of deploying a custom modern app (.appx). As a part of our discussion about deploying custom modern apps we will also introduce the idea of side-loading, which is very important to understand. Side-loading applies to both Windows 8 and Windows RT systems. More on side-loading shortly.
Deep Linking
Deep Linking is the process of identifying an application in the Windows store that you wish to deploy to Windows 8 or Windows RT systems. As the name implies, Deep Linking simply provides a link to the user that will take them directly to the app in the Windows Store, bypassing the need for them to search for a specific app and perhaps loading the wrong one.
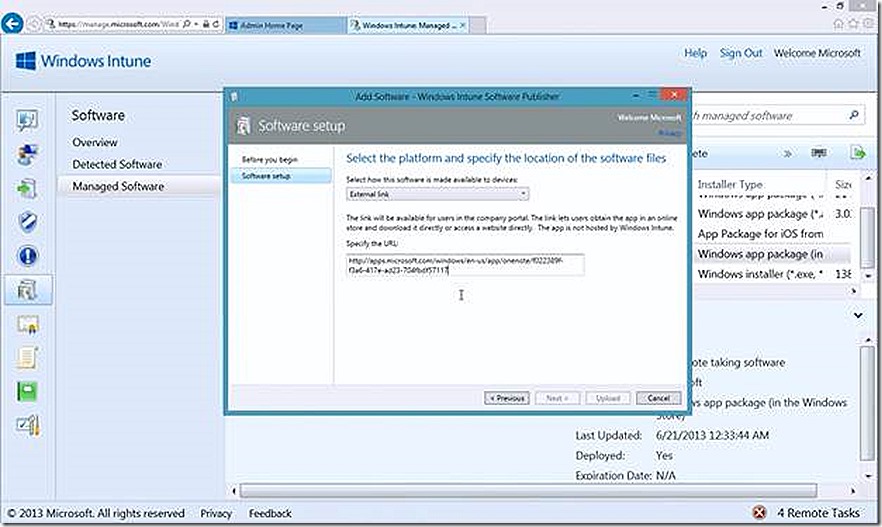
To configure a Deep Linked deployment simply select External Link as your choice In the Add Software wizard.
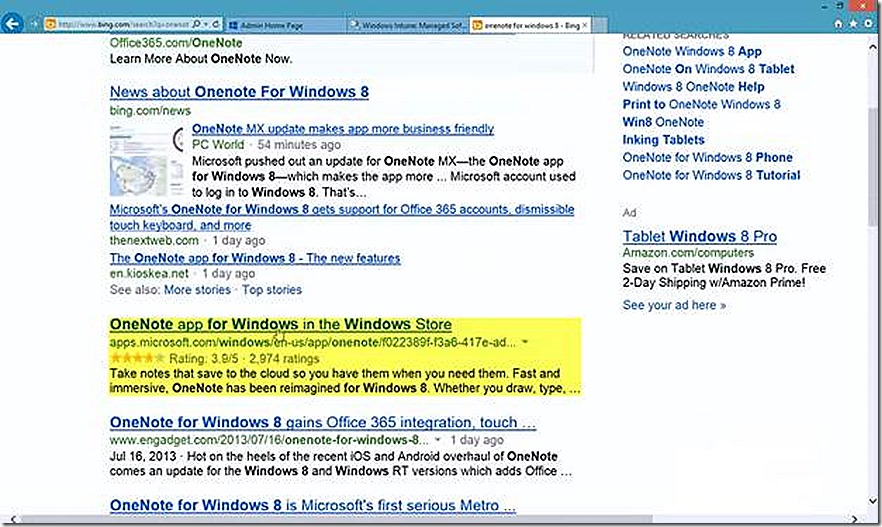
Note that you also need to provide a URL for the application you are deploying. The easiest way I’ve found to find the appropriate link is to do a Bing search for the application in question, in this case OneNote, as shown. The search phrase I used was ‘OneNote for Windows 8’.
From here I have the URL and simply plug it into the Add Software wizard, answer the remaining detail questions that are part of the wizard and finish up.
My OneNote deployment is now created and I’m ready to make it available to managed systems.
Note: Some applications in the Windows store are not publically searchable because the application published to the store is flagged as private by the publisher. If you have such an app you wish to deploy to your users the process works the same way except you will need to know the URL since search will not reveal it.
Custom Modern Applications
Beyond simply providing a link to applications published in the Windows store is the ability to deploy custom built modern apps (.appx) to your Windows 8 and Windows RT systems. The process of doing so is easy but there are a few things you need to know first, so let’s cover those before showing the process.
Deploying a custom modern application (which is only applicable to Windows 8 and Windows RT systems forward) requires three prerequisites must in place - a code signing certificate, deployment policy and, in many cases, a side-loading key. Let’s take these in order.
Code Signing Certificate
Custom modern applications must be signed with a code signing certificate to ensure security when deployed to systems. The certificate used for signing must be trusted by the target system. This actually applies even when deploying an app from the Windows store but in those cases the certificates used to sign the apps in the Windows store are already trusted by default on the target systems so it just works. For custom apps the certificate used for signing may or may not be trusted by default. Typically if the code signing certificate is issued by a commercial certificate authority there won’t be any issues. If the certificate is not trusted by default then you must make take steps to ensure the proper certificate chain is present in the target devices certificate store.
Deployment Policy
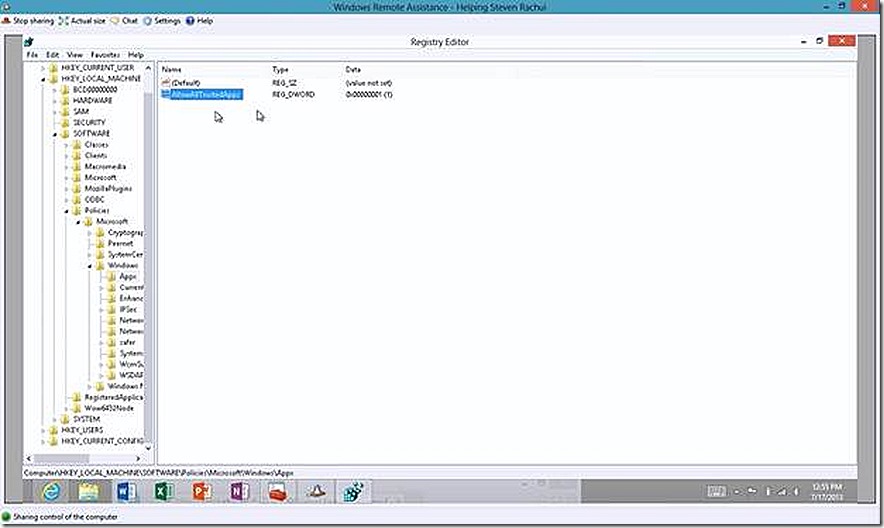
Systems where you will deploy custom modern apps must be configured to allow such deployments. This is easily done by navigating to Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > App Package Deployment. Ensure the setting Allow all trusted apps to install setting is enabled. This policy change is implemented in the registry of the target system at HKLM/Software/Policies/Microsoft/Windows/Appx/AllowAllTrustedApps = 1.
Side-loading Key
The process of installing a modern application requires the target system be authorized to accept custom applications. The process of loading a custom modern application is known as side-loading and the process of approving a device to allow side-loading is done by activating a side-loading key. So, do all versions of Windows 8 require a side-loading key? No, but most do. A Windows 8 Enterprise system that is domain joined is already configured to allow side-loading. Windows 8 Pro (domain joined or workgroup), Windows 8 Enterprise (workgroup) and Windows RT all require the use of side-loading keys to approve the device for side-loading custom modern applications. For Windows RT systems, the side-loading key can be configured in the Windows Intune administration console. For other versions of Windows 8 you must configure the side-loading key yourself.
More details on the requirements of deploying modern applications can be found here.
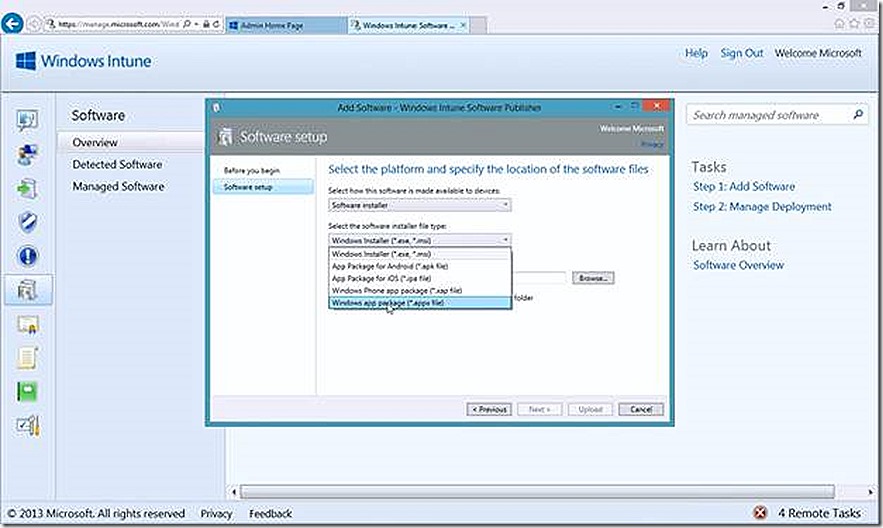
With that out of the way we revisit the Add Software wizard and this time choose Software Installer and choose Windows app package for the installer file type. From here I simply supply the path to the .appx file and other detail information - similar to what I’ve already shown – and upload the content.
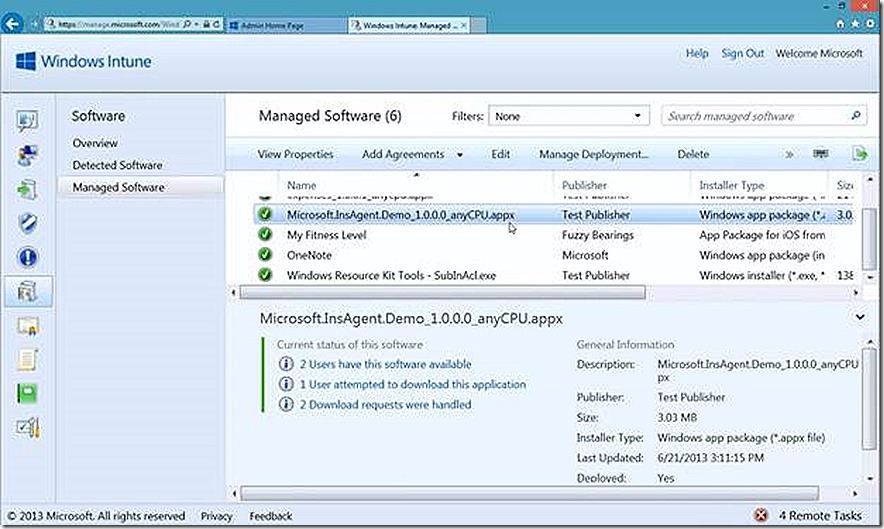
For my lab I’ve chosen a custom Demo Insurance Agent application for my .appx file and uploaded. The content is now ready for deployment to systems.
With all of this configured let’s move to our Windows RT device and launch the company portal and sign in.
At the risk of being Mr. Obvious, remember that with the exception of a PC, all deployments are targeted to the user – so only those deployments associated with my user will show up here. Yes, you do see the subinacls PC deployment we just discussed but remember that it was targeted to the user so it also shows up here. Another question that may come up – are we able to force a user to install an application on their device? No. If you have a PC and wish to force install an application you can target it to the PC device but any deployment targeted to a user must be initiated by that user.
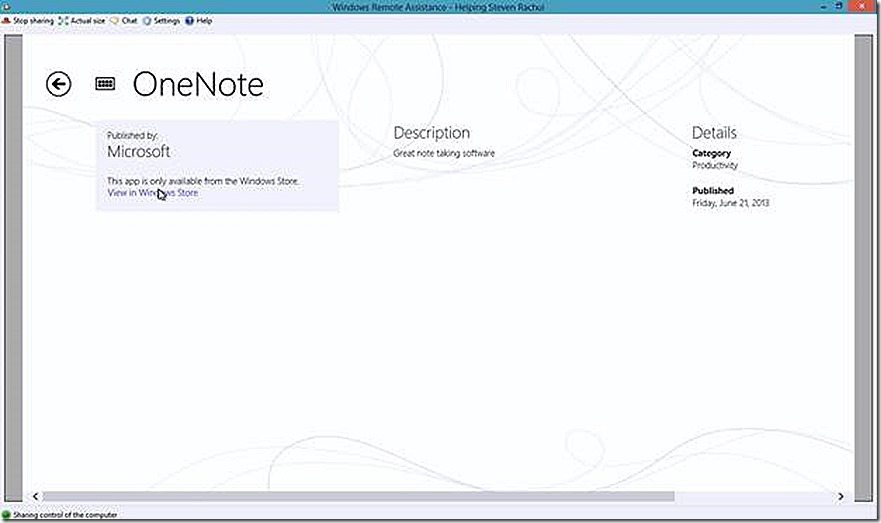
We have two deployments to test, OneNote deployed using a Deep Link and the Insurance app deployed as a custom appx. If I click the OneNote app I will be presented with a link where I can select to view the app in the Windows store.
Clicking the link takes me directly to the application in the Windows store where I’m able to deploy it. In this case, I already have it installed so no further action is needed.
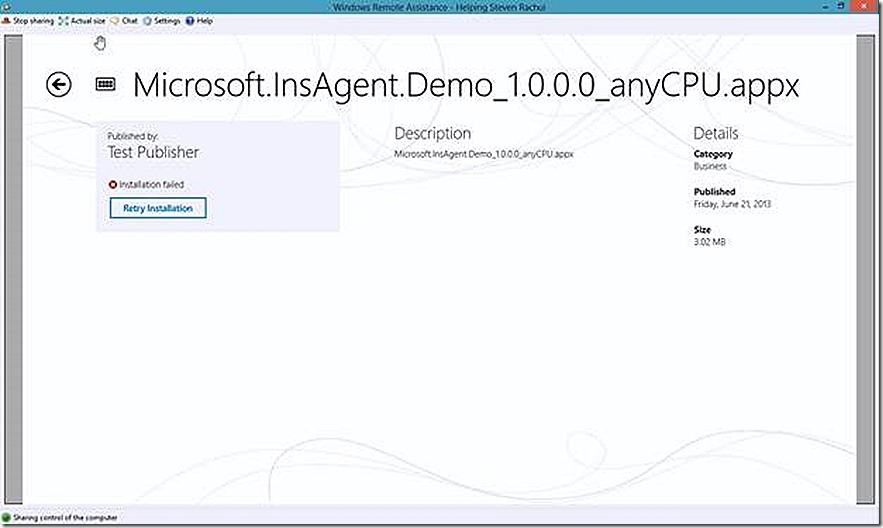
Also in the company portal we have our custom modern app deployment, the demo Insurance Agent app. If I go to launch that installation you will see that I had some failures deploying this app – the reason was that my code signing certificate was not trusted by my Windows RT device. I’ve corrected that problem so when I click Retry Installation the app will now install.
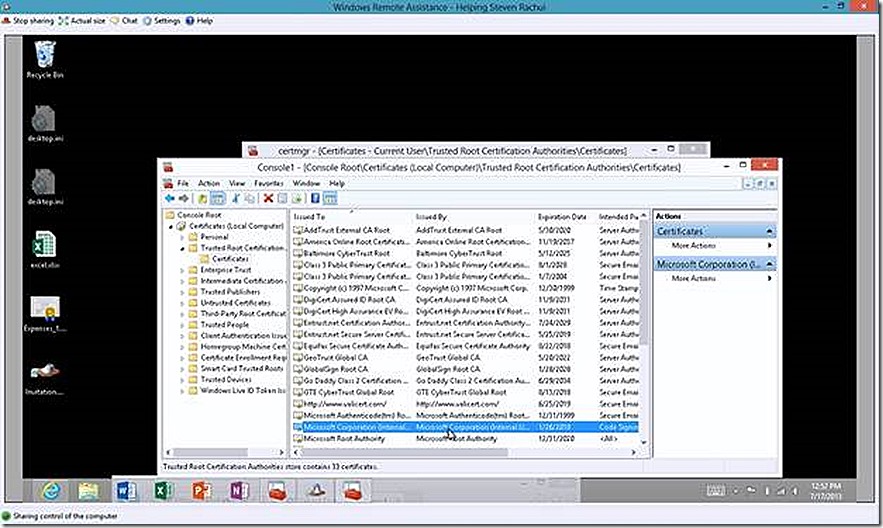
Confirming the code signing certificate is trusted is a simple matter of checking the certificate store on your Windows RT (or Windows 8) system. Load up the Local Computer certificate store and look under Trusted Root Certificate Authorities. If your certificate is issued by a commercial Certificate Authority then you will likely find the appropriate certificate in place here to allow validation. If your application is signed with a certificate issued by your own Certificate Authority, as in my case, you will need to make sure that certificate is trusted here.
While we are verifying the certificate we can also validate our system is configured to allow custom modern application deployment by reviewing the registry key mentioned earlier.
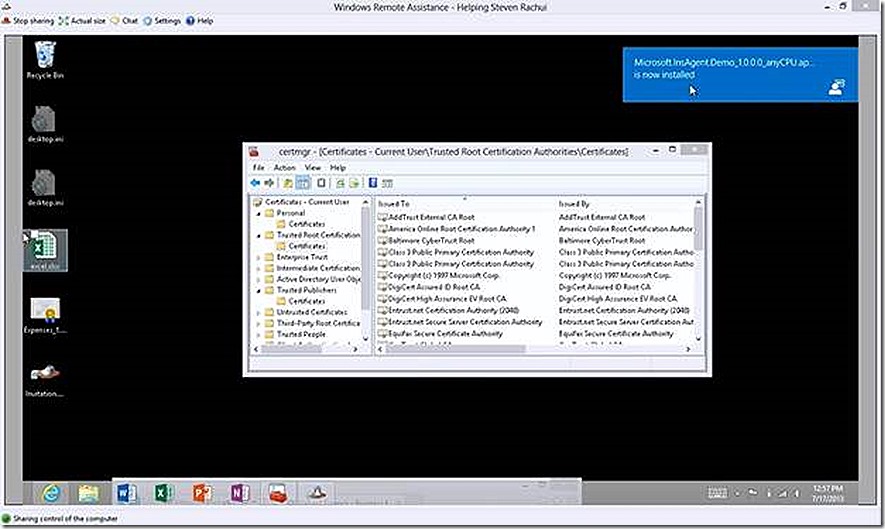
With all of this verified if we click to retry the install of our custom application we will see after a couple of minutes that the installation has completed successfully and our application is ready for use.
That’s it for Windows RT (and applies to Windows 8), let’s take a look at the same process but now focused on an iPad.
iPad
With an iPad the same concepts of Deep Linking and custom application deployment apply but the mechanics of both are different.
Deep Linking
For the iOS Deep Linking we work through the exact same process as already described for Windows RT but the URL we specify is different. To find the URL for an app in the Apple store I browse to the Apple site, https://www.apple.com, and select iPad from the main menu. On the iPad menu go all the way to the bottom and on the left you will see a link for App Store. Select that and the scroll down on the resulting page and find the proper app category to browse. Select that and then find the app you care about. Once you find the app, select it and this will give you the URL you need for the wizard. Yes, I know, that may not be the most efficient way to find the URL but that’s the way I found to navigate the link and haven’t bother to find another way!
Custom Application
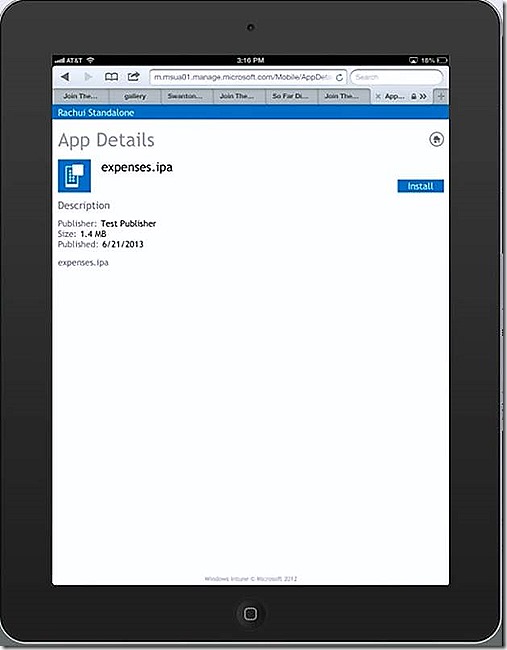
A custom application is added very similar to what we just did for Windows RT except for an iPad just select the .ipa option and upload your content. You will need to make sure the application is prepared according to Apple standards but you shouldn’t need to worry about additional certificates – at least I didn’t need to do so. Again, I’m not an Apple guru so there may be some extra configuration here I just didn’t run into, but I don’t think so. For our test I have a custom expenses app for the iPad.
So I now have both the Deep Linked and Custom Application ready to deploy in Windows Intune.
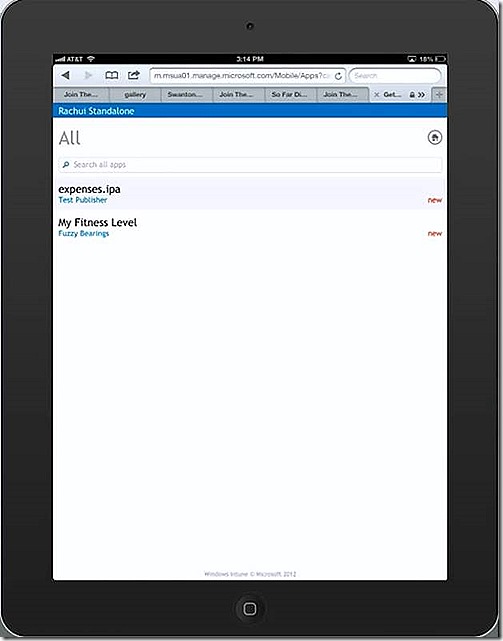
If we go to our iPad and bring up the company portal app (which is actually a link to a web page) and then navigate to the Get Apps option I will have various app categories. For my deployments I select the All option and see both apps I’ve configured for deployment.
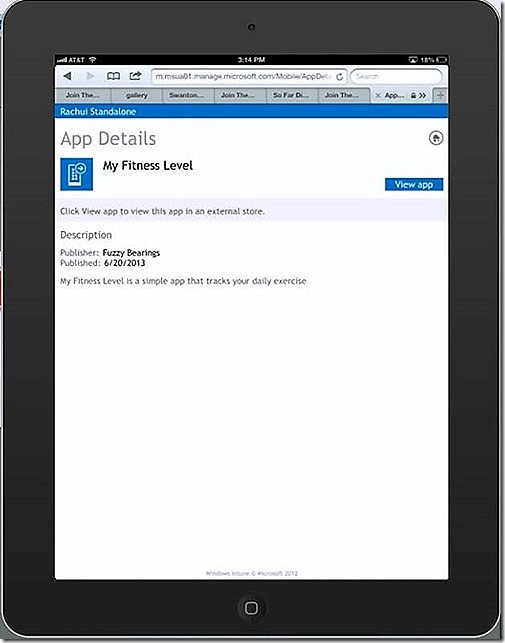
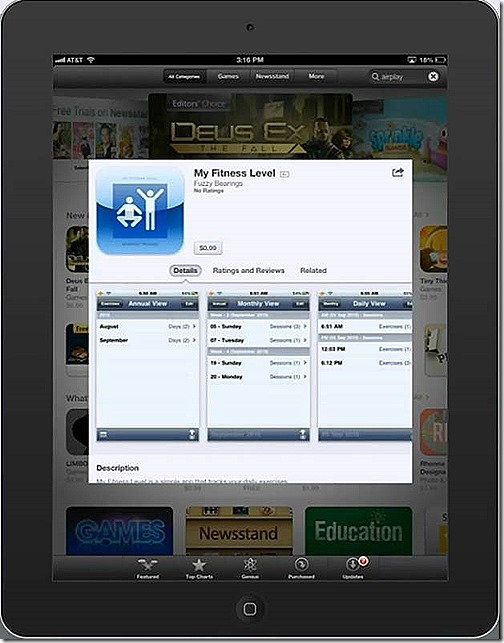
If I select the My Fitness app, which is the Deep Linked app, I have the option to View app which will take me to the app in the Apple store and present me with the option to install.
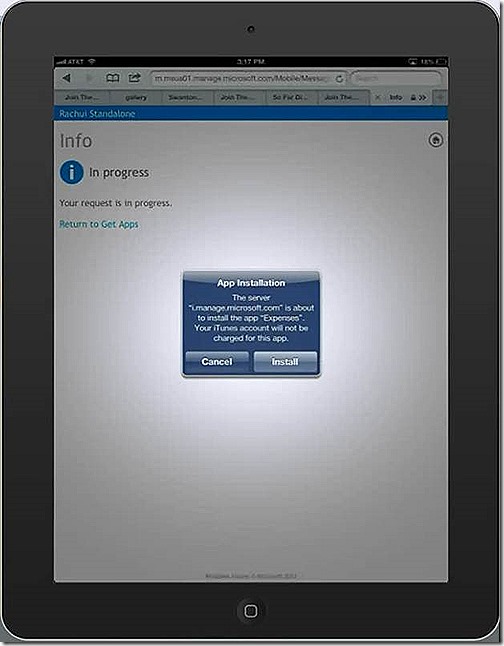
Back in the Company Portal I also have my custom Expenses app available to install. If I select that
I’m presented with the option to install. Clicking to install begins the process and after a couple of minutes you will see that the installation was successful.
And that’s the iPad and also concludes our tour of Windows Intune management!
Troubleshooting
A brief word about troubleshooting.
PC Systems
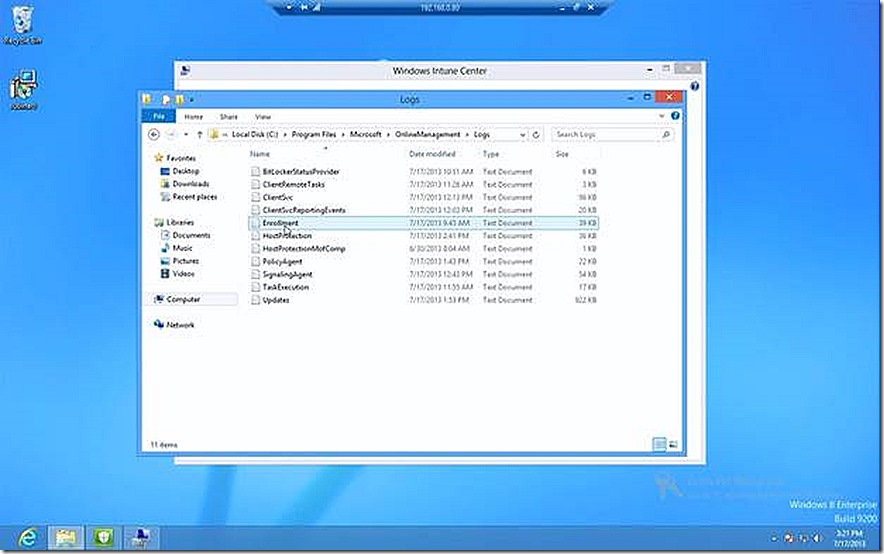
All Windows PC systems managed by Windows Intune require a client install for management. When managed by a client troubleshooting a PC system is very familiar, especially for ConfigMgr administrators. Just take a look at the log folder.
Windows RT
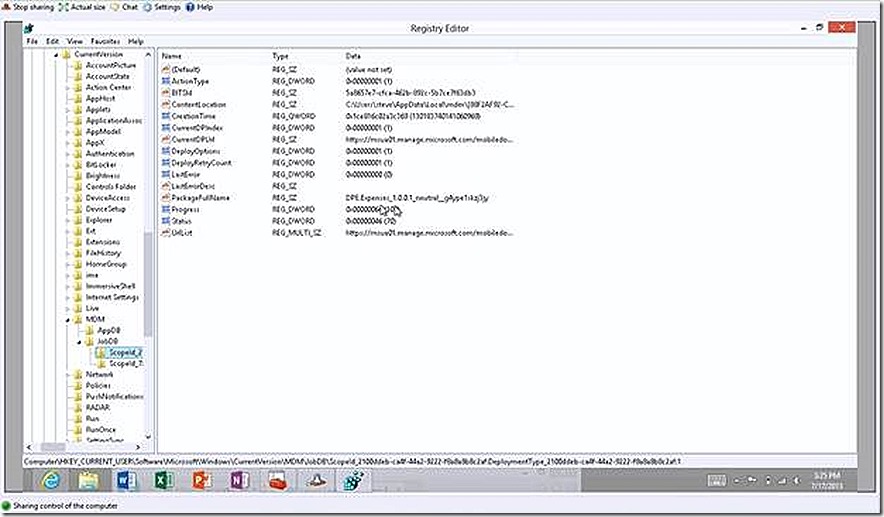
Windows RT devices are managed through native management API’s built into the operating system that Windows Intune is able to use. Accordingly, there is no Windows Intune agent to install on Windows RT but we do have some troubleshooting information available to us should we run into problems. Just take a look in the registry on a Windows RT device and navigate to the MDM key. Here you will see data regarding each individual job that has tried to install on the device. In our case we have installed two apps, one Deep Linked and one custom – and we have two jobs listed in the registry. If we look at our custom app install we see several registry values here - one of interest is LastErrorDesc. In this case there is no information here because my app installed successfully. If it hadn’t the detail explaining the failure would be populated here. As an example, when I was working through my certificate problem the error showed up here confirming my certificate chain couldn’t be validated.
Apple
For troubleshooting Apple devices the utility I’m told is useful is the iPhone Configuration Utility for Windows. I’ve not used the tool but you can find it at https://support.apple.com/kb/dl1466.
And that’s it, take a look at Windows Intune – it really is flexible and capable and well worth the time to evaluate!
Talk back to me by leaving feedback!