Configuring an Evaluation Windows Intune Standalone Deployment
So you’ve heard about Windows Intune and are ready to setup a lab to test it out. Question is, where do you start? How do you use this cloud based service to manage your on-premise PC’s or devices? What are the requirements? Do you have to sync your Active Directory into Intune? Do you need Windows Azure for storing software you may want to deploy? WHERE DO YOU START?!?!?! All good questions, and ones I wrestled with when I first setup my lab.
The goal of this post will be to walk you through setting up Windows Intune in a lab environment with some tips and tricks along the way that hopefully will save you some time. In this post we will cover basic Windows Intune setup and requirements and also work through installing some clients and devices. Let’s get started.
The Basics
Before we start actually building anything in the lab let’s go through the basics for Windows Intune.
What is Windows Intune?
Windows Intune is a public cloud based PC and device management platform that provides management in the following areas:
· Security and Compliance Management
- Software Update and Patch Distribution
· Policy Management
- Endpoint Protection for PC’s
- Self-service Portal for installing company applications
· Personalized application delivery
Windows Intune supports management of both PC and mobile devices. Specific Windows Intune management capabilities may vary depending on the specific managed device.
Why use Windows Intune?
Devices are ubiquitous in today’s computing world and BYOD (Bring Your Own Device) is something all IT organizations will need to contend with in some way. Having the ability to manage those devices while still allowing the user to ‘own’ the device is critical to having a fine tuned and productive environment and also ensuring the best user experience.
Windows Intune is all about managing devices that have the ability to connect to the internet. Windows intune can work totally standalone and can also be integrated with ConfigMgr 2012 SP1. When integrated with ConfigMgr 2012 SP1 through the ConfigMgr 2012 SP1 connector you will have a single pane of glass for managing both the PC’s (Windows, Mac, Unix/Linux servers) in your ConfigMgr environment and also the devices. But this post doesn’t focus on ConfigMgr integration so enough said about that for now!
In addition, Windows Intune is a cloud based service. As such, the pace of innovation and ability to bring new features/options to bear is much greater than that seen in the average on premise IT environment.
The Windows Intune Subscription
Windows Intune is a cloud service and requires a subscription to use. Before committing to purchase a Windows Intune subscription it’s a good idea to take a test drive by signing up for a 30-day trial subscription. This will give you a good amount of time to kick the tires, see how the Windows Intune management processes work and test out a good array of devices and users. And, hopefully, the details to come in this article will help address some of your questions along the way and further optimize the time you spend evaluating Windows Intune vs. digging for information!
The process of acquiring a trial subscription is easy, just go to https://www.microsoft.com/en-us/windows/windowsintune/try.aspx and sign up.
A couple of questions came up when I was setting up my lab that might be useful to you as well.
Do I need a Windows Azure subscription to use Windows Intune
I a word, no. I got myself into this question when I started thinking about synchronizing my Active Directory users with Windows Intune. My thoughts let me to think I somehow needed Windows Azure in the picture to allow directory synchronization to work. You don’t. I also considered whether I might need Windows Azure to load content that I planned to distribute to my Windows Intune clients. Again, no. Windows Intune has inbuilt mechanisms that allow directory synchronization and also provides it’s own storage space for content you may wish to deploy. The thing that likely caused me to question whether Windows Azure was needed is the fact that in ConfigMgr you can setup a cloud based distribution point. To do so you need a Windows Azure subscription since that is where the cloud based distribution point is hosted.
How many Windows Intune instances do I need?
This is a great question and for me really stems from the fact that I wanted to configure both a standalone Windows Intune test environment and a ConfigMgr integrated Windows Intune test environment. A single Windows Intune environment cannot serve both purposes and, once configured, you can’t later decide to switch the environment from one configuration to the other. So, for my test lab I needed two test installations, one for standalone and one for ConfigMgr integrated.
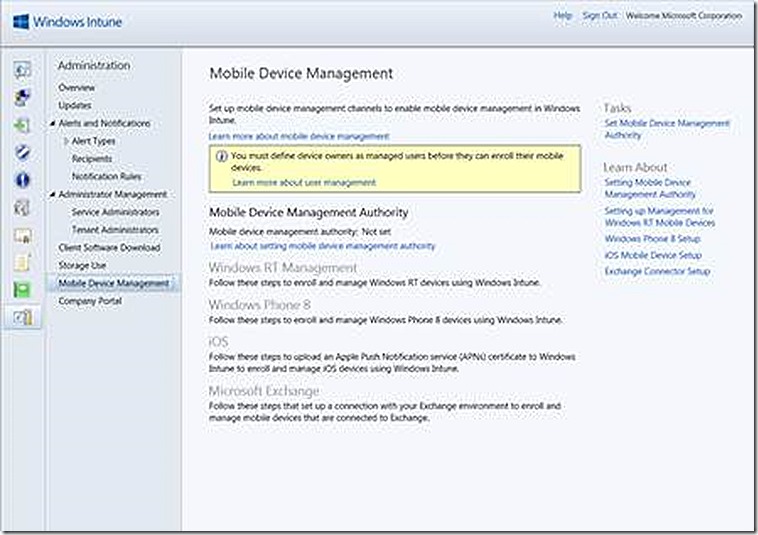
This option is available on the administrator node under Mobile Device Management. The option appears as follows prior to configuration.
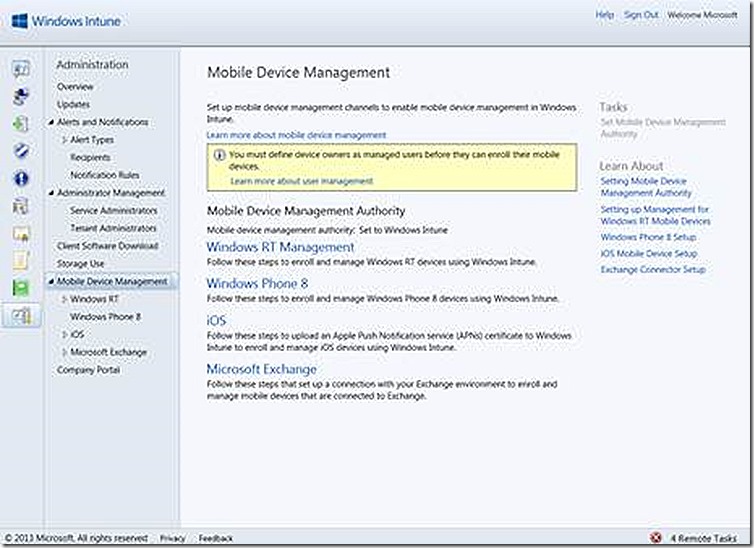
After I’ve chosen standalone mode, the option appears as follows. NOTE: If you will be choosing ConfigMgr Integrated that configuration is NOT done here – instead, setup the ConfigMgr connector in ConfigMgr itself which will implement this configuration for you.
Still on the topic of how many Windows Intune instances are needed we also need to consider scale. A single Windows Intune instance (Tenant) is able to support up to 5000 PC devices. If you need to support both PC’s and devices as well as the various users who may be using those those devices then a single Tenant is able to support 4000 users and 7-8000 devices (mix of traditional PC and device). These numbers are correct as of this blog posting but always check to validate as these numbers are subject to change as future Windows Intune updates are released.
Supported Configurations and Clients
Windows Intune supports both PC and device clients. The current list of supported platforms is found at https://technet.microsoft.com/en-us/library/jj676630.aspx and https://technet.microsoft.com/en-US/library/jj733623.aspx
Windows Intune Setup & Configuration
Enough of the formalities, let’s get to the fun part – setting up Windows Intune in our lab. This section will walk through the various sections of the Windows Intune consoles. We won’t dive deeply into any one part but just want to give a flavor of what is available. When we get to the administration node of the admin console I will show how to configure a PC, iPad and Windows RT tablet for client management. Let’s get started!
The Windows Intune Consoles
The first step is to login to my windows Intune environment. This assumes I have completed the step to acquire a test subscription.
Admin Node
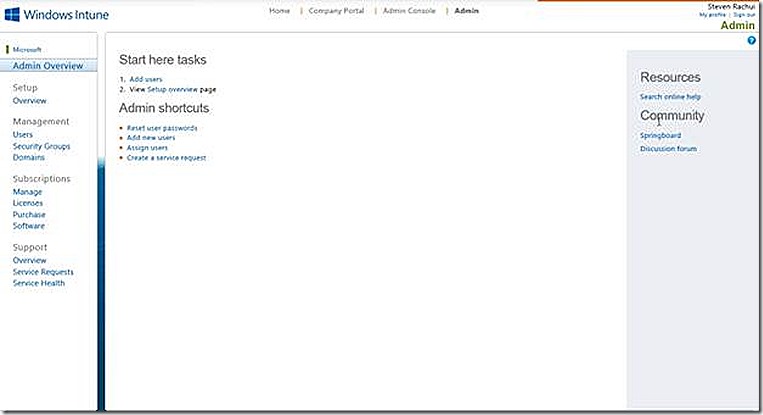
Once logged in we are presented with the start page, as shown. This page is where you add users to the Windows Intune environment, access and configure the Company Portal and launch the Administrator console. There is a also a good amount of documentation for using Windows Intune that is linked from the pages presented both here and in the administration console.
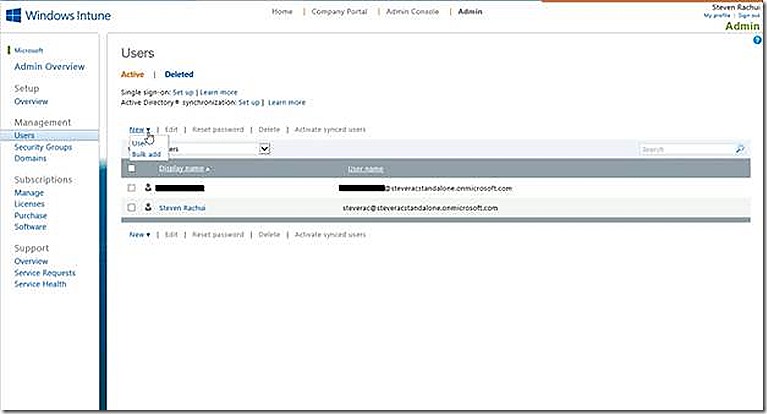
A key section on the Admin page is the Users node. At the risk of being Mr. Obvious here, the Users node is where you add Users that will interact in the Windows Intune environment.
There are a few choices to make here. First, do you need to add users at all? In all scenarios you will need to add at least a few users – in some cases more. Users specified here will be those that can be flagged as having access to the Intune environment to perform various administrative actions. In addition, users are added for the purposes of management. Users are associated with devices when those devices are under management (enrolled) by Windows Intune. Remember, when managing a non-PC device all management is done in the context of the user that owns the device rather than the device itself!
So how exactly do you add users to this node? The most straight forward way is to manually add the user. In my example you see two users have been added. For testing and limited use cases this is fine. In full production deployments you likely will want to leverage users that already exist in your Active Directory environment. This is done by configuring directory synchronization, a topic I don’t cover in this blog post but is fairly straight forward to configure. Once directory synchronization is operational then all of the users that synchronize as part of that process will show up here. Once visible here the users will be AVAILABLE to enable for management but will not be enabled by default. This allows you to decide which users should be managed and which should not. Enabling a synchronized user for management is done by placing check marks besides the user(s) and selecting to Activate from the menu, as shown.
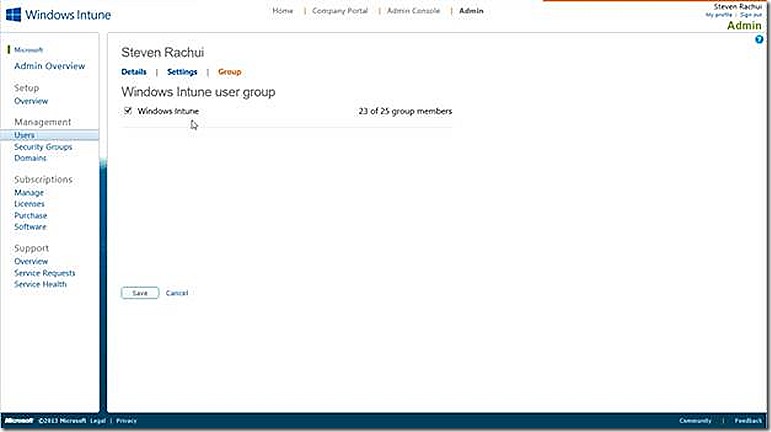
This node is also where various administrative tasks are available – such as resetting the users password, deleting a user and editing the users properties. If a user is selected (click on the user name) the details for that user are displayed, as shown. Note the three tabs available here, details, settings and group. The group node is shown and is important because this is where a user is selected to either be a part of the Windows Intune user group or not. In order for a user to participate in Windows Intune management they MUST be a member of this users group. If they aren’t then the user won’t be able to enroll their devices for management! If you see an error message during enrollment that looks permissions related and you can’t figure out why, check to make sure the user is in the Windows Intune users group!
So, the Users node is important!
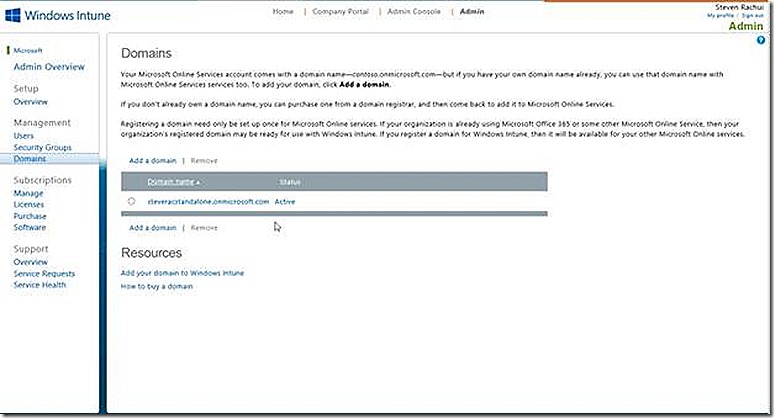
Further options available on the left side include the ability to add and manage security groups within Windows Intune and to specify domains that are managed by Windows Intune. The domains tab is where you specify any domain names you own and wish to manage. In my case I only have a single domain, the steveracstandalone.onmicrosoft.com domain that is assigned when setting up my Windows Intune subscription. If I had configured directory synchronization and wanted to flag that domain for management, I would make sure it is added on the domains node, as shown.
Note: A domain name added here MUST be one that can be validated from the internet. This adds a bit of a wrinkle when trying to test in a lab which is why I have avoided directory synchronization in my standalone environment.
Admin Console Node
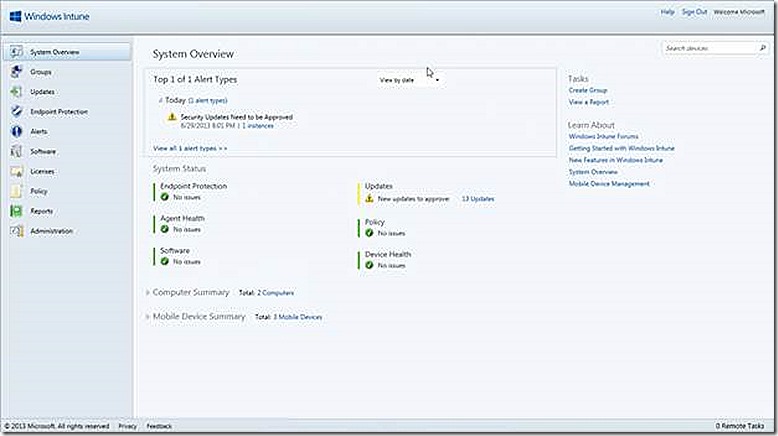
So let’s move on to the Admin Console Node as this is where the work of managing Windows Intune is done. The Admin Console Node opens up to the System Overview page. There are a number of options available in the console, all displayed on the left
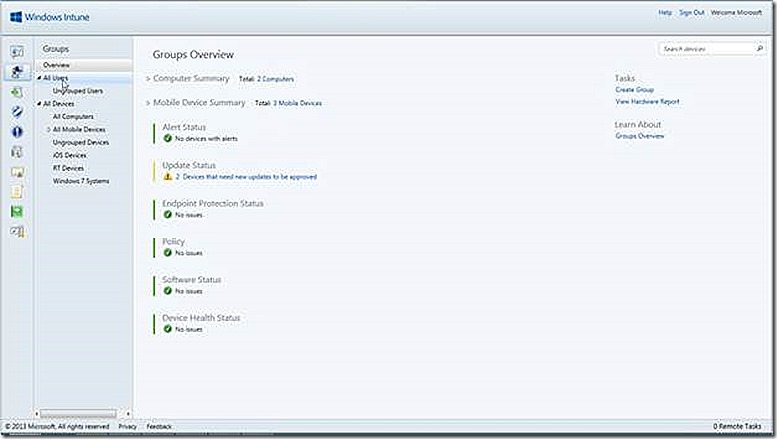
The System Overview node gives a summary of the various manageable Windows Intune components, surfacing alerts that are relevant and also providing links to tasks, such as viewing reports, that may be relevant from here and also key documentation.
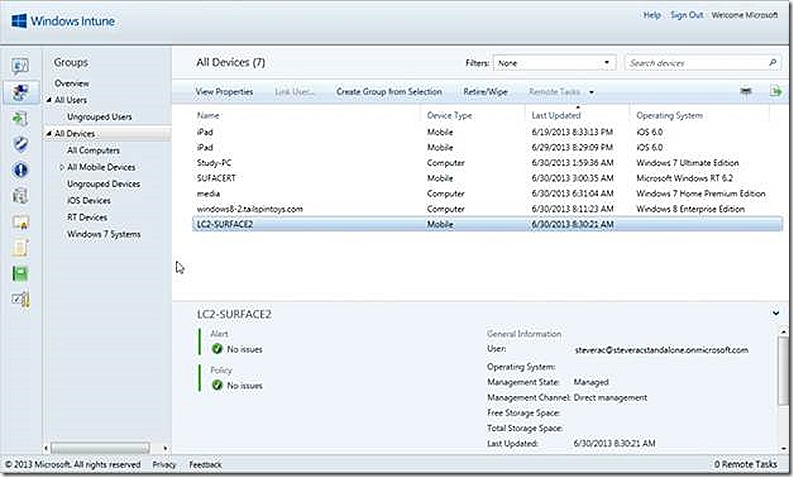
The Groups node allows us to view default groups and create custom groups specific to our needs. Groups are similar to ConfigMgr collections and used to target actions to the group members. There are default groups for Users and default groups for Devices. A couple of custom device groups have been created in the test environment, as shown.
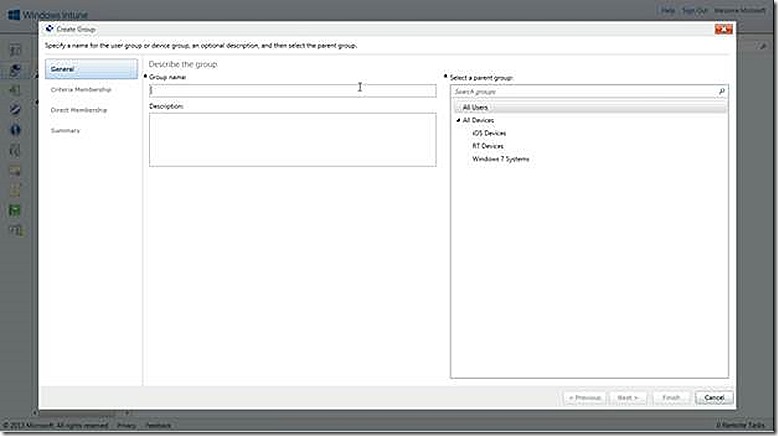
Creating a custom group is easy, simply select to Create Group in the task list and a wizard is presented allowing you to specify the Group Name and Description and also which parent group to use. Further selections in the wizard allow specifying either criteria based group membership or direct membership for groups. In the criteria case the options will vary depending on whether creating a user or device group. For user groups the options for filtering membership are either to include based on security group or manager. For device groups the options for filtering membership are organization unit or domain membership. The criteria options for devices is shown.
The Direct membership option is the way to go if you want to manually add users and devices to groups and manually maintain. Note:: Users and devices cannot co-exist in the same group!
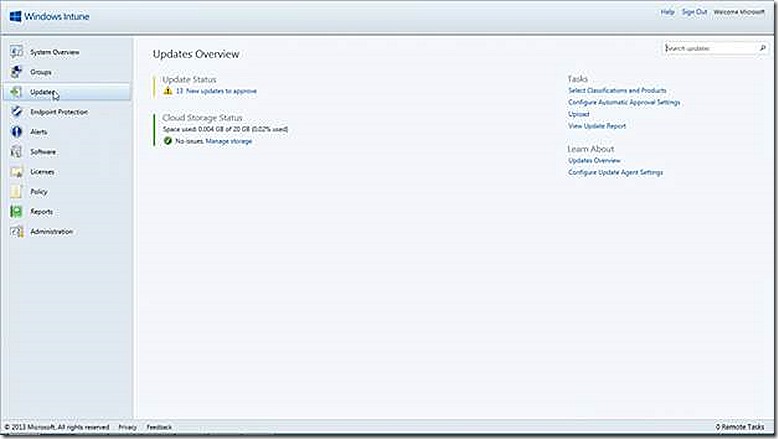
The software updates node is where management and deployment of software updates takes place. From the main page there is a link that allows selecting the software update categories and products and also the automatic approval settings. We also have summary views of any updates that require approval and more.
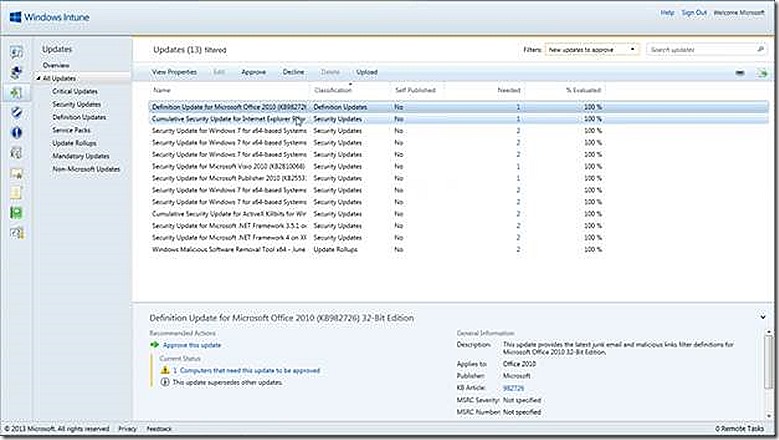
By clicking on the link showing 13 updates needing approval I am taken to a page allowing me to either approve or decline the updates. There is even an upload link here that will launch a tool allowing you to upload a custom (non-Microsoft) update that can then be deployed to systems. This option ins similar in nature to System Center Updates Publisher available for ConfigMgr environments.
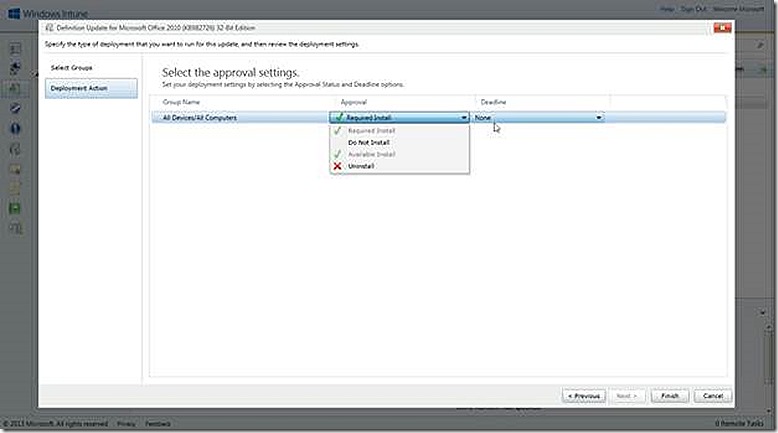
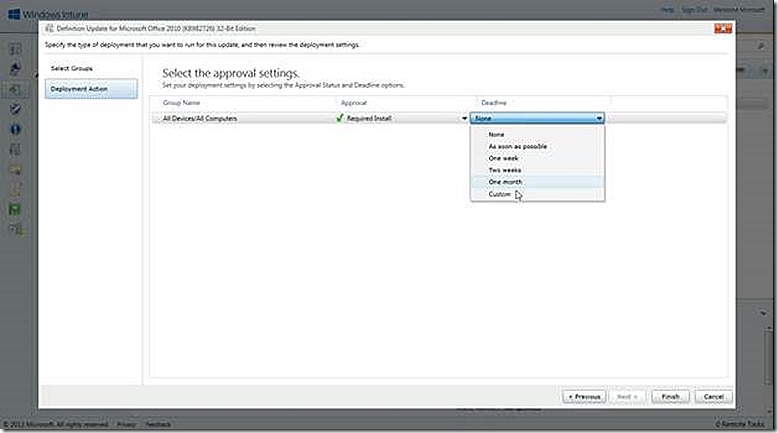
If I click approve a wizard launches that allows me to specify a group that should be targeted with the update(s) and then what action I want to take for the deployment.
The Endpoint protection node provides an overview of Malware and Computer status and provides links to documentation about Malware and Endpoint Protection. Endpoint protection is available for PC’s only and is enabled by default through configured client policy which we will discuss further shortly.
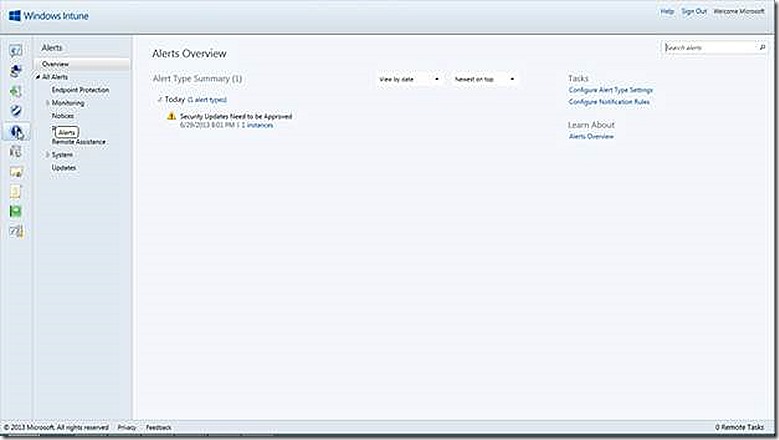
The Alerts node is where any types of issues in the environment are surfaced. As shown earlier, some alerts are also shown on the overview and other pages but this is where they originate. From this page administrators configure rules that define which alerts trigger an email and also customizations to the default alerting settings, such as whether a given alert is disabled and any custom severity information.
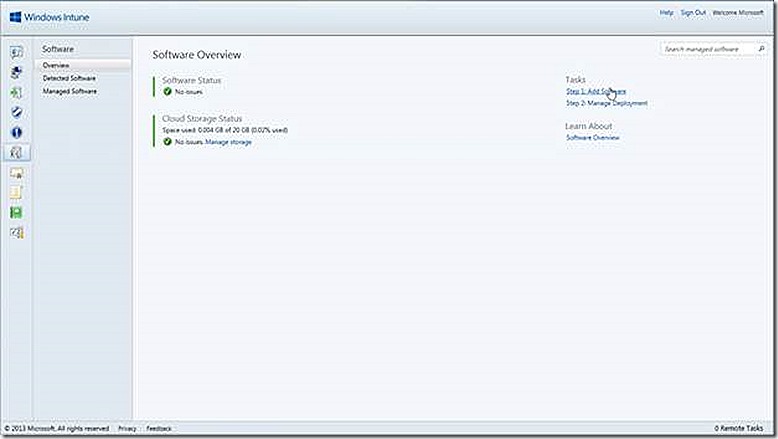
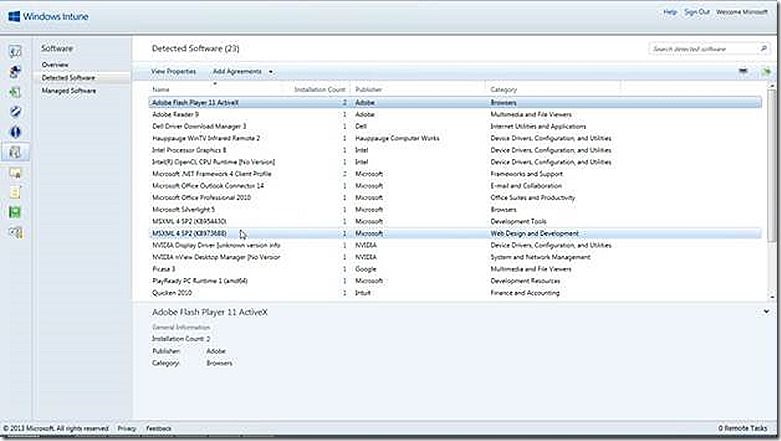
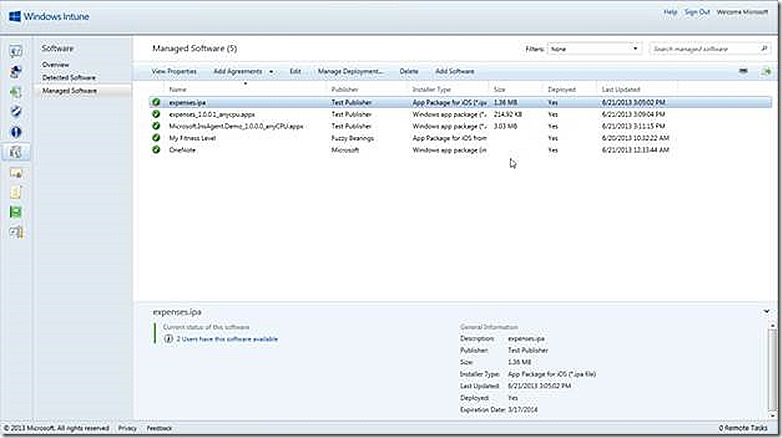
From here we finally arrive at the software node. This is where any custom software deployments are managed, whether the deployment is sent to a PC or device. The task list includes an option to add software to the Windows Intune environment. This option will launch a wizard that will walk through configuring a deployment and uploading the content. Once software is added it is available for management under the Managed Software node. Any software that is detected on managed devices is shown on the Detected Software node, all as shown below. A future blog post will provide examples of installing software across various device types.
The Licensing node is where we are able to import volume license agreements from Microsoft and others, create license groups, view purchase reports and more.
The Policy Management node is where various policies that need to be in place on managed PC’s and devices are configured. From this page we can either add new policies or view existing policies. Policies are broken down in 4 categories
Mobile Device Security Policy – Security settings specific to mobile devices
Windows Firewall Settings – Settings specific to configuring Windows Firewall settings
Windows Intune Agent Settings – Settings specific to configuring the Windows Intune PC agent
Windows Intune Center Settings – Settings that customize the Windows Intune Center on PC’s
The policies that are defined in the default templates are deployable as is but can also be used as a basis for building customized policy settings that can then be deployed to select groups of users or devices, as appropriate.
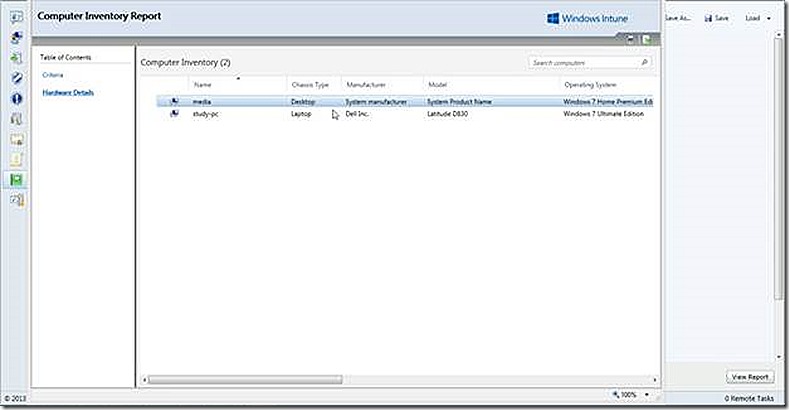
The Reports node provides default reports for Software Updates, Detected Software, Computer Inventory, License Purchasing and License Installation. These reports are displayed by clicking to the appropriate category and then running the report of interest and clicking through the details. A sample inventory report is shown.
The administration node is for activities such as reviewing software updates, tracking cloud storage usage, reviewing alerts and notifications, configuring service and tenant administrators and also managing the PC and device enrollment settings. As you work in the Windows Intune console you will see how your selections will redirect you to other nodes to view detail. As an example, consider alerts. The alerts node allows interaction with the alerts that have been generated but to see detail the view is actually redirected to the administrator node.
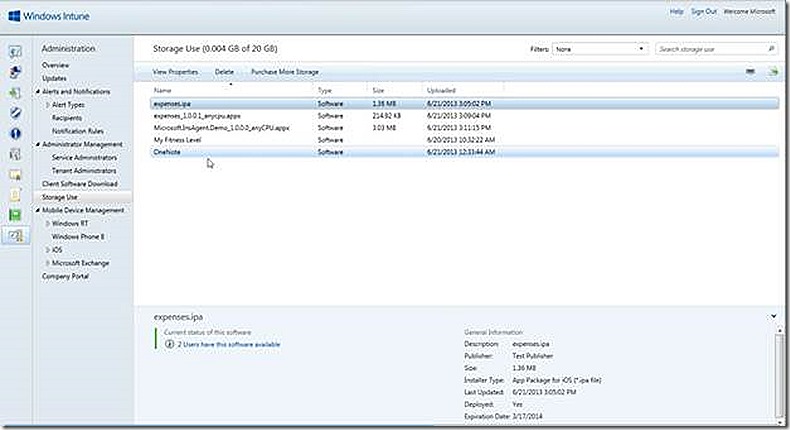
Note that in the storage use section I have configured five test deployments. But also note that only three of the five deployments show as consuming any storage space. Why? The reason illustrates the types of deployments possible – custom deployments or deep linked deployments. Custom deployments are those that deploy custom applications to a PC or device and, accordingly, require storage space for publishing the source files. Deep linked deployments are actually pointers to applications that are already published in a software store, whether the Windows store or Apple store. Since the deep linked applications are coming from an existing store there is no storage space required from Windows Intune.
Device enrollment
The administration node is where client deployment and enrollment is configured. We will focus on three examples – deploying a PC client and enrolling a Windows RT and iPad device. I don’t have a Windows Phone 8 device enrolled because the process is somewhat similar to enrolling Windows RT and there is a cost associated with enrolling Windows Phone 8 devices in order to obtain the needed certificates. Further, there is a tool that allows testing of Windows Phone 8 defices when managed through a ConfigMgr integrated experience. Details are available at - https://www.microsoft.com/en-us/download/details.aspx?id=39079. I also do not have an Android device in my environment for two reasons - I don’t have an Android device for testing and, more importantly, the Android management story at the time of this post relies on Exchange ActiveSync only.
PC Client Deployment
The PC client software is available on the Client Software Download node. Simply download the PC client software and deploy to PC’s you wish to manage via Windows Intune. The process used to deploy the software is up to you, whether manual, email link, Group Policy, whatever.
With the PC client software downloaded simply run through the installation on a PC you wish to manage. Note that the Windows Intune client software cannot be installed on a system that is running a ConfigMgr client so make sure you remove the ConfigMgr client first if it exists.
Run Windows Intune setup from the extracted client zip files obtained from Windows Intune and run the associated .MSI to install the Windows Intune client. The setup process requires no user input, just launch, step through the wizard and that’s it.
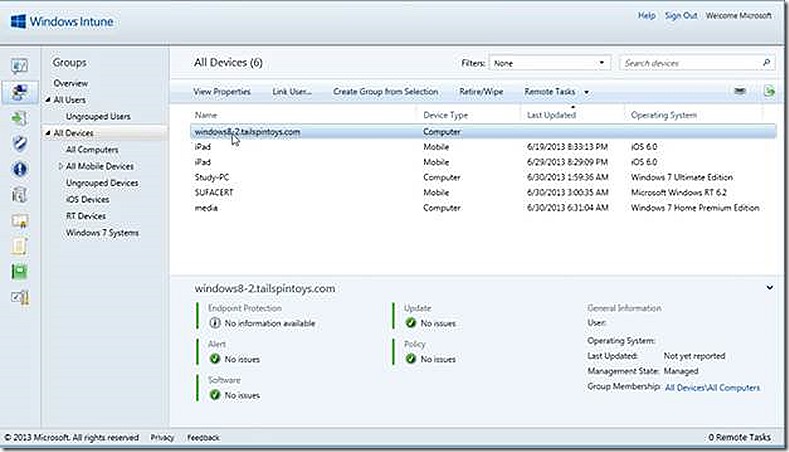
Once installed the Windows Intune client connects up with the Windows Intune service and the PC now shows up and is ready to manage.
Windows RT Enrollment
Enrolling Windows RT devices requires a bit of configuring in Windows Intune first. There are several options we need to discuss.
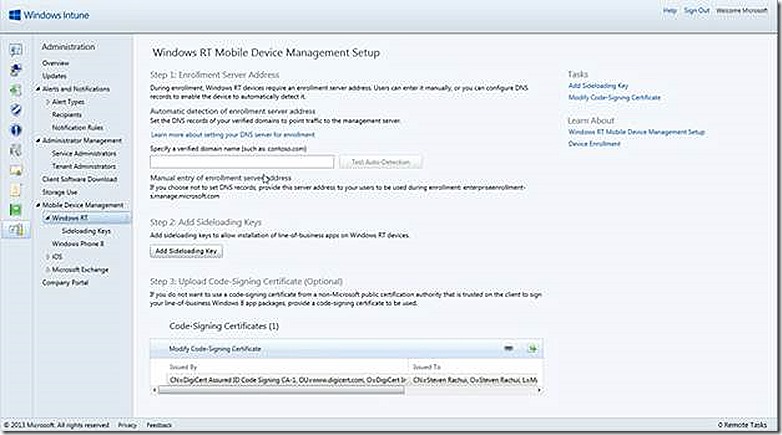
Specify a verified domain name
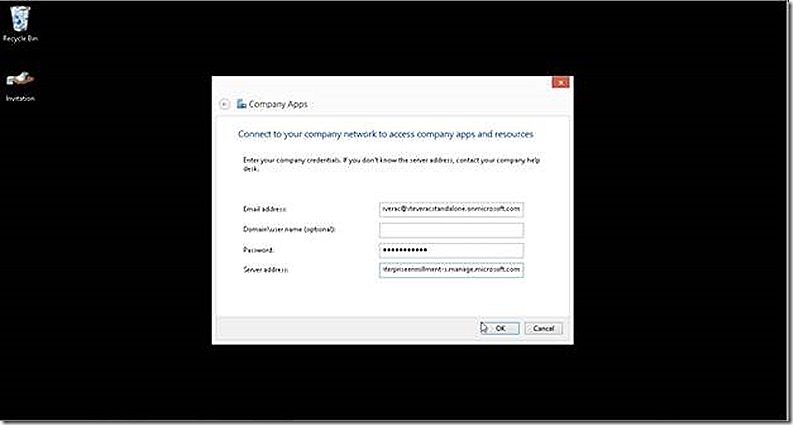
If you own a domain name in addition to the onmicrosoft.com that is supplied when subscribing to Windows Intune you can specify it here. Doing so will streamline the process when users enroll their Windows RT devices. Not having a validated domain name, such as in the case of a lab environment, will not prevent enrollment. The enrollment process will simply require an additional step by connecting to enterpriseenrollment-s.manage.microsoft.com, as we will see.
Add Sideloading Key
As described below, a Sideloading Key is required in many circumstances to facilitate loading custom applications onto Windows RT and Windows 8 systems. For completeness, Sideloading Keys are also required in some cases for deploying modern apps to Windows Server 2012 systems – but since server systems are not supported in Windows Intune they are not part of the discussion here.
OK, so we know we need a Sideloading Key. What IS a Sideloading Key and why do we need it? Great question. A Sideloading key ‘activates’ a Windows RT or Windows 8 device so that custom built modern applications can be loaded onto these devices, whether the loading is done through Windows Intune or any other mechanism. The Sideloading key is per device and not per application being deployed to the device. Think of the Sideloading key as the mechanism that approves a device for installing modern applications that are not already in the Windows store. In addition, a single Sideloading key can be obtained and used to approve activate sideloading on multiple devices.
The following is a list of devices and whether or not they require a sideloading key.
Domain joined Windows 8 Enterprise – no sideloading key needed
Non-domain joined Windows 8 Enterprise – sideloading key IS required
Windows 8 Professional – sideloading key IS required regardless of whether domain joined
Windows RT – sideloading key IS required
Code Signing Certificate
A code signing certificate is used to ‘sign’ any application that will be deployed to the Windows RT device. This ‘signing’ process validates the source of the application and ensures security of the target device. A code signing certificate from any commercial certificate authority is fine as is one issued by your own internal certificate authority. Regardless of where the code signing certificate is obtained the certificate MUST be trusted by the Windows RT device in order to be used.
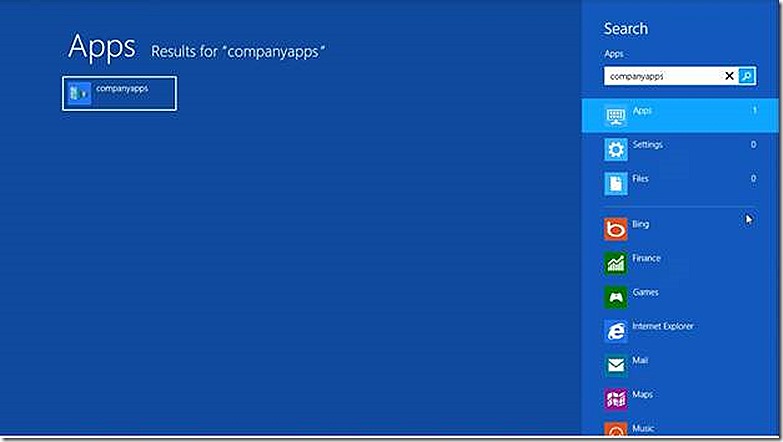
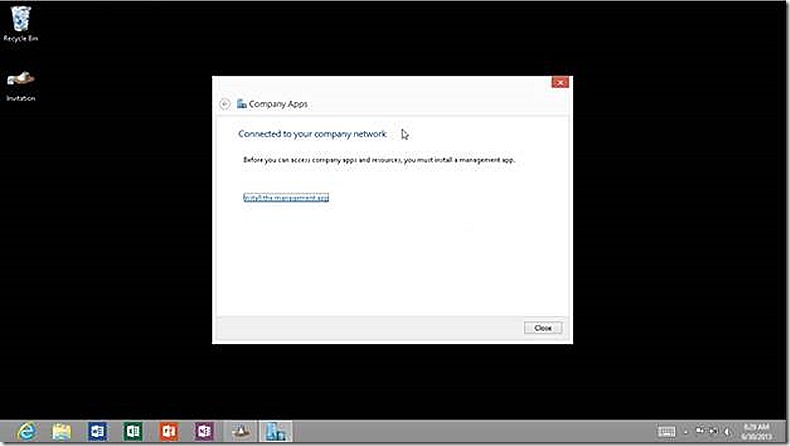
When enrolling a non-PC device remember that the user account used for enrollment is associated to the device and that user account is what Windows Intune uses to target the device for management going forward. Once Windows Intune is configured then it is very easy to enroll the Windows RT device. All that is required is to launch the built-in companyapps application. Note: This application will not appear until you type the full name into search.
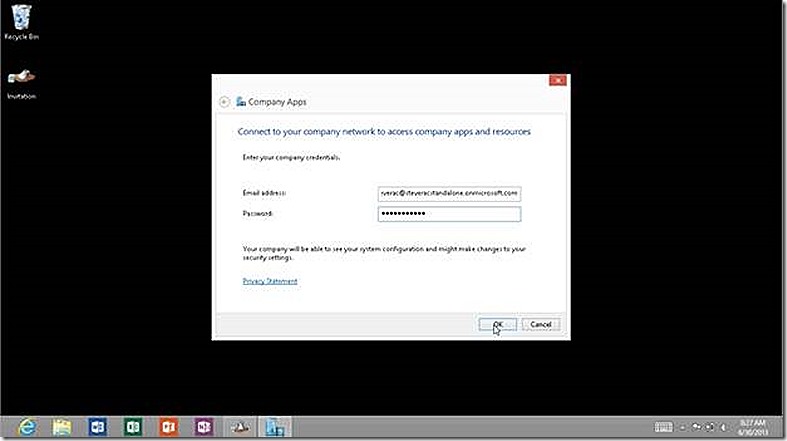
In Companyapps you are at first only prompted for an email address for the user who is enrolling the device and who is approved in Windows Intune. If you have a validated domain name configured then the enrollment process begins when you click OK.
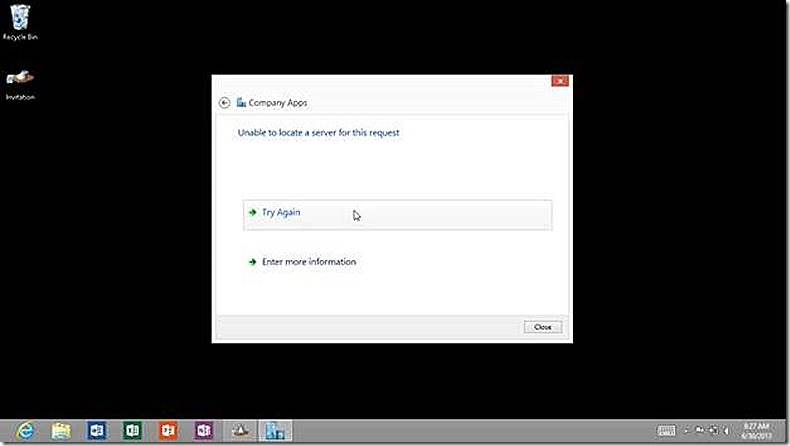
In my lab environment I don’t have a validated domain name so get an indicator that more information is needed. I select to Enter more information and supply the name of the enrollment portal.
Now when we click OK the RT device will churn for a several seconds and if all goes well we see that the device is now successfully enrolled and now you can click the link to install the Company Portal app. If you get an error at this stage then validate the user account being used is configured in Windows Intune and is part of the Windows Intune user group, as discussed earlier.
As easy as that, the Windows RT device is managed by Windows Intune.
iOS enrollment
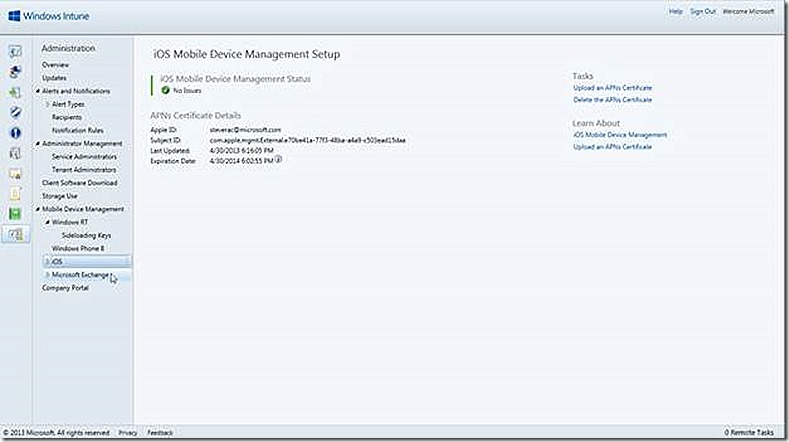
Enrolling an iOS device requires an Apple APN certificate. This certificate is provided by Apple and is free. Simply follow the prompts in the Windows Intune console for instructions on how to request and install the issued certificate.
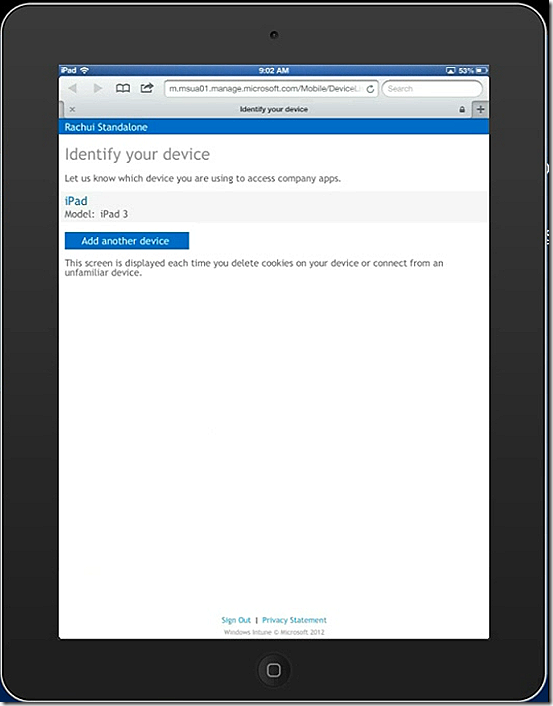
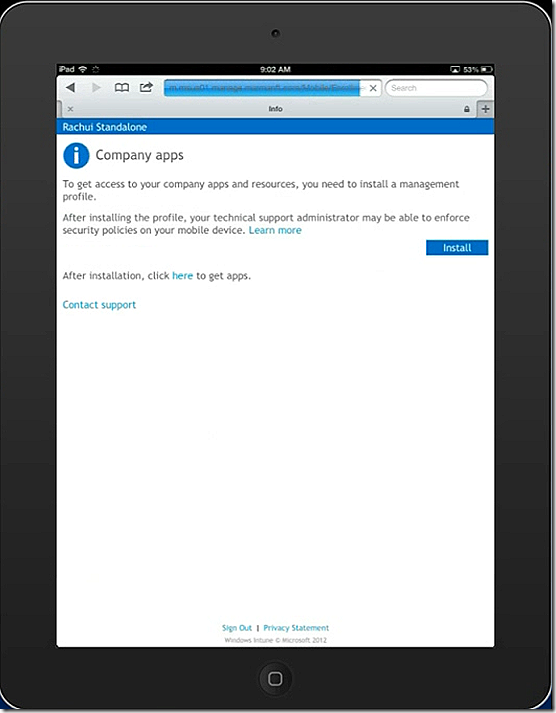
To enroll an iOS device, in this case an iPad, launch your browser and navigate to m.manage.microsoft.com, select to add the device and the enrollment process starts. In my case I already have an iPad associated with the user name so this iPad is considered an additional device.
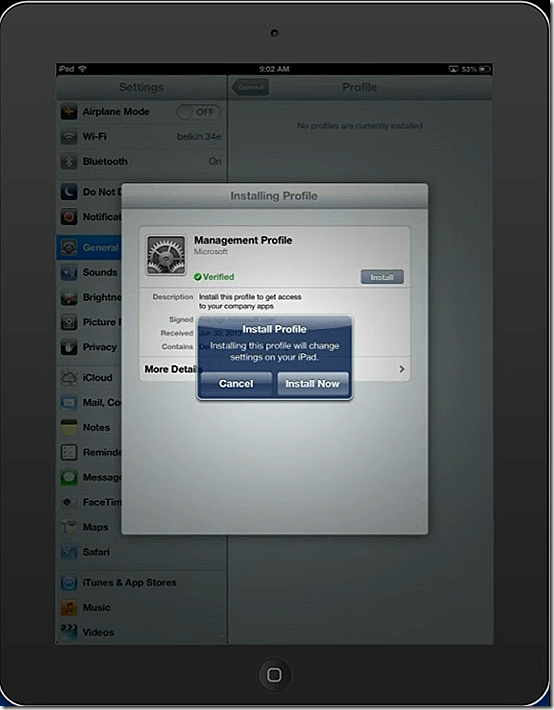
I select to Install the management profile.
I approve the install
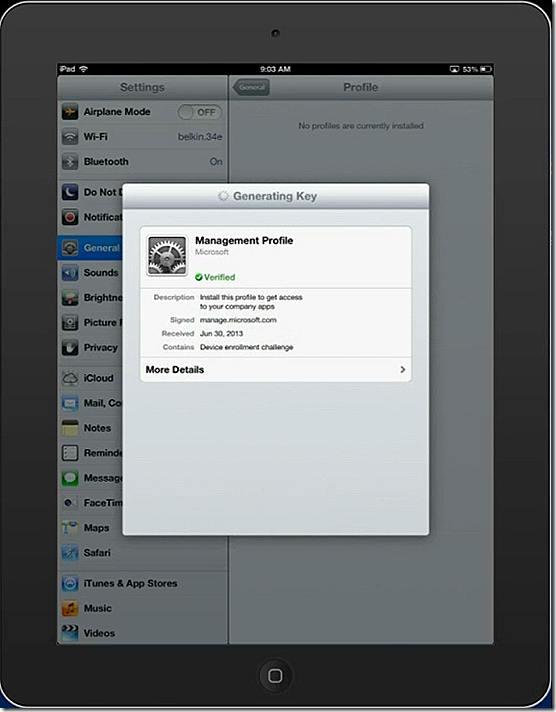
The required keys are generated. During this process an additional prompt is displayed to the user to approve the process.
With the keys generated the device is now enrolled.
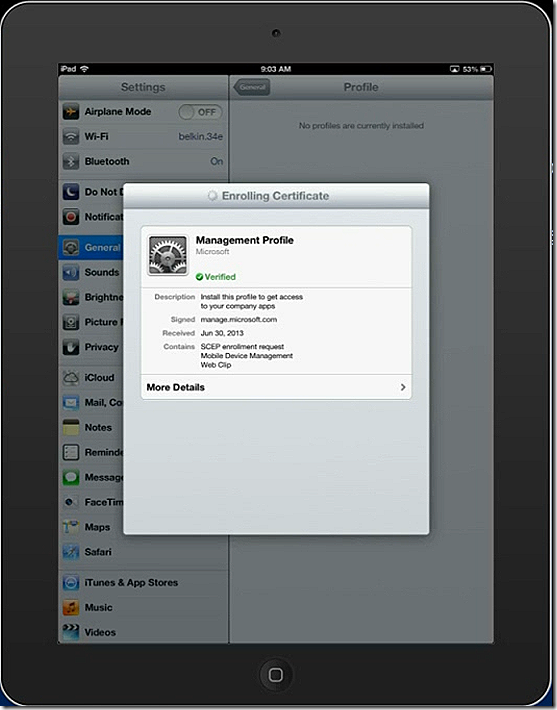
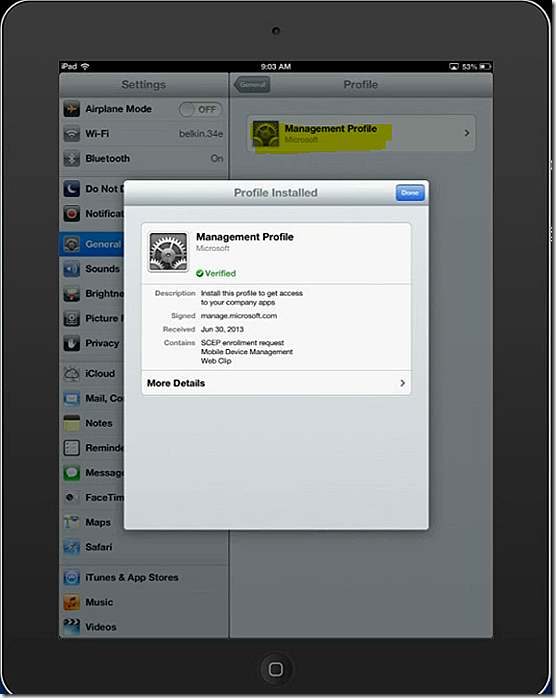
And finally the management profile is installed. Note the new management profile that has shownup on the iPad.
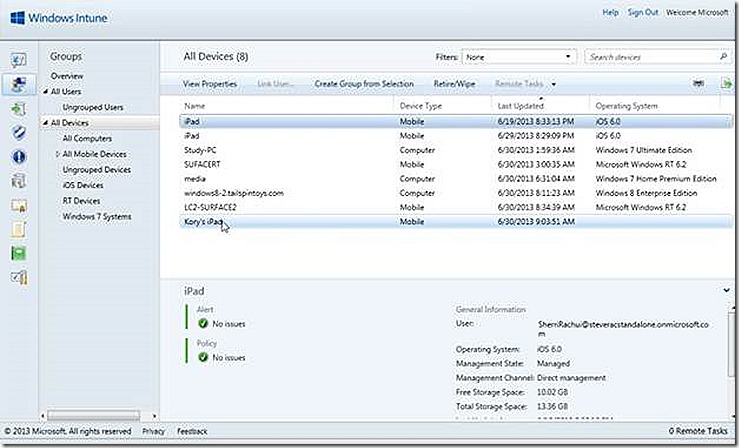
And that’s it, the iPad is enrolled! Looping back to the Windows Intune console we see the iPad is now listed. The device I used is a loaner device thus the personalized name.
Conclusion
And that's it, my test lab is now setup and I’m ready to test out managing my devices! A future blog post will detail that process as I work in my lab. Hopefully the information presented here will be useful to kickstart building your own lab!