Is there any debug logs or tracing logs can help us to monitor certificate importing or EFS decrypting?
This is a recent question I saw ...
You can track detailed EFS events such as EFS decrypt\encrypt and EFS engine cert enrollment via the EFS debug logging in Vista.
In addition – Vista has new DPAPI logging for auditing its usage ( DPAPI is what EFS uses to protect its keys so you should see some data for a key import \export ) you can enable this via the method outlined here:
https://blogs.msdn.com/spatdsg/archive/2007/05/11/New-Auditing-in-Vista.aspx
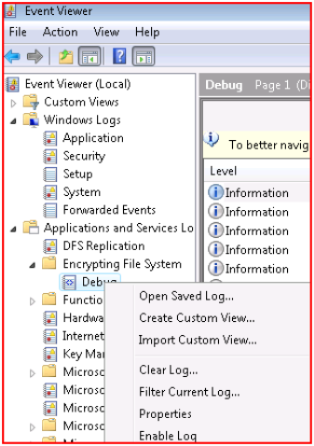
Here is the EFS debug logging….
Enable advanced EFS logging via the eventvwr -- ( click on "enable log" )
Tests I ran…nothing super technical so I am not 100% sure of when and where we log it all in the grand scheme of things, play with it some if you want a specific event flowchart.
Encrypt a file when there is no EFS key – it automatically got one from the Ent CA in my domain:
Event posted:
Log Name: Microsoft-Windows-EFS/Debug
Source: Microsoft-Windows-EFS
Date: 8/6/2007 1:56:30 PM
Event ID: 260
Task Category: None
Level: Information
Keywords:
User: CRISCO1\administrator
Computer: VistaCrisco.crisco.com
Description:
1.3634: Attempt to create a new EFS key
Log Name: Microsoft-Windows-EFS/Debug
Source: Microsoft-Windows-EFS
Date: 8/6/2007 1:56:36 PM
Event ID: 256
Task Category: None
Level: Information
Keywords:
User: CRISCO1\administrator
Computer: VistaCrisco.crisco.com
Description:
EFS key promoted from current key. CertValidated: 2, cbHash: 20, pbHash: E2 B3 9B 13 ED C6 4D 2B D6 17 8D 68 63 FE 89 48 1A 37 E3 83, ContainerName: d7bbcfe2c68036677fc606f5309b0453_79f3ab01-e697-496e-afe2-672634d9bf6a, ProviderName: Microsoft Enhanced Cryptographic Provider v1.0, DisplayInformation: Administrator( administrator@crisco.com ), dwCapabilities: EKU_EFS KU_GOOD_FOR_EFS KEYSPEC_EXCHANGE MASTERKEY RSA_ENCRYPT IS_TIME_VALID KEY_LARGE_ENOUGH , bIsCurrentKey: TRUE, eKeyType: RSA KEY
For an encrypt \ decrypt operation we seem to log the following so the two event highlighted look to be a promising identifier.
4.11824: attempting to validate EFS stream
4.11926: EFS stream validated
Good luck to you…
spatdsg