Using UNIX Attributes tab without installing IdMU
Using UNIX Attributes tab without installing IdMU
Starting with the Windows Server 2003 R2 release, Microsoft has made it clear that the AD Lookup feature would be the preferred direction to go for identity mapping between Windows and *nix when it comes to NFS access - both server and client. AD Lookup uses the information populated in UidNumber and GidNumber attributes with user and group objects in AD to map the identity information between these platforms.
There's no tool that comes with NFS components in Windows we can use to populate this information. We have to either use scripts/ADSIEdit.msc to populate these attributes or use the infamous UNIX Attributes tab that comes with IdMU. This tab gets added to the ADUC snap-in when Server for NIS service is installed. This tab is easy to use and does the job using the familiar ADUC interface.
How to install UNIX Attributes tab?
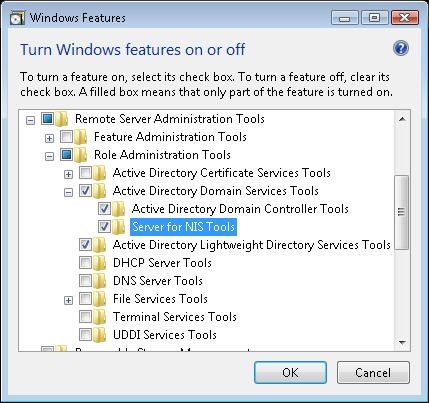
On the client workstations that use Windows XP, you can run the IDMU.EXE that ships with Windows Server 2003 R2 Media 2 under the ADMIN folder to install this tab and use the local ADUC snap-in to manage this information. On Windows Vista, you can install this extension by installing the Server for NIS Tools under Turn Windows features on or off > Remote Server Administration Tools > Role Administration Tools > Active Directory Domain Services Tools -
On my Windows 7 Ultimate RC, I don't see a way to install this tab. I hope it gets added by the time it's released.
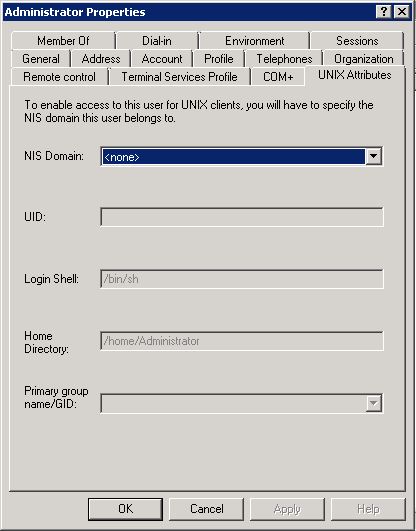
Now, even when this extension is installed using one of the above methods, it doesn't work because the NISPROP.DLL file - the DLL behind the UNIX Attributes tab - expects the NIS domain information to be present in AD while that is added only when Server for NIS component is installed on at least one of the DCs in an AD domain. If that information is not present in AD, the fields in the tab remain disabled -
How to get it working?
While that sounds like a big problem - it's not difficult to get it working without installing any of the IdMU components. All that is required is to execute the appropriate version of NISCNFG.EXE.
On the Windows Server 2003 R2 Media 2, you can find this file under the CMPNENTS\R2 folder. Just copy and execute this console app from a command prompt.
While on a Windows Server 2008 or Windows Server 2008 R2 system, you can find this file on the system itself by running the following command -
DIR NISCNFG.EXE /S/A
On my test boxes, it returned the following paths -
C:\Windows\winsxs\x86_microsoft-windows-server-for-nis_31bf3856ad364e35_6.0.6001.18000_none_48fb4ed1643883aa
And,
C:\Windows\winsxs\amd64_microsoft-windows-server-for-nis_31bf3856ad364e35_6.1.7100.0_none_160ce2b671abc629
- on a Windows Server 2008 and a Windows Server 2008 R2 RC systems respectively.
Please note that executing this binary doesn't produce any output or error message. The command will wait for some time while it is adding the necessary information in AD under System > RpcServices > YpServ30 container and then it comes back to the command prompt. You might also see another container called DefaultMigrationContainer30 on same level as System container.
NOTE: The user executing this binary needs to have administrative privileges in order to allow this tools to make the necessary changes.
This tool doesn't extend the AD schema in any way since all the necessary classes and attributes are already present in Windows Server 2003 R2 and later schema. It merely adds some containers and objects for the UNIX Attributes tab to function properly.
As you can see in the above screen shot, when we use this UNIX Attributes tab to populate the UNIX UID and GID information on user and group objects, it also adds some other information like NIS domain name, shell and home folder. Apart from the values present in UidNumber and GidNumber attributes, other information is redundant for AD Lookup and are used only when UNIX systems are authenticating against AD using NIS or LDAP/Kerberos.
The Technet content on Active Directoy Lookup and IdMU can be found on the following links -
- Specify How Server for NFS Obtains Windows User and Group Information in Windows Server 2008/2008 R2
- Configuring Services for Network File System to Use Active Directory Domain Lookup in Windows Server 2003 R2
- Integrated Identity Management in Active Directory Domain Services in Windows Server 2003 R2
- UNIX Interoperability in Windows Server 2008/2008 R2