Configuring User Name Mapping - Part 3 (Advanced Mapping)
Configuring User Name Mapping - Part 3 (Advanced Mapping)
Simply said - when you map users and groups manually with their UNIX counterparts, it's called Advanced Mapping.
From the last post on User Name Mapping, you may be aware that Simple Mapping automatically creates maps for all users and group who have the same names in your Windows and UNIX environment. It is possible that you aren't lucky enough to have the same names for users and groups in both the environments. Sometimes, you would want better control on this aspect and may not want to map all the users and groups automatically.
Advanced mappings can be used in such cases. Easy to configure - turn off Simple Maps in User Name Mapping Configuration and map them manually. You can read this page to see how it can be done in a Windows Server 2003 R2 environment.
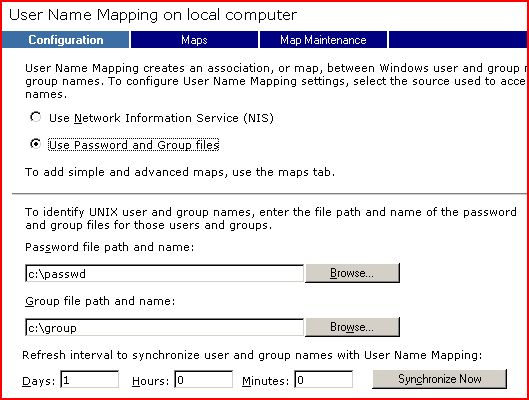
In Services for UNIX 3.x environments, you can do by using the Services for UNIX Administration console. Select User Name Mapping in the left pane, define the UNIX data source and click on Apply -
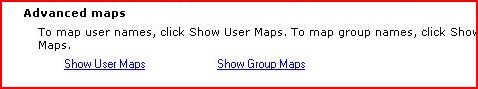
To proceed further, click on Mappings in the right pane. You can now click on Show User Mappings or Show Group Mappings depending on what you want to do -
Now, you can display the users/groups in both Windows and UNIX side. Select the objects in both lists and click on Add. You're done.