How to View a Report in WACA?
Web Application Configuration Analyzer v1.0 is the latest tool released by our team that scans a machine for deployment best practices. Here is how you can use this tool to view a scan report which provides resolution details for failed rules.
1. From the presented Launchpad under the “Quick Actions” Section screen click on the “View scan results” link or go to “File” menu and select “View scan results”. You can also get to this screen by clicking on the “View Report” button after a scan, which will automatically select that scan for the report.
2. From the first drop down box, select a server to view a scan result. The drop down box displays all the server names for which results have been generated by the tool. Upon selecting the server name, the list box displays the scanned dates and times starting with latest date and timestamp.
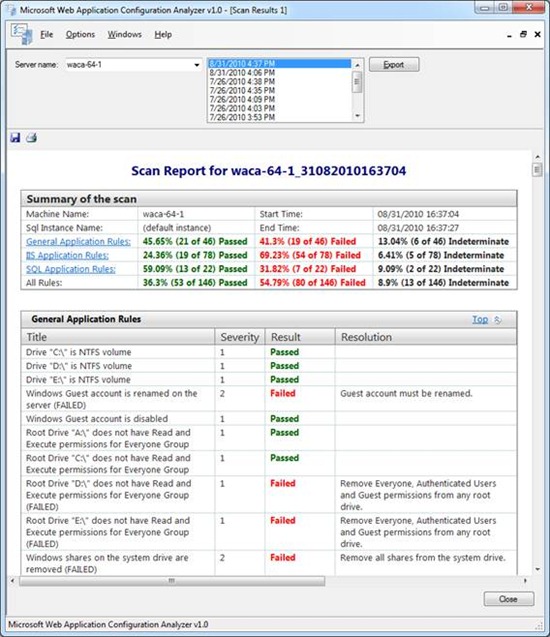
3. The report is divided into multiple sections. You can navigate to corresponding section by clicking the links in summary table. There are four sections for every report. First is the Summary, which tells you about the machine and its specific attributes. This section also serves as the index allowing you to select a link to jump to that specific section. The next section is the General application Rules. This is where all rules pertaining to a machine regardless to the machines purpose. The next section contains the IIS Application rules. If a user knows this machine is an IIS box then this section should have all the security rules for IIS in one contained section. The last section is for SQL server. Assuming the server is a SQL server machine all rules pertaining to SQL Server will be in this section.
4. Results from scanning a machine falls into one of four states: Passed, Failed, Indeterminate and Not Applicable. Passed indicates the rules was tested and based on WACA’s scan discovery the rule passed. Failed indicates after the rule was scanned for the discovery was the rule failed the test. Not Applicable state is used when specific application such as IIS or SQL Server is not present on the target machine. Indeterminate state is applied when a specific rule cannot find the underlying data due to missing information to process the rule. For example, Indeterminate state could be returned for the “Unnecessary service (Alerter) is not running” rule if the service itself is not present on the target machine. Investigate indeterminate rules by using the descriptions and resolutions from Excel export.
5. Severity and resolution provide additional context to the rule and only failed rules include resolutions to fix the violation. Context may determine whether a failure in WACA is a bug to be fixed. Some checks, for example, are applicable for servers facing the extranet, but would be considered false positives for any other environment. The description for the checks provides guidance for these scenarios.
6. Exporting to Excel and using the Filter feature can help with quickly identifying and managing failures.
Thanks
Anil RV