What’s happening with CAT.NET 2.0?
RV here...
Our pre alpha release included a command line tool showcasing newer version of CAT.NET based on tainted data flow analysis engine using Phoenix compiler infrastructure. It also included a configuration analysis engine which was capable of identifying insecure configuration in .config files. We are actively working on the potential beta release of CAT.NET tool focusing mainly on the core analysis and user experience areas. Here is a quick update on changes.
- User Experience
- Integration with Visual Studio 2010 code analysis infrastructure as FxCop rules
- Easy analysis using FxCop command line or UI interface or VSTS Team Build.
- Core Analysis
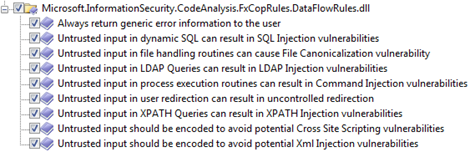
- Updated tainted data flow analysis engine to track both tainted operands and source symbols
- Lesser false positives and false negatives by detecting sanitizers and constant variables and instructions that affect the data flow.
- New Data flow rule to detect XML Injection attacks
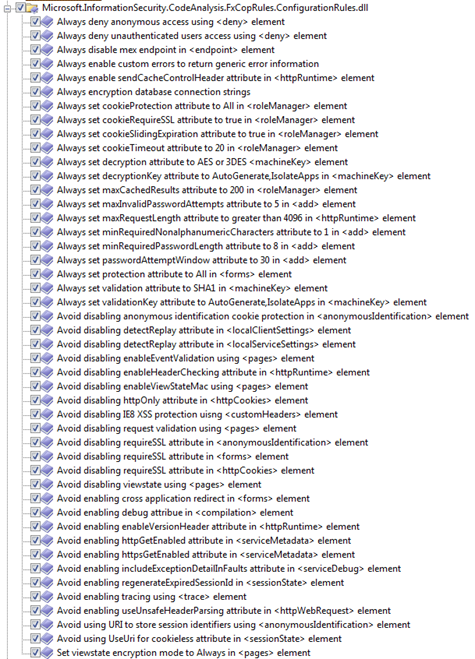
- Updated configuration rules engine to detect clear text connection strings and credentials
- Updated rules to detect insecure defaults, for example minRequiredPasswordLength attribute of membership providers add element.
- Configuration rules updated to detect @page directive configuration overrides.
Here is a list of FxCop CAT.NET data flow rules.
Here is a list of FxCop CAT.NET configuration rules.
With tighter integration with visual studio code analysis the changes are going to make it much more easier to use CAT.NET analysis to detect application level security issues.
Happy New Year!