How to Configure WPL v1.0 SRE
RV here...
With the release of Web Protection Library v1.0 (WPL) Security Runtime Engine (SRE) has been significantly updated. It now includes a SQL Injection Detection module which can detect certain attack vectors. It also include re-designed configuration editor which enables you to easily configure SRE. The following easy steps let you configure your application to use SRE.
Step 1 : Edit Configuration
First step is to configure your application web.config file to enable SRE modules. Star the configuration editor by going to Start –> All Programs –> Microsoft Information Security –> Web Protection Library v1.0 and clicking on SRE Configuration Editor shortcut.
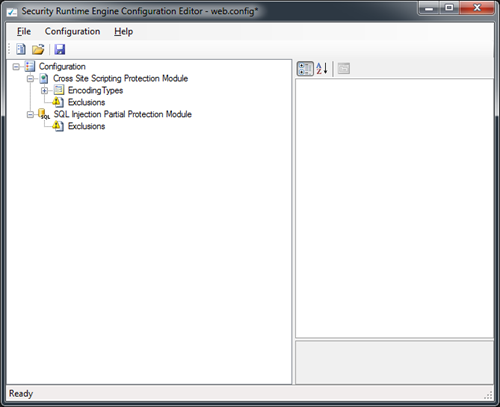
The left side tree includes list of processors configured in the current config file. By default a blank web.config with all processors are loaded in the editor. Click on File –> Open to open an existing web.config file to add the processors. The configuration tree would be empty. Right Click on the “Configuration” node in the tree and select “New –> Cross Site Scripting Protection Module” to add XSS protection module to the application. Similarly, add the “SQL Injection Partial Protection Module” to the configuration node. Click on the save icon or select File –> Save to save the configuration. The following sections are added to the configuration file.
- configSection/section nodes for defining processor configurations
- httpModules/add for enabling the modules
- processor configuration sections
Step2 : Copy SRE Binaries
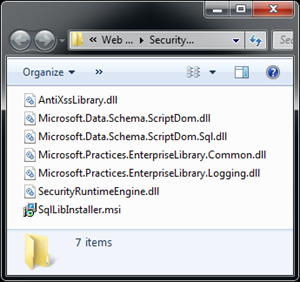
Once the configuration is in place, ASP.NET will now try to resolve the httpModules defined in the configuration. In case of 64-bit windows Go to %ProgramFiles(x86)%\Microsoft Information Security\Web Protection Library v1.0\SecurityRuntimeEngine or 32-bit Windows go to %ProgramFiles%\Microsoft Information Security\Web Protection Library v1.0\SecurityRuntimeEngine directory and copy all the .dll files to \bin folder of your application. Here is a brief description of files found in this directory.
Don’t copy the SqlLibInstaller.msi as this is going to install the SQL Parser libraries on the machine.
Step 3: Test
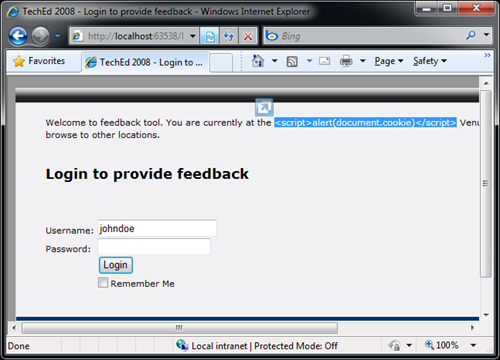
Once you copy the binaries, SRE should automatically encode the controls being rendered on the page. It should also detect an SQL Injection Attempts as shown below. In case of XSS attack, inputs are automatically encoded by the Anti-XSS processor.
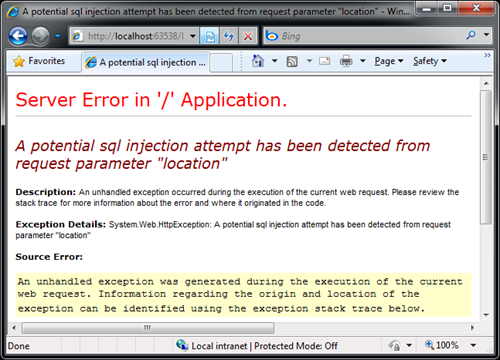
Similarly following exception is thrown when SQL queries are detected in the input.
You can handle this exception with custom errors page and provide generic information to the user. As we release new processors in WPL, we will continue to update the blog site with more how to information.