Enabling Azure Disk Encryption for Windows IaaS VMs using PowerShell
In this post, I will enable disk Encryption for a Windows IaaS VM using PowerShell for an existing VM. This is an example with step by step instructions to give you a high level overview. For detailed information on Azure Disk Encryption including prerequisites, supportability and different options to enable encryption , please refer to the links below:
https://blogs.msdn.microsoft.com/azuresecurity/2016/01/22/azure-disk-encryption-white-paper-updated/ https://azure.microsoft.com/en-us/documentation/articles/key-vault-get-started/ https://azure.microsoft.com/en-us/documentation/videos/azure-key-vault-with-amit-bapat/ https://channel9.msdn.com/events/Microsoft-Azure/AzureCon-2015/ACON214
Enabling Disk Encryption for Windows IaaS VMs using PowerShell
Connect to your Subscription
PS C:\WINDOWS\system32> Login-AzureRmAccount
Create a New Resource Group or use an existing
PS C:\WINDOWS\system32> New-AzureRmResourceGroup -Name “skpkeyvaultgroup” -location “East US”
ResourceGroupName : skpkeyvaultgroup
Location : eastus
ProvisioningState : Succeeded
Tags :
ResourceId : /subscriptions/3a0d1a4f-1d45-4dbc-bb68-xxxxxxxxxxxxx/resourceGroups/skpkeyvaultgroup
Create a New Key Vault
PS C:\WINDOWS\system32> New-AzureRmKeyVault -VaultName "skpkeyvault" -ResourceGroupName "skpkeyvaultgroup" -location "East US"
Vault Name : skpkeyvault
Resource Group Name : skpkeyvaultgroup
Location : East US
Resource ID : /subscriptions/3a0d1a4f-1d45-4dbc-bb68-891422694ec1/resourceGroups/skpkeyvaultgroup/
providers/Microsoft.KeyVault/vaults/skpkeyvault
Vault URI : https://skpkeyvault.vault.azure.net
Tenant ID : 9aaa5c65-a5d0-415f-9964-ac32ea83c1b1
SKU : Standard
Enabled For Deployment? : False
Enabled For Template Deployment? : False
Enabled For Disk Encryption? : False
Access Policies :
Tenant ID : 9aaa5c65-a5d0-415f-9964-xxxxxxxxxxx
Object ID : e0a21a69-899e-4f98-bc0d-xxxxxxxxxx
Application ID :
Display Name : satish pandita
(#EXT#@youemailaddresshotmail.onmicrosoft.com)
Permissions to Keys : get, create, delete, list, update, import, backup,
restore
Permissions to Secrets : all
Provision a Key Encryption Key to add a key or secret to the key Vault
PS C:\WINDOWS\system32> $key = Add-AzureKeyVaultKey -VaultName 'skpKeyVault' -Name 'skpFirstKey' -Destination 'Software'
PS C:\WINDOWS\system32> get-azurekeyvaultkey -vaultname "skpkeyvault"
Vault Name : skpkeyvault
Name : skpFirstKey
Version :
Id : https://skpkeyvault.vault.azure.net:443/keys/skpFirstKey
Enabled : True
Expires :
Not Before :
Created : 5/14/2016 3:04:29 AM
Updated : 5/14/2016 3:04:29 AM
To see a specific URI Version
PS C:\WINDOWS\system32> $key.key.kid
https://skpkeyvault.vault.azure.net/keys/skpFirstKey/1fc92a75728c4d389997f
Next Register and authorize an application with Azure Active Directory
Go to Active Directory Tab and add an application (see screen captures below) 
Next click on "Add an Application"
Next Generate the new key and save the key to be generated and click on save button and copy the Client ID and Secret Key, these will be required for enabling encryption 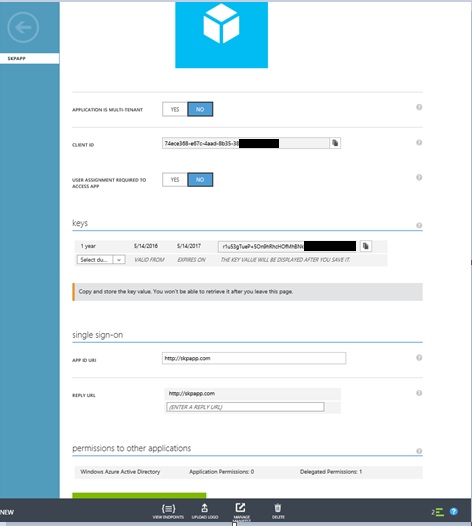
Set Key Vault Access Policy to provide AAD Application the required rights to access keys or secrets in the vault and Enable the Disk Encryption
(in this example my VM "skpvm1" is in "skpvmresourcegroup" and key vault is in "skpkeyvaultgroup")
$rgName = ‘skpkeyvaultgroup'
$vmName = ‘skpvm1'
$aadClientID = "74ece368-e67c-4aad-8b35-38xxxxxxxxx"
$aadClientSecret = " r1u53gTueP+5On9hRhcHOfMhBNkYH8riecKxxxxxxxx"
$KeyVaultName = ‘skpKeyVault'
$KeyVault = Get-AzureRmKeyVault -VaultName $KeyVaultName -ResourceGroupName $rgname;
$diskEncryptionKeyVaultUrl = $KeyVault.VaultUri
$KeyVaultResourceId = $KeyVault.ResourceId
Set-AzureRmKeyVaultAccessPolicy -VaultName $KeyVaultName -ServicePrincipalName $aadClientID -PermissionsToKeys all -PermissionsToSecrets all -ResourceGroupName $rgname;
Set-AzureRmKeyVaultAccessPolicy -VaultName $KeyVaultName -ResourceGroupName $rgname -EnabledForDiskEncryption
Set-AzureRmVMDiskEncryptionExtension -ResourceGroupName skpvmresourcegroup -VMName $vmName -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId;
The enabling of encryption will reboot the machine and can can take take 10-15 minutes to finish.
Verify the Encryption status
C:\WINDOWS\system32> Get-AzureRmVMDiskEncryptionStatus -ResourceGroupName skpvmresourcegroup -VMName skpvm1
OsVolumeEncrypted : True
OsVolumeEncryptionSettings : {
"diskEncryptionKey": {
"secretUrl": "https://skpkeyvault.vault.azure.net/secrets/1528B96D-AA71-4313-AB26-xxxxxxxxxxx
D4/77b94cbbb0ed4d73b9109ef0bxxxxx6",
"sourceVault": {
"id": "/subscriptions/3a0d1a4f-1d45-4dbc-bb68-8914xxxxx/resourceGroups/skpkeyvaultgroup
/providers/Microsoft.KeyVault/vaults/skpkeyvault"
}
},
"keyEncryptionKey": null,
"enabled": true
}
DataVolumesEncrypted : True
To disable volume encryption
PS C:\WINDOWS\system32> Disable-AzureRmVMDiskEncryption -ResourceGroupName skpvmresourcegroup -VMName skpvm1 -VolumeType All
PS C:\WINDOWS\system32> Get-AzureRmVMDiskEncryptionStatus -ResourceGroupName skpvmresourcegroup -VMName skpvm1
OsVolumeEncrypted : False
OsVolumeEncryptionSettings : {
"diskEncryptionKey": null,
"keyEncryptionKey": null,
"enabled": false
}
DataVolumesEncrypted : False
Few things to note:
- If the OS volume is not encrypted, then the data volumes cannot be encrypted
- If you add another data volume later, You can explicitly run the PS cmdlets Set-AzureRmVMDiskEncryptionExtension with -Volumetype Data or ARM template to turn on encryption on the newly added data volume or if you reboot the VM. the bitlocker extension will encrypt any un-encrypted data volumes presuming the VM was previously configured to encrypt data volumes/all volumes.
- For bitlocker enabled VMs' you will notice another Volume "Bek Volume", it is local volume in which the BitLocker keys [secret] are stored locally so that the encrypted OS volume can boot on start/reboot etc. This volume is local to the VM and is not persisted in storage
Special thanks to Anand Kumar-Microsoft Azure PFE for reviewing and assisting with this post. https://social.msdn.microsoft.com/Profile/ranand12
DISCLAIMER: This posting is provided “AS IS” with no warranties and confers no rights