Required permissions when calling a Web service using client certificate for authentication in an ASP.NET Web application
A Web service requiring Client certificate authentication is a common scenario.
You may have a client application which needs to send the Client certificate as part of the web request for accessing the web service.
This client application may be a Windows/Console application or another Web application.
Often you will get into issues wherein you are able to send Client certificate as part of the web request from a windows/console app but not from another web app. The primary reason for this could often be around Web app not being able to send the client cert to the target Web service.
This can happen for multiple reasons, in particular account under which Web app is running doesn't have enough permissions to access the Client cert in its local certificate store.
Refer to this excellent kb for this for more details.
In this post I want to highlight ways in which you can grant access to the Web application account to access the Client certificate in its local machine store.
When we have to send client cert as part of the web service call from a web app we need to ensure that the client cert is installed in the Local Computer -> Personal Store on the local box (where Web app is running). By default you will see the client cert installed in the Local User Store for the user who requested and installed the cert on the machine. You need to ensure first that the client cert is installed on the Local Computer Store instead of the Local User Store and then follow any of the methods below to grant access to the private key for the account (under which your web app is running).
Method 1:
The above article kb gives an example of granting access using the Microsoft Windows HTTP Services Certificate Configuration Tool
> WinHttpCertCfg.exe -g -c LOCAL_MACHINE\MY -s " IssuedToName " -a " AccountName "
for e.g.
> WinHttpCertCfg.exe -g -c LOCAL_MACHINE\MY -s " IssuedToName " -a "Network Service"
There are other ways in which you can achieve the same result. This feature is in fact built in on Windows Server 2008 within the Certificate mmc console.
Method 2:
Using the WSE X509 Certificate tool (This tool has features that can be used to check certificate properties).
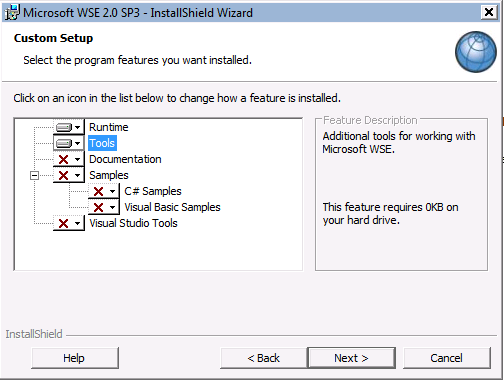
You need to download Web Services enhancements (WSE) 2.0+ SP3 for Microsoft.Net and in the install wizard ensure you select Tools as shown below:
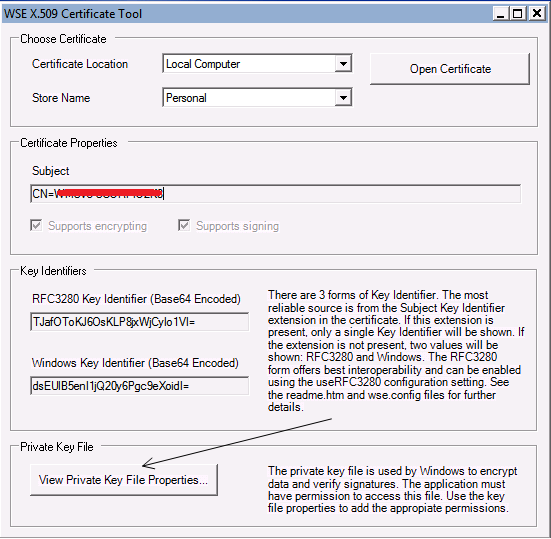
Once installed go ahead and launch the tool. It has a clean UI. You have the option to check certificates in the Local Computer/Current user for the available stores like Personal/Trusted/Intermediate Root CA etc. If you click on View Private Key File Properties (shown below) you can directly modify the permission for private key associated with the certificate. Basically this is just a file under C:\Documents and Settings\All Users\Application Data\Microsoft\Crypto\RSA\MachineKeys on Win2k3 server and C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys on Win2k8 server.
You may want to go ahead and give the Service account under which the web app is running Full permission on this file (modify the permissions from the Security tab).
Method 3:
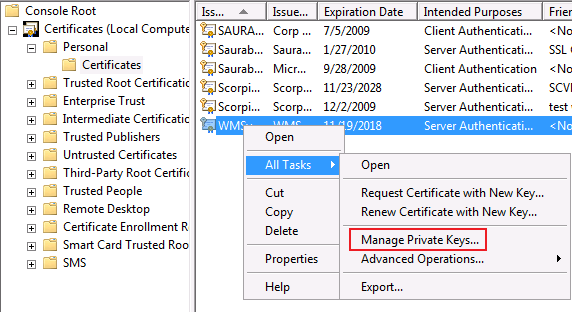
If you are running the web app on Windows Server 2008/Vista there is a far simpler way built in the Certificate mmc.
Right click on the certificate and go to All Tasks -> Manage Private Keys and then give Full permission for the associated account.
Till next time..
Cheers!