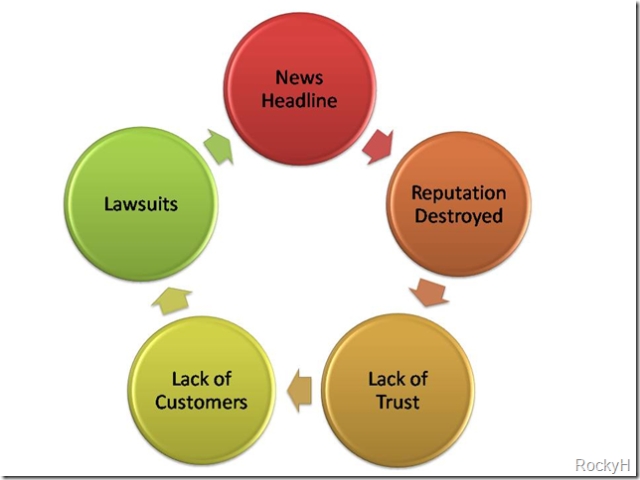
The Vicious cycle
In the IT Security area there seems to be this lack of belief in the old adage, It Can Happen To Anyone. Normally, before a company will get off their collective butts and do anything about their software security, they have to experience an incident. There are all sorts of cliche's we can put here:
- A stitch in time saves nine
- Learn from the mistakes of others
- ad. nauseum
But I think we can agree that cliche's are by their nature things that people tend to think of as well...cliche and don't do anything about. New Flash, cliche's become cliche's for a reason, they usually hold some tidbit of wisdom that is worth paying attention to.
So what does this have to do with the viscous cycle? There is an inevitable series of things that happen after a company experiences a security breach. They are illustrated in the diagram below:
It all starts with a News Headline. As I've said at many of the talks I've given, what I want is to prevent your company from becoming a headline. A semi-wise person once said, "There's no such thing as bad press." WRONG! That only applies to Actors and Politicians. In the IT Industry it's usually all bad press. once the breach leaks into the public eye through press, or regulatory disclosure (https://www.privacyrights.org ) the company and all of it's potential insecure practices come under the microscope. What usually follows is the tossing away of a good reputation.
When the dirty laundry is aired out, the company suffers one of those intangible losses of reputation. In business, more than most places, your reputation is a deciding factor on your success. So if your reputation is destroyed, the domino effect is that you will suffer losses on the bottom line as well. Why does this happen though? After all a reputation is a pretty flimsy thing in today's "less than honorable society so what's the big deal?
If you lose your reputation, your customers, or potential customers will not trust you. It is this golden facet of the relationship with your customers that is so important in today's fast-paced security conscious world. Sure there are some places that don't have to worry about their customers going elsewhere, say the IRS/ATO/DIR (insert the tax collection agency of your choice here). So they probably don't have to worry about this kind of stuff right? WRONG! What happens to them, that is instead of their customer going elsewhere, they undergo one of those new business terms - Reorganization. Either way, you essentially lose out on either potential business, or your job.
So a lack of trust directly relates to a lack of customers. Now this one is pretty simple. No Customers = No Business. However in our ever law-suit-savvy world, there's a new threat emerging.
A lot of people, especially when backed by regulatory red tape like SOx, HIPPA, and others are turning to their lawyers to help 'fix things' when someone experiences a data breach. This usually takes the form of million dollar lawsuits against the companies who experienced the data breach. Of course, when someone sues a big company and gets some money out of it, that makes the news, and we're back at the begriming of the circle again.
So what do we do about this? Well for a long time now we've been hardening the OS layer and the Network layer against attack. To be honest, it's in pretty good shape now. While malicious hackers are very smart, they are like mode code jockeys, lazy. So they tend to go for the weak point, the application layer. No amount of firewalls, IPSec and good intentions are going to protect a company against sloppy insecure programming practices. The Application Layer is the weak link in the chain.
I always fid it a bit ironic that over 70% of the typical IT Security budget is spent on infrastructure, yet over 75% of attacks happen at the application layer. We're spending our money in the wrong place. Infrastructure solutions will always have a problem when it comes to knowing what is acceptable to an application and what is not. No matter how smart the firewall is, it will never know if a SQL string is acceptable input to the application or not. Only the application will be able to inspect and filter the input with any reliability.
We need to focus our attention where it will actually do some good, at the application layer. Don't get me wrong, firewalls, IPSec, and IDS are very good things to have, but they can't be your only line of defense. But we need to concentrate on getting security at the points it's going to do us the most good. There are a couple things you can do to improve your security posture:
- Invest in up-front activities:
- Threat Modeling
- Design Review
- Put your developers through secure coding training
- Use Secure Deployment practices
- Use host level scanning to ensure your servers are configured to security best practice.
Put an end to the cycle!