SharePoint Adventures : Using Claims with Reporting Services
Back in February of 2011, I created a blog that walked through using Kerberos with Reporting Services. Since then, we have moved Reporting Services to a shared service within SharePoint. This changes the game and we are now in the Claims world. I’ve been asked a bunch of times regarding Claims Configuration, and just clearing up some general confusion. I have also presented at PASS on this topic as well, and thought it was time to get the Blog post out there on this topic. This blog will show SharePoint 2013, but the steps are the same in SharePoint 2010. To start, I’ll reference a few other blogs for background that we can refer back to.
Reference Blogs:
My Kerberos Checklist…
What SPN do I use and how does it get there?
SharePoint Adventures : How to identify if you are using Claims Authentication
Isn’t Kerberos Dead?
I’ve heard some comments along the lines of – “Well now that I’m using claims, I don’t need to worry about Kerberos.” This isn’t true. Claims changes the perspective a bit, but if our goal is to get to a back end data source using Windows Authentication, we need Kerberos. Within the Claims/SharePoint Bubble, we don’t have a Windows Token. We have a Claims Token. When we want to leave the bubble, we need to go get a Windows Token. This is done by way of the Claims to Windows Token Service (C2WTS). From there it is all Kerberos. So, everything you know about Kerberos is still relevant. We just need to add a few things to your utility belt.
Shared Service
Starting with Reporting Services 2012, we are now a Shared Service within SharePoint. We are no longer an external service as we were with RS 2008 R2 and earlier versions. This means we are inside of the SharePoint bubble. In the Using Kerberos with Reporting Services, I talk a lot about needing to have the front end SPN’s (HTTP) in place. However, now that we are inside of the SharePoint bubble, we don’t need the HTTP SPN’s any longer. Everything from the client (Browser) to the Report Server, does not require Kerberos any longer. You can still setup Kerberos for the SharePoint Web Front End (WFE), but when we go to hit the Report Server, it will be Claims. Any communication with the Report Server is done via a WCF Web Service and will be Claims Auth. Regardless of how the WFE is configured. So, in this setup, we really only care about the RS Service and going back into the backend. It’s all about Delegation now.
Common Errors
Before getting into the configuration, I wanted to highlight some of the errors you may see that are related to this topic. These are at least ones I’ve seen.
Cannot convert claims identity to a windows token. This may be due to user not logging in using windows credentials.
Login failed for user ‘NT AUTHORITY\ANONYMOUS’
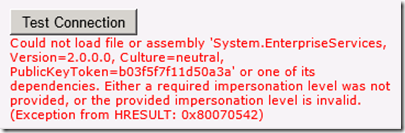
Could not load file or assembly ‘System.EnterpriseServices, Version=2.0.0.0, culture=neutral, <-- see this blog post
Claims to Windows Token Service (C2WTS)
This is where the magic happens. As mentioned above, we are using a Claims Token when we are within the RS Shared Service. We are in the SharePoint bubble. So, what happens when we want to leave the bubble? We need a helper. This helper is the Claims to Windows Token Service (C2WTS). It’s whole purpose in life is to extract the User Principal Name (UPN) claim from a non-Windows security token, in our case a SAML token, and generates an impersonation-level Windows Token. Think Kerberos Delegation. This is actually a Windows Service that sits on the same machine as the service that is trying to call into it to get the Windows Token.
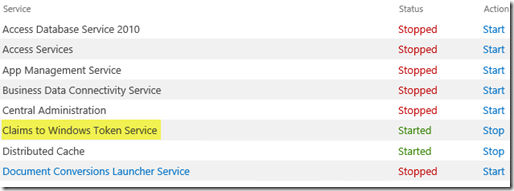
This service is enabled via Central Admin –> Application Management –> Service Applications –> Manage services on server.
Be sure to start it here as opposed to the Windows Service directly. The SharePoint Timer jobs will just stop the service if you start it manually.
C2WTS Configuration
There are a few things that need to make sure that you configure C2WTS correctly. We will have a look at everything except for the delegation piece. We will save that for last.
Service Account
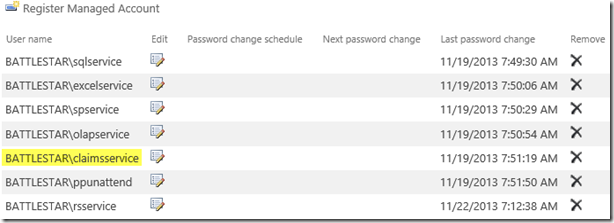
You will need to decide what Service Account you want to use. By default, C2WTS is set to use the Local System account. I’ve seen people use this, and it will work fine. However, I usually don’t ever recommend you use Local System for any Service Account. This is just a security standpoint, and the ideal of least privileged. Local System has a lot of power on the machine. So, I typically recommend a Domain Account to use. On my deployment, I use a Claims Service account that I created. If you use an account you created, you will need to add it as a managed account within Central Admin. This is done via Security –> General Security –> Configure managed accounts.
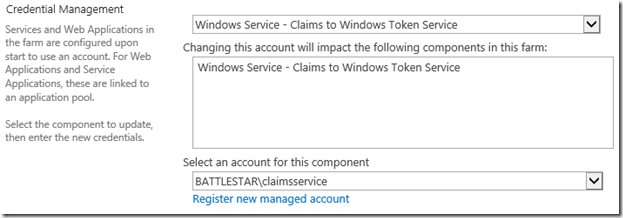
After that is done, you need to change the C2WTS service to use that managed account. This is done via Security –> General Security –> Configure service accounts. Then select C2WTS from the drop down.
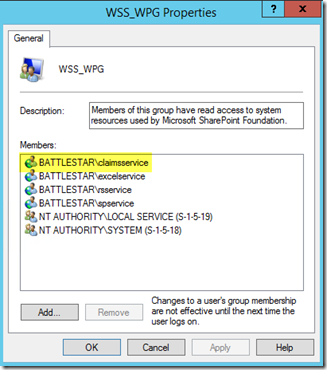
When you do this second step, it should also add the service account to the WSS_WPG local group on the SharePoint boxes.
Local Admin Group
You will need to add this service account to the Local Admin Group on the machine that it will be used on. If you have two SharePoint boxes and one is a WFE and the other is the App Server that will be using it, you only need to do this on the App Server. C2WTS will not work unless it is in the local admin group. I haven’t narrowed down what exact permissions it requires to avoid the local admin group. If someone has figured this out, let me know.
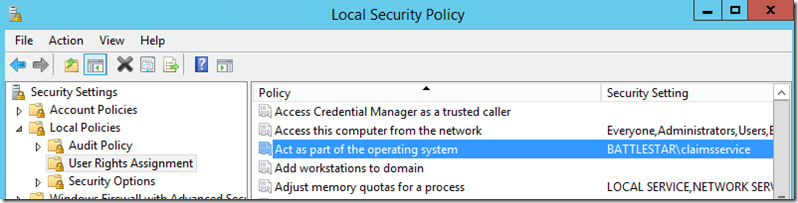
Local Security Policy
The service account you are using needs to be listed in the Act as part of the operating system policy right. Again, this only needs to be done on the SharePoint box that will be using the service.
c2wtshost.exe.config
Remember the WSS_WPG group? This is why we want the service account in that group. The location of this config file is C:\Program Files\Windows Identity Foundation\v3.5. In this config file will be defined who can make use of C2WTS. If your account isn’t listed here, or covered by a group that is listed, it won’t work.
<allowedCallers>
<clear />
<add value="WSS_WPG" />
</allowedCallers>
RS Shared Service Configuration
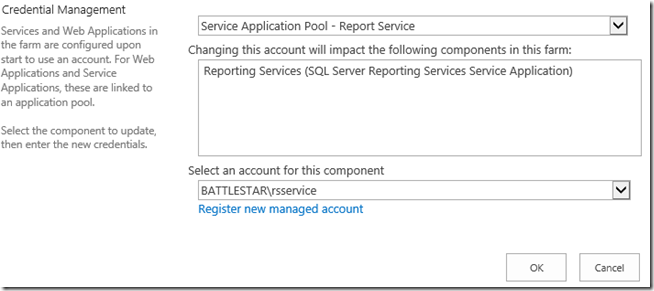
The only real configuration point here is with regards to the service account. Again, I would recommend a Domain Account for use with this. In my deployment, my account is rsservice. We will need to make sure that account is added as a managed account within SharePoint (see above under the claims account). Once that is done, it will be added to the local WSS_WPG group. The addition into the WSS_WPG group allows for the RS Service to call into C2WTS because that group is set in the config file.
We then need to associate that account to the RS Service, if you didn’t already do that during initial configuration of the RS Service.
Delegation
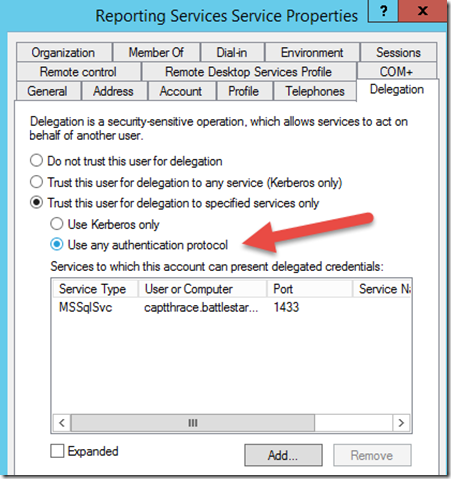
The last part on our journey is configuring delegation. Remember we mentioned that we don’t care about the front end piece of this. So, we don’t need to be concerned with HTTP SPNs at all. We just want to configure delegation from the point of C2WTS and the RS Service. These both need to be configured in order for this to work. They need to match with regards to which service you want to hit. I would start with the RS Service Account, and then make sure that the C2WTS account matches what the RS Service Account has.
NOTE: The C2WTS service may have other services configured that RS doesn’t need. This could be due to other services making use of C2WTS such as Excel Services or PerformancePoint.
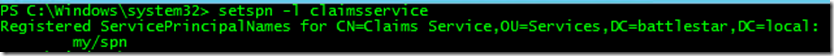
To configure this, we need to go into Active Directory Users and Computers. There are other ways to configure delegation, but this is probably the easiest. Ut Oh! Where’s the delegation tab? The delegation tab will only show up if there is an SPN configured on that account. But, we said we didn’t need the HTTP SPN that we would have with RS 2008 R2. As a result, nothing was configured on the RS Service Account and we don’t see the delegation tab. What’s the fix? Add a fake SPN.
Here you can see I added an SPN called my/spn. This won’t hurt anything and won’t otherwise be used.
For this to work, we need to choose the settings for Constrained Delegation. More specifically we need to enable Protocol Transitioning (Use any authentication protocol). This is because we are transitioning from one authentication scheme (Claims) to another (Windows Token). This also has the adverse effect of limiting you to a single domain for your services and computer accounts. This has changed starting in Windows 2012 R2, but I haven’t tested that yet to see how it works. I’ve read that you can do cross domain traffic with constrained delegation in Windows 2012 R2.
After that, I add the service that I want to delegate to. Basically, what data sources are you hitting with your reports. In this case, I added my SQL Server. This assumes you have your SQL SPN in place. You can reference the other blog posts at the top of this blog if you need assistance getting your SQL SPN configured.
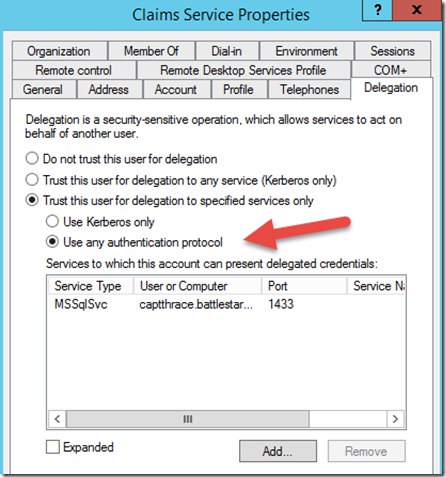
We then need to make sure that the Claims Service matches this configuration. Don’t forget the fake spn on the Claims service account.
And that’s it! After that, we should see that our data source works.
Adam W. Saxton | Microsoft SQL Server Escalation Services
https://twitter.com/awsaxton