SharePoint Adventures : ADFS Setup – Part 1
I've had a few cases that involved customers using ADFS, SharePoint and Reporting Services. When going through this, one of the big struggles was just getting ADFS up and running with SharePoint 2010 so we could focus on the customer's issue. I did find a few items out there that got me pointed in the right direction, but they were all missing a few pieces that connected the dots. I thought I would share out my experience and try to be as complete as possible. I'll also say, that I do not consider myself an expert in ADFS, but I did have to run though this multiple times.
One thing this blog post will not go into is normal Active Directory (AD) setup or setting up a Certificate Server. I will be using the Certificate Server that comes with Windows Service for use with this setup. This is not a requirement, but made it easy for me to get this working in a complete manner as opposed to using self generated certificates, or getting trial certs for a demo purpose.
Certificates
During this course of this setup, there will be multiple points where we will need a certificate for one reason or another. Either ADFS or SharePoint/IIS. Because I have a Certificate Server setup, it is pretty easy to get a new cert. Which is also why I'm using it. You can also create a Self generated cert.
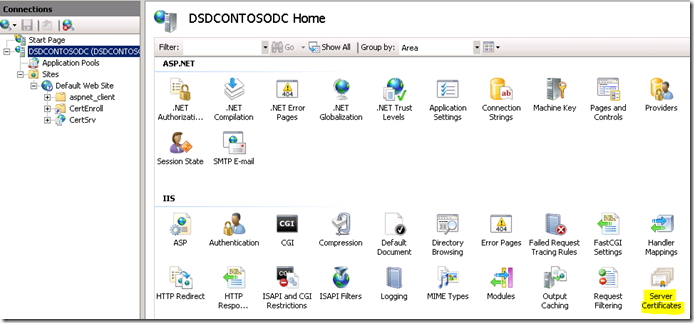
Within IIS Manager, highlight the server itself. There you will see an item labeled "Server Certificates". Make sure you are not on the Site, but the actual Server.
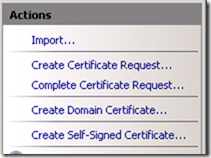
From there you have a few options. You can "Create Domain Certificate…" which will base it off of the Certificate Server bound to your Domain. You can also "Create Certificate Request…", which will go through the normal request for a Certificate Authority (CA) not bound to Active Directory. This could be a 3rd party CA like Verisign, or a CA that you have in your environment that isn't bound to your AD environment.
The last option is "Create Self-Signed Certificate…". This allows IIS to create a temporary certificate for use. While this can be used for your situation, it complicates things a little when it comes to moving the certificate around. When we get to the SharePoint integration, there will be times where we need to export and import some certificates. This is much easier to do when we have a known CA.
ADFS 2.0 Setup
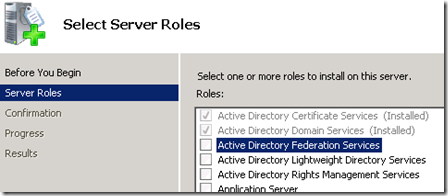
When I first started on this, I recall seeing ADFS within the Roles for Windows Server, and thought: "Sweet, this will just be a quick wizard and I will be on my way!" Yeah, I was wrong.
What is listed in the Role selection is considered ADFS 1.0. What we really want is ADFS 2.0. This can be downloaded from the Microsoft Download center here. And here is a quick link to the Documentation on ADFS 2.0. This will grab AdfsSetup.exe. Before I ran this, I made sure that I had Certificate Server setup as it will be needed.
From the install perspective, I choose "Federation server". From a quick test environment, this works fine, but if you are deploying this into a production environment you may need to have a different configuration depending on what you are doing.
Of note, I installed this on my Domain Controller, as I had a limited number of machines. This requires that PowerShell, IIS and some .NET items be installed for this to work as the ADFS items are basically a .NET Web Service. It will also install Windows Identify Foundation (WIF). I've talked about the Claims to Windows Token Service (C2WTS) before, and that is also part of WIF.
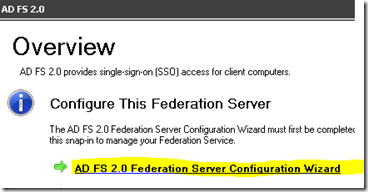
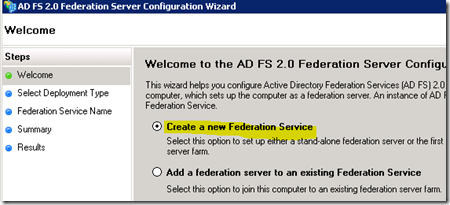
That's pretty much it from the install wizard that I encountered. After setup is done, I went into the ADFS Snap-in. From there it has a link to start the "ADFS 2.0 Federation Server Configuration Wizard".
ADFS 2.0 Federation Server Configuration Wizard
I then choose "Create a new Federation Service". Hit Next.
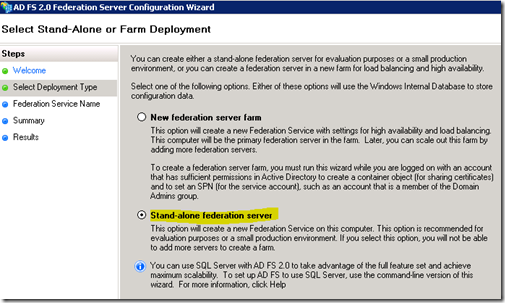
Because this is a test server, I choose "Stand-Alone federation server". Of note, this will also make use of SQL Server Express Edition for the ADFS data store. Which goes on the DC. Definitely not recommended on a Domain Controller if you are deploying this to production. It does mention that you can set this up with a full blown SQL Server from a command line, but I think SQL Express will still be laid down initially and you can just switch it over to full blown SQL Server. I'm not sure if there is a workaround to prevent SQL Express from being laid down. It may be that once you switch it over to the full blown SQL Server install, that you can just uninstall SQL Express.
It may also be that the "New federation server farm" option gives you some options for this, but I didn't have a look at that.
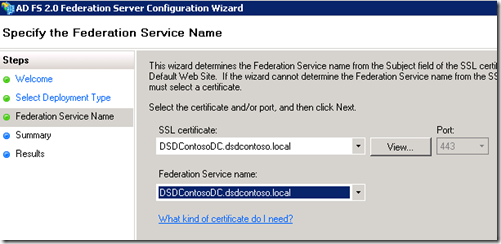
The next piece is where the Certificate Server first comes into play.
The certificates listed here are what are in the local Certificate Store. As this is the cert that will be bound to the Web site, the name will be derived from the Certificate itself. Meaning that the URL for the site should match the Certificate name. If the name listed isn't one you want, you can go to IIS and create a new Cert. Refer back to the Certificates section at the beginning of this blog which talks about how to create a new certificate.
That's pretty much it for that Wizard.
Claims/SAML
One thing to keep in mind is that ADFS will generate a SAML token which is what we use for Claims. When you setup a trust relationship (which we will get into in the next post), you are really setting up what claims you want in your token. As a result, when you setup a Trust Provider, which is what ADFS will be, within SharePoint 2010, it will be Claims based authentication.
Adam W. Saxton | Microsoft SQL Server Escalation Services
https://twitter.com/awsaxton