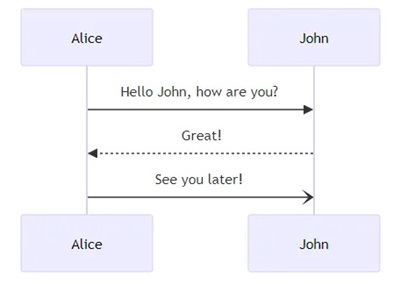


Azure DevOps Pipelines: Discovering the Ideal Service Connection Strategy

Hands-On Azure Container Apps 101 — Deploying a scalable Go-Backend
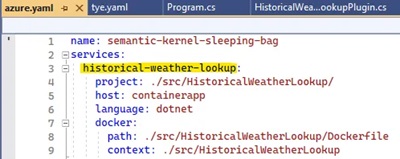
How to enhance your chatbot so it can retrieve data from multiple data sources & orchestrate its own plan with C# Semantic Kernel, planner & Azure OpenAI – part 4 (local development & deployment details)
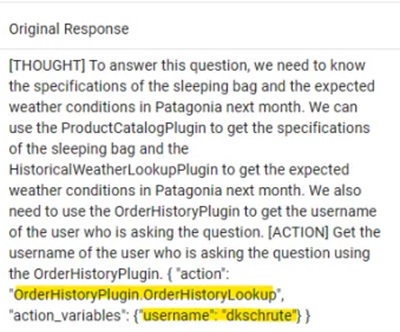
How to enhance your chatbot so it can retrieve data from multiple data sources & orchestrate its own plan with C# Semantic Kernel, planner & Azure OpenAI – part 3 (demo app)

How to enhance your chatbot so it can retrieve data from multiple data sources & orchestrate its own plan with C# Semantic Kernel, planner & Azure OpenAI – part 2 (demo app implementation)
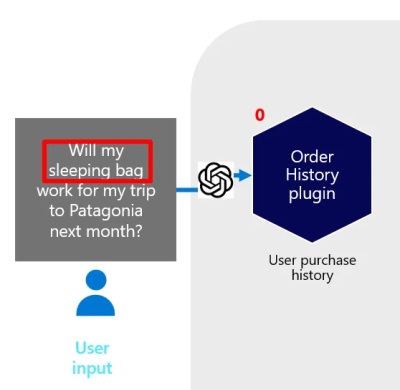
How to enhance your chatbot so it can retrieve data from multiple data sources & orchestrate its own plan with C# Semantic Kernel, planner & Azure OpenAI – part 1
Configuration of Data Movement between On-prem or private network to Azure Cloud

Effective Kubernetes for JakartaEE and Microprofile Developers


 Light
Light Dark
Dark