SharePoint 2010: Custom Claims Provider for users authenticated from different sources
One of the special features SharePoint 2010 introduced is an option to implement multiple authentication sources on the same web application. This is applicable if you are using Claim based authentication.That means you can use any/all of the following authentication options on a single web application:
- Windows based authentication claims (using NTLM/Kerberos)
- Form based authentication claims(using ASP.net membership and role provider with LDAP, SQL or any custom user sources)
- SAML claims (using ADFS, Live ID or your own custom STS provider)
Again, you can write Custom Claim Providers to implement additional claim tokens on top of the existing claim tokens SharePoint receives from the authentication provider.
In this example we are going to implement a custom claim provider which will be applicable for users coming from 2 different sources:
- Windows based authentication claims (using
NTLM) - Form based authentication (using custom
Asp.Net membership and role provider with SQL Server)
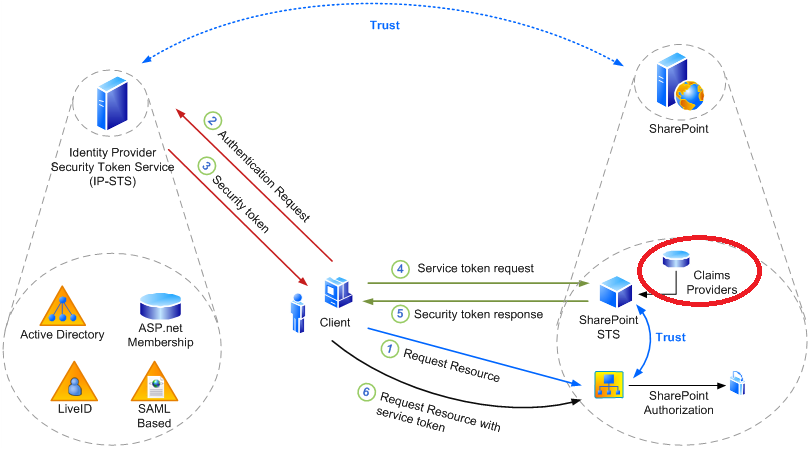
In the following image, we are dealing with the area marked in red circle.
Requirement:
Contoso Inc. has implemented 2 different types of authentications (mentioned above) for their web application. They have different site collections dedicated to users who are experts on different technologies (Exchange, SharePoint, OCS).
This information of what user has what expertise is available in their SQL Server DB. They would like to use the data to make sure users have permission to specific site collections depending on their expertise.
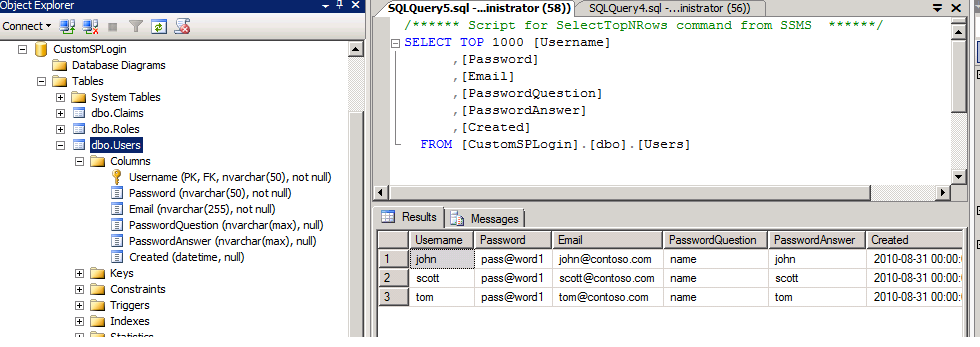
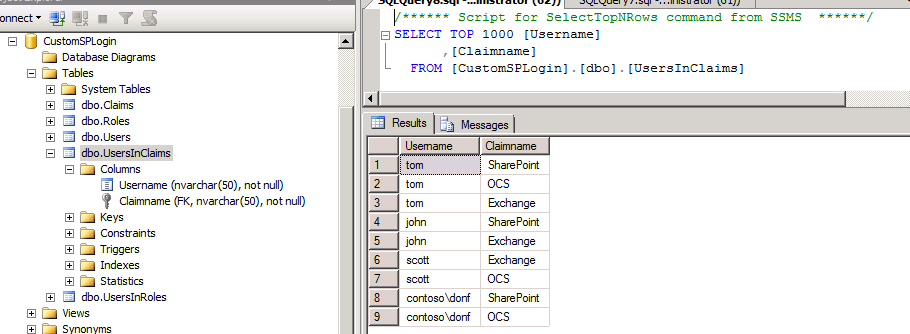
Let’s have a look into the DB:
Following 3 tables are for their custom ASP.Net Membership and Role Provider:
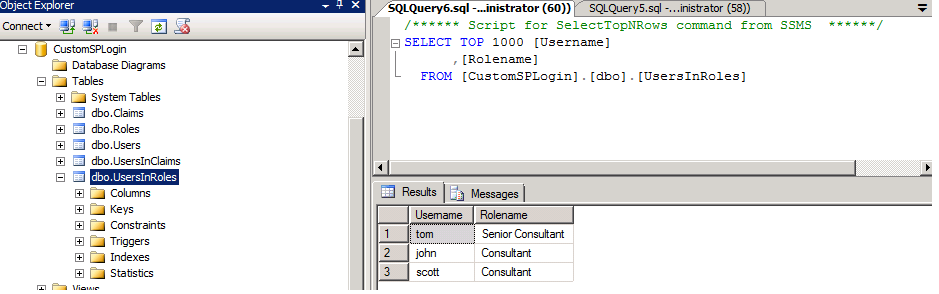
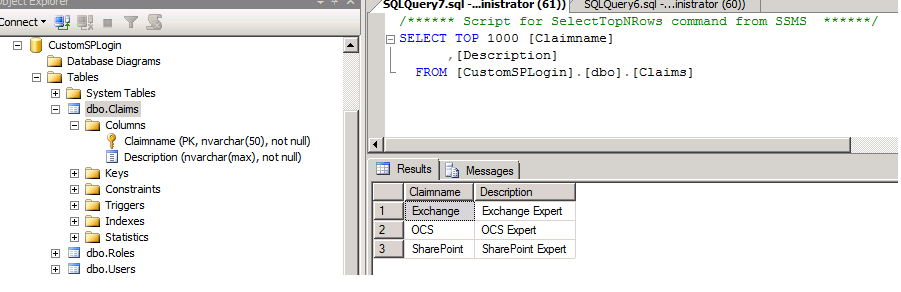
Following 2 tables defines their user expertise:
If you look closely into the last table (UsersInClaims), you will see 2 different types of users there. Few are users from their FBA source and few are from AD.
Now is time to create our custom claim provider. Thanks to Steve Peschka. He made our life easier. After going through the following articles, it seems a piece of cake:
https://msdn.microsoft.com/en-us/library/ff699494.aspx
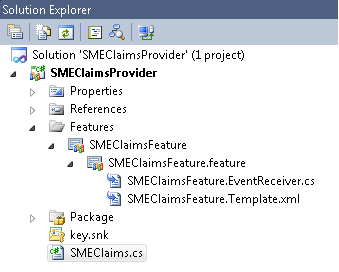
I started with an Empty SharePoint project and added a class that defines the claim provider, a farm scoped feature and also a feature receiver. The feature receiver basically helps to attach this claim provider to the farm.
The Code (SMEClaimsProvider) is given along with this document. One specific area I want to discuss here. In the method “FillClaimsForEntity” within “SMEClaims” class you can see an area where we separated the additional string tag injected by SharePoint for Windows authenticated users:
string userName = string.Empty;
if(entity.Value.Contains("0#.w"))
{
string[] strArr = entity.Value.Split('|');
userName = strArr[1];
}
Once we deploy this solution to the Farm and activate the Farm level feature, we can go to each individual site collection and can use people picker control to add users with different claims (Exchange, SharePoint or OCS).