DAL in action: Managing Network switches using PowerShell and CIM
This post is a part of the nine-part “What’s New in Windows Server & System Center 2012 R2” series that is featured on Brad Anderson’s In the Cloud blog. Today’s blog post covers management of network switches using CIM and WS-Man standards and how it applies to the larger topic of “Transform the Datacenter.” To read that post and see the other technologies discussed, read today’s post: “What’s New in 2012 R2: IaaS Innovations.”
We described the role Cloud OS plays is managing the datacenter and the role the Datacenter Abstraction Layer (DAL) vision plays in enabling this on the DAL website link. Of all the managed datacenter elements, nothing is getting more focus than “Network”. This is very expected. As we say “Difference between Networking and Not-Working” can be huge. It leads to loss of revenue, reduced uptime and frustrated customers. To address this humongous challenge, the industry has come up various open and proprietary solutions. We found that almost all of these solutions require the network switch vendors to write a custom piece of software to “plug-in” to their management framework.
We disagree with this approach. We think device vendors should invest their energy in making their product better – not in creating a plethora of plug-ins that require constant change. In the world view advocated by DAL, network switch vendors implement an industry standard protocol and schema, and it is up to various Software Defined Networking (SDN) solutions to update their own software to talk to standard enabled switches.
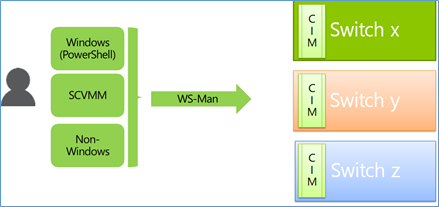
Imagine a world where OSes (like Windows Server) or Fabric Controllers like System Center Virtual Machine Manager (SCVMM) are able to manage network devices right-out-of box using CIM /WSMAN standards – without requiring third party plugins or agents.
Imagine configuring switches from different switch vendors in a simple consistent way.
Imagine if there was a way to “discover” vendor value adds and use them without having to learn proprietary CLI commands.
This is what standards based management brings to the complex world of software defined networking.
When we started working on this compelling vision, we identified one challenge. Network vendors we talked to responded in one voice “We are not experts in writing CIM/WS-Man engine – it’s easier for me to write plugins than implement a full CIM server and WS-MAN protocol on my device”. Well, we solved that problem a year ago by releasing Open Management Infrastructure (OMI) to Open Source community under Apache 2.0 license. The ball started to roll.
To give a very high level view, currently CIM schema for network switch management covers the following functionality.
– Switch global settings
– Ethernet port and Vlan configuration (L2)
– Switch Virtual Interface (SVI), IP address (L3)
– Routing and BGP
– Users, Roles and ACLs
– AAA configuration
– SNMP settings
To ensure interoperability and consistency between schema implementation by different vendors, we created a Logo certification for CIM-enabled Switches. Currently logo tests require only the L2 level functionality, the bare minimum required for SCVMM 2012 R2 integration.
We are also glad to let you know that Arista announced CIM/WS-Man support in their entire product range with release of Windows Server 2012 R2 Preview. With this brief overview – we switch to demo mode, showing this vision in action using an OMI enabled Arista switch.
Switch Configuration using PowerShell
Windows PowerShell (PS) 3.0 shipped with CIM Cmdlets – that allow Windows to manage any standard CIM/WSMAN server. We will use these cmdlets to configure an Arista switch. You can read about CIM Cmdlets in this blog post. Detailed help documentation is here.
| ## Connect to Management Port on the switch. Use SSL to connect
$ip = “10.10.1.1” $Cred = Get-Credential admin #username and password to connect to the switch. $so = New-CimSessionOption -UseSsl -SkipCACheck -SkipCNCheck –SkipRevocationCheck $s = New-CimSession -CN $ip -Auth Basic -Credential $Cred -SessionOption $so Get-CimInstance CIM_ComputerSystem -CimSession $s # Get list of ports Get-CimInstance CIM_EthernetPort -CimSession $s | Select ElementName, Speed,MaxSpeed |
One very common questions that comes up from device vendors is – Would implementing standards mean every switch will become same? What about value adds that differentiate vendor offerings?
Answer is: Implementing CIM standard does not result in loss of value-adds. In fact, customers will find it easier to discover and use these custom settings. Device vendors can derive their class from standard CIM class and add properties or methods to expose the value-added functionality.
| ### Vendor Value Adds – PowerShell also enables you to inspect class schema –
### (OMI implements GetClass standard operation) # You can discover any vendor extensions – custom properties and methods to CIM derived classes $ports=Get-CimInstance CIM_EthernetPort -CimSession $s $ports[0].PSTypeNames $ports[0].CimClass $ports[0].CimClass.CimClassMethods $ports[0].CimClass.CimClassProperties | Select Name, Cimtype |
With this introduction – let’s take some common switch configuration tasks and see how to do it using CIM. The script below shows how to do the following:
a. Enable port
b. Disable port
c. Change port mode to trunk and set Vlans
d. Change port mode to access and set native Vlan
e. Enumerate Vlans
f. Create Vlan
g. Delete vlan
| ## Connect to Management Port on the switch. Use SSL to connect
$ip = “10.10.1.1” $Cred = Get-Credential admin $so = New-CimSessionOption -UseSsl -SkipCACheck -SkipCNCheck –SkipRevocationCheck $s = New-CimSession -CN $ip -Auth Basic -Credential $Cred -SessionOption $so ##Enumerate ports by getting all instances of CIM_EthernetPort $ports = Get-CimInstance CIM_EthernetPort -CimSession $s ## Enable Port – Invoke RequestStateChange method , passing RequestedState parameter as 2 (Enable) Invoke-CimMethod $ports[0] @{ RequestedState = 2 } RequestStateChange ## Disable Port – Invoke RequestStateChange method , passing RequestedState parameter = 3 (Disable) Invoke-CimMethod $ports[0] @{ RequestedState = 3} RequestStateChange ## Change port mode to Trunk #get the settings for this port by going to associated instance of CIM_ EthernetPortAllocationSettingData $psd = Get-CimAssociatedInstance $ports[0] -ResultClassName Cim_EthernetPortAllocationSettingData #Set the port mode to access by setting DesiredVLANEndpointMode to Trunk (5) Set-CimInstance $psd -Property @{DesiredVLANEndpointMode = 5 } #Now Set Allowed Vlans to 1,2 and 3 #Get to the Vlan settings for the ports through the association from Port>LanEndpoint?VlanEndpoint>SettingData $lanEndpoint = Get-CimAssociatedInstance $ports[0] -ResultClassName Cim_LanEndPoint $vlanEndpoint = Get-CimAssociatedInstance $lanEndpoint -ResultClassName Cim_VLanEndPoint $setting = Get-CimAssociatedInstance $vlanEndpoint -ResultClassName Cim_VLanEndPointSettingData Set-CimInstance $setting –Property @{ TrunkedVLANList = @(1,2,3)}
## Change Port Mode to access #Get settings for the port $psd = Get-CimAssociatedInstance $ports[0] -ResultClassName Cim_EthernetPortAllocationSettingData #Call ModifyInstance , setting DesiredVLANEndpointMode to Access (2) Set-CimInstance $psd -Property @{DesiredVLANEndpointMode = 2 }
## Enumerate Vlans $vlans = Get-CimInstance CIM_NetworkVlan -CimSession $s ## Create Vlan – in the script below, we create two new vlans with id 4 and 5 $svc = Get-CimInstance MSFT_SwitchService -CimSession $s $cs = Get-CimInstance CIM_ComputerSystem -CimSession $s #Create instances on MSFT_NetworkVlan class, these are in-memory objects on client side $v4 = New-CimInstance -ClientOnly MSFT_NetworkVLAN @{VLANId = [uint16]4} -Key @(“InstanceID”) $v5 = New-CimInstance -ClientOnly MSFT_NetworkVLAN @{VLANId = [uint16]5} -Key @(“InstanceID”) #Invokde AddVlan method on MSFT_SwitchService class, pass two vlan instances created above Invoke-CimMethod $svc[0] @{TargetedSwitch = $cs[0]; NetworkVLAN = [ciminstance[]]@($v4, $v5)} AddVLAN
## Remove Vlan $svc = Get-CimInstance MSFT_SwitchService -CimSession $s $vlan = Get-CimInstance MSFT_NetworkVlan -CimSession $s | ? {$_.VLANId –ieq 2} #Invoke RemoveVlan method of MSFT_SwitchService class and pass the Vlan instance to be deleted Invoke-CimMethod $svc[0] @{VLAN = [ciminstance[]]@($vlan)} RemoveVLAN |
The script sample above shows how to do common switch configuration tasks using PowerShell. To ensure switches from different vendors can be managed in a consistent way, we also created a logo for CIM enabled Network Switches. All Windows Server logo certified switches will have consistent implementation of CIM schema ensuring that it will just work with SCVMM and Windows Server. There is an important point to clarify here. DAL vision is to enable management of datacenter elements from both Windows and non-Windows. The Switch management tasks shown above in PS script can also be performed from a non-Windows client having CIM/WS-Man client.
Our goal is to enable 100% of switch configuration using CIM and WS-Man. We are pleased with the uptick in the device vendors willing to implement CIM schema in devices. We hope that standard based management of network switches will take Software Defined Networking to levels never seen before.
Thanks
Osama Sajid, on behalf of
Standards Based Management team.
To see all of the posts in this series, check out the What’s New in Windows Server & System Center 2012 R2 archive.

 Light
Light Dark
Dark
0 comments