Video Screencast: Complete setup details for federated identity access from on-premise AD to Office 365.
How to set up IIS, ADFS 2.0, the Federation Config Tool and Office 365 Dirsync. The video starts with federated access and its setup. Shows how an existing user can use their AD credentials to log in to Office 365 entirely seamlessly; they hit CTRL-ALT-DEL and login to the machine, then when they go to Office 365 they are not prompted for the password because they have already logged in.
Then in Dirsync I do the setup so that you can create users and modify their attributes in AD and they automagically appear in Office 365 as federated accounts that you can use your AD credentials to log in to.
I’ll do a whiteboard flow of the protocols and how they work very soon, I just wanted to get the demo-video in place because so many folks have asked for it. I use the “magic of video editing” to avoid the confusion of error messages and to shorten the install-times of various components.
Complete setup details for federated identity access from on-premise AD to Office 365. from Steve Plank on Vimeo.
Video Screencast: AD to Office 365 setup
If you are going to do this yourself – here are a couple of notes worth mentioning:
Federated Identity:
The “Admin” account you need to use for the powershell commands that set up the ADFS server and the Microsoft Federation Gateway up in the cloud is not just any admin account. It needs to be the first admin account on the Office 365 system when the subscription is created.
There is a typo in the help files on the Microsoft Online portal (https://onlinehelp.microsoft.com/en-us/office365-enterprises/ff652560.aspx). The 3rd powershell command says:
“Convert-MSOLDomainToconverFederated –DomainName <domain>”.
The part I’ve highlighted in red should be missed out completely – so the command becomes:
“Convert-MSOLDomainToFederated –DomainName <domain>”.
DirSync:
Can only run on a 32-bit Server. I used Windows Server 2008 SP2. You can’t install it on a Domain Controller. Which means if you are going to set up a test-lab, you need a minimum of 2 machines: a DC (you could use for ADFS 2.0) and a member server for the Dirsync tool.
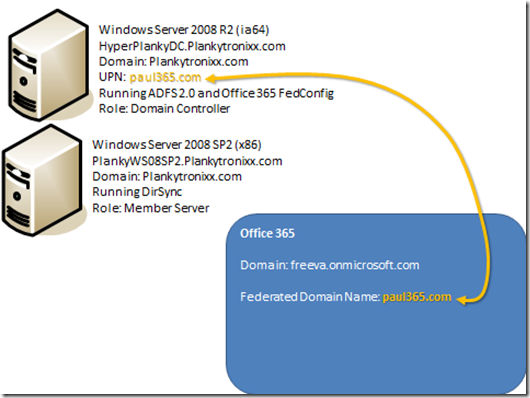
In my test environment I had:
Planky – GBR-257