Authentication Precedence and Behavior in IIS
Introduction
This blog seeks to explain which authentication mode will take precedence when multiple authentication mechanisms like Anonymous, Basic, Windows are enabled. Please note that the following instructions are applicable only to ASP.Net applications and Internet Explorer.
Authentication Precedence
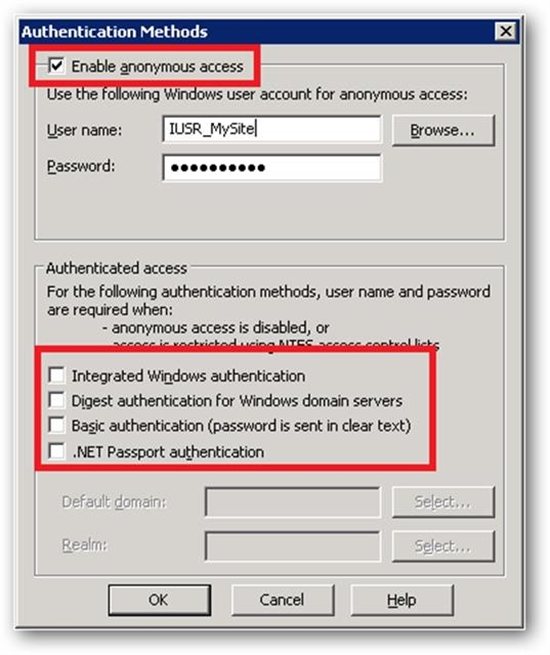
The best way to find out which authentication mode will take precedence is to revisit the IIS 6 Directory security Tab. The order in which authentication modes are presented from top to bottom indicates the authentication precedence. For example, Anonymous Authentication will take precedence over Windows, Digest and Basic authentication. However, if the client Certificate Authentication is configured, then it will take precedence above all other authentication mechanisms since the SSL handshake takes place even before the HTTP request comes into picture.
To Summarize everything, this is how the authentication precedence looks like.
- Client Certificate Authentication
- Anonymous authentication
- Windows authentication
- Basic authentication
Authentication Behavior
Scenario 1 - Only Anonymous authentication enabled
Under any given circumstances, when a client makes the first request to the server, it will be anonymous. On the server side, if the application is also configured to run under anonymous authentication, then the server will process the request and send the desired response back to the client without requesting any further validation from the client.
Scenario 2 - Multiple authentication modes enabled
Let us assume that both Basic and Windows authentication have been enabled on the server at the application level. When the first anonymous request from the client reaches the server, the server checks the application's configuration and understands that it is configured to run under Basic/Windows authentication. Since these authentication mechanisms need further validation to deliver the required page, the server sends the authentication details to the client and requests for further validation. The client picks up the most secure authentication mechanism(windows) from the list provided by the server and takes necessary steps to provide the required information to the server.
It is incorrect to assume that if two authentication modes are configured and if one fails, the request will fall back to other authentication mode. If you consider my previous example, I stated that if Windows Authentication and Basic Authentication are enabled, Windows authentication will take precedence. Now, if Windows authentication fails, it will never fall back to Basic and take it forward from there.
A fall back would mostly occur only in following scenarios.
- Scenario 1: Under Windows Authentication, if Kerberos fails, it will fall back to NTLM
- Scenario 2: If client Certificate Authentication and Anonymous authentication are enabled on the server at the application and if client Certificate Authentication fails, then the request will fall back to Anonymous authentication. If you're setting up client certificate authentication in your environment, please make sure you have anonymous authentication disabled so that you don't end up receiving false positive answers.
Hope this helps :)