Using Azure AD B2B collaboration support for Google IDs and Conditional Access
Hi,
Alex Simons announced the public preview of Azure AD B2B Collaboration support for Google IDs, so i thought I'd share my findings on configuration, user experience and bring Azure AD Conditional Access into the mix.
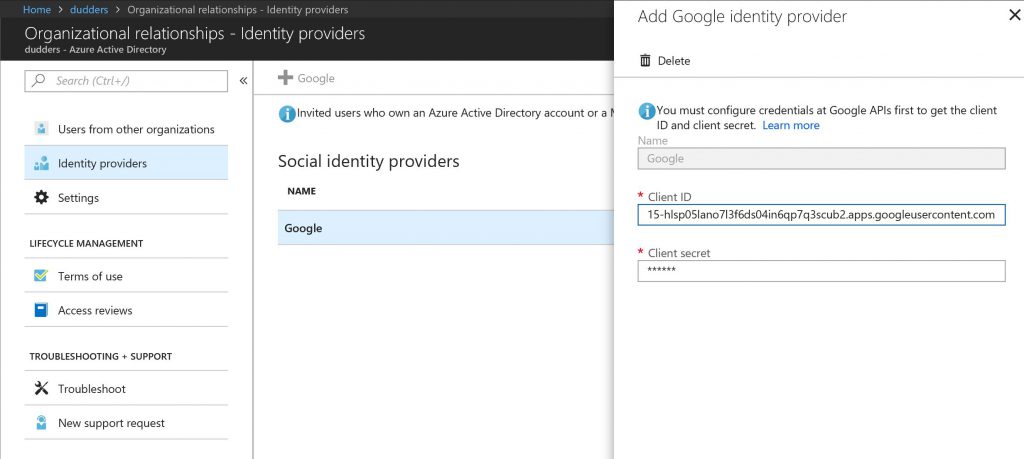
The first step to setting this up is to add Google as an identity provider in your Azure AD tenant. This has been beautifully documented by the Azure AD team here.
Once you have followed those steps then you are ready to roll...
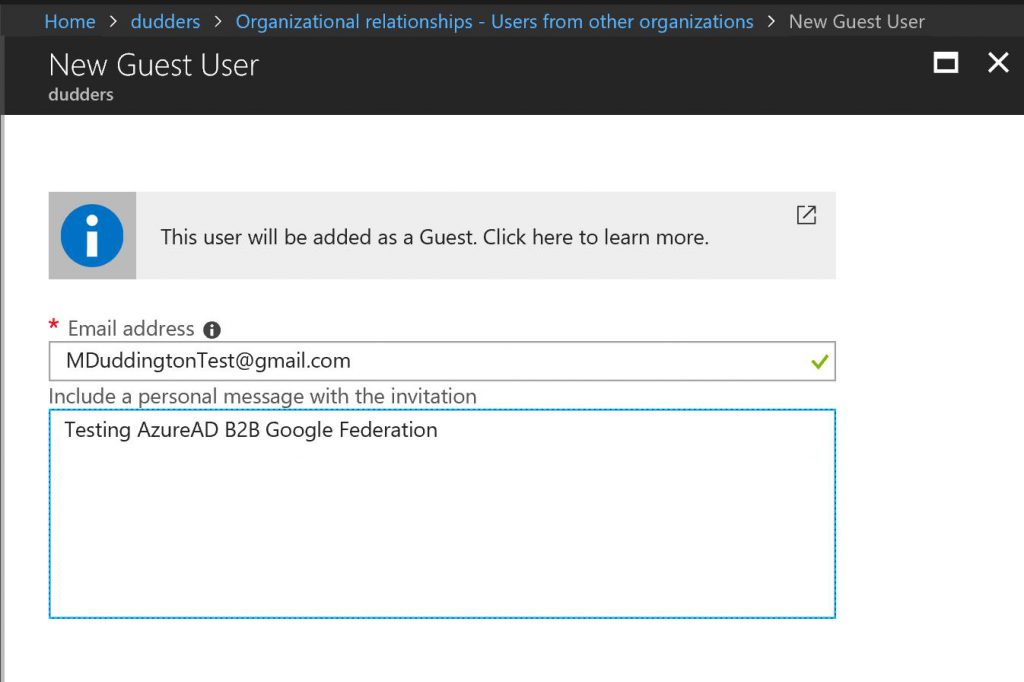
Now it's time to add a guest user. There are numerous ways to invite guest users but for the purposes of this post I'm inviting from the Azure AD Portal.
NOTE: At the time of writing this document it's only @gmail.com users that are supported.
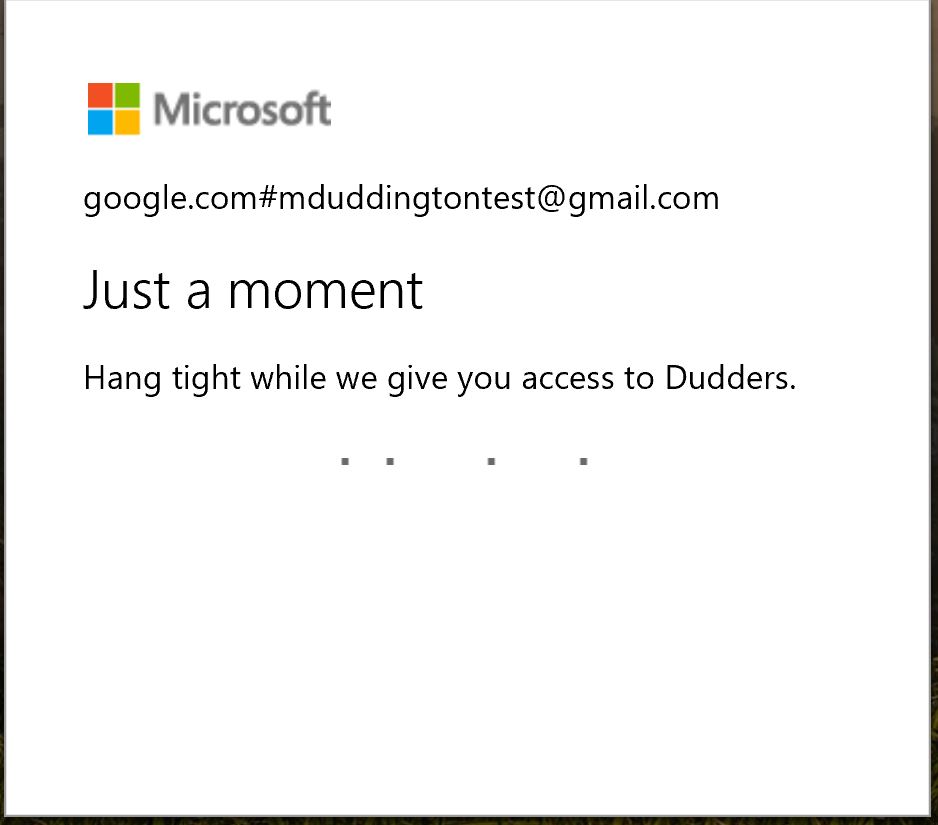
Once invited the user then the user receives an invitation.
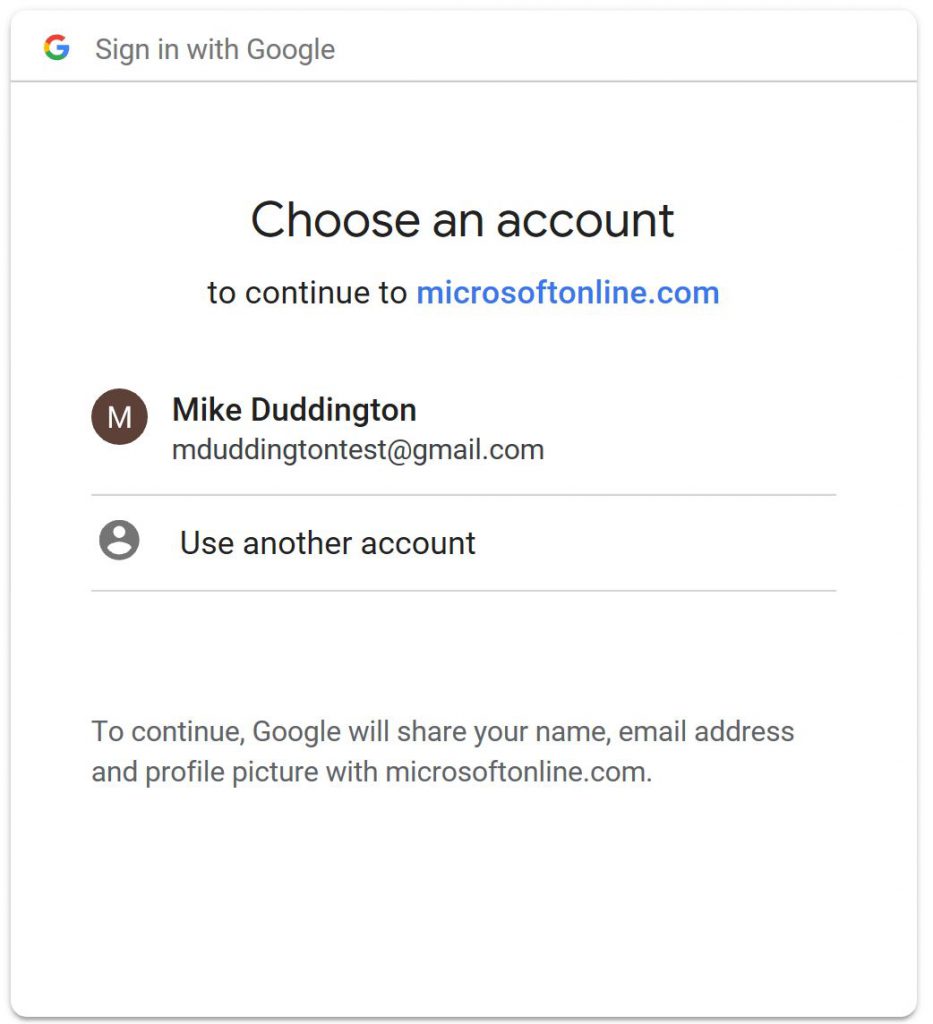
The user then clicks "Get Started" and then they are prompted to authenticate with their GoogleID.
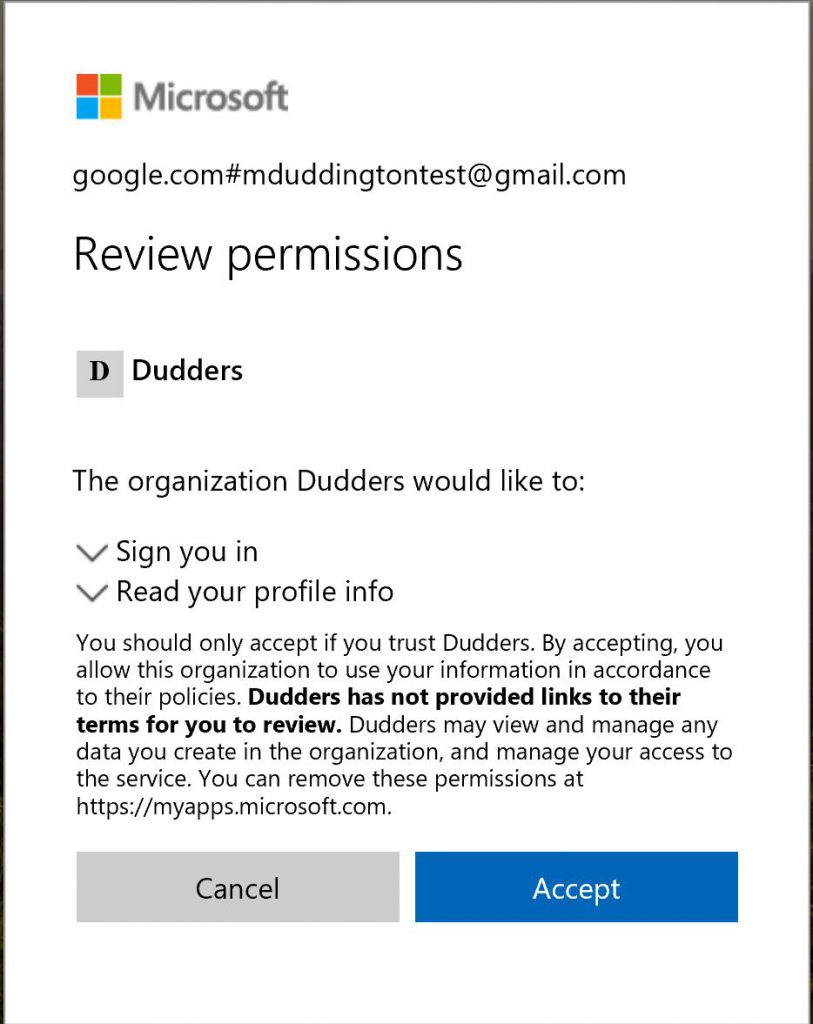
Once successfully authenticated the user then has to review the permissions and "Accept".
Access is then provisioned.
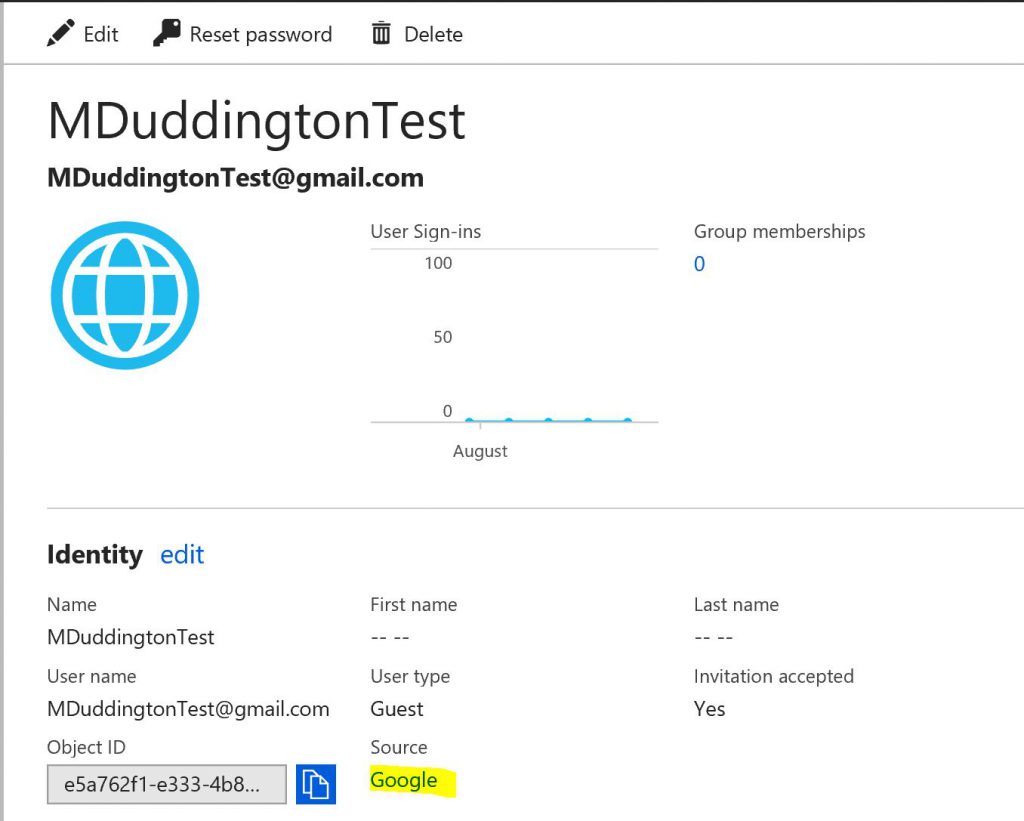
The user is now logged on using their Google ID! Now lets have a look at what that account looks like in Azure AD.
The user is now provisioned in Azure AD as a "Guest" user and the "Source" is Google.
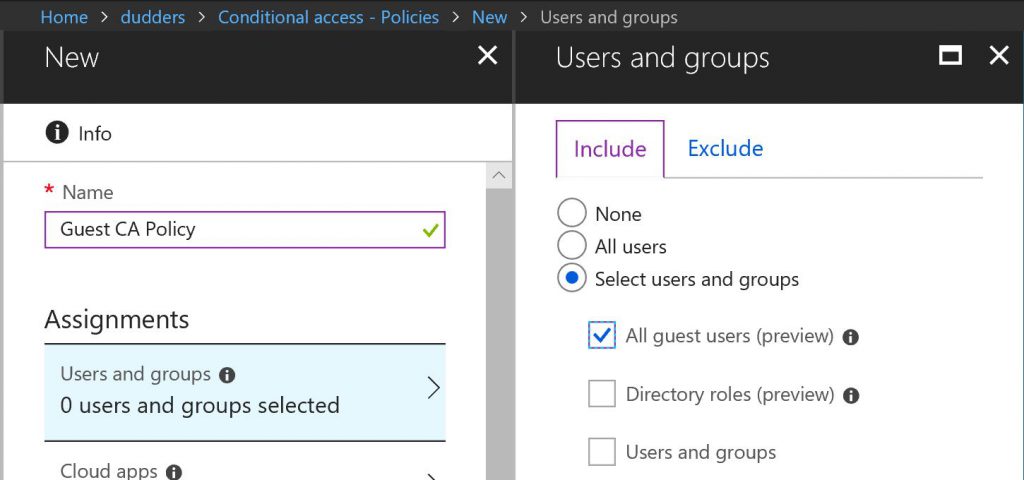
You may be aware of a recent public preview which enables you to target Conditional Access policies at "guest users". This is a great feature and allows you to target all guest users (including GoogleID's) to provide additional protection when they are accessing your organisations resources. Let's set up a Conditional Access Policy which will enforce Azure Multi-Factor Authentication for all guest users.
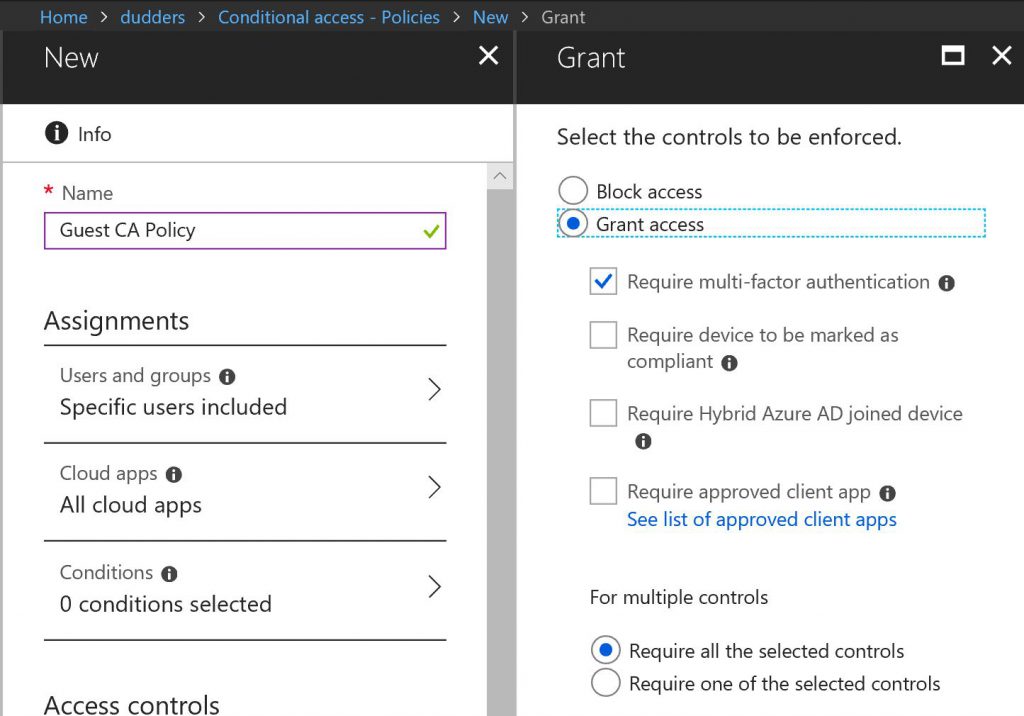
Create a new Conditional Access Policy and select "All guest users (preview)", make the relevant "Cloud app" assignments and any additional conditions you would like to test.
NOTE: This will apply to all users with the userType attribute set to guest
Now select "Require multi-factor authentication" as a control to enforce when granting access. As always with Conditional Access make sure you understand the impact of the policy and always test before enabling in production.
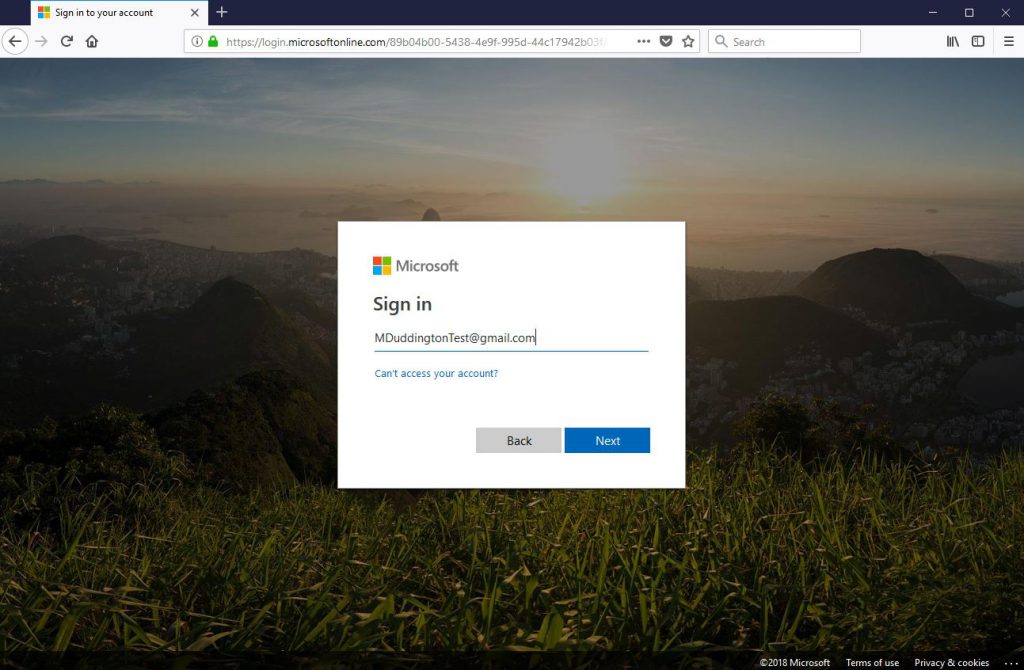
Let's have a look at the user experience. Access the resource (At this stage the URL must include the tenant context e.g. https://myapps.microsoft.com/?tenantid=\<tenant id>) and the user is prompted for authentication.
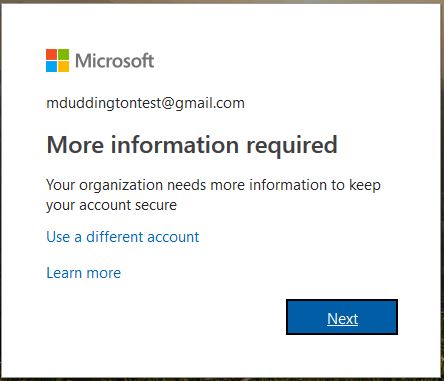
Once the user has entered their GoogleID credentials they are prompted with the following.
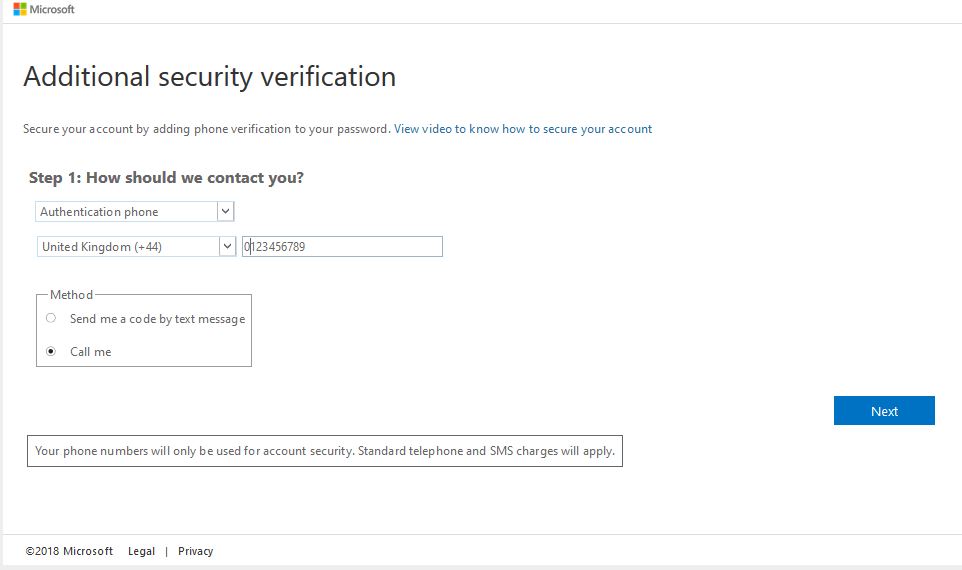
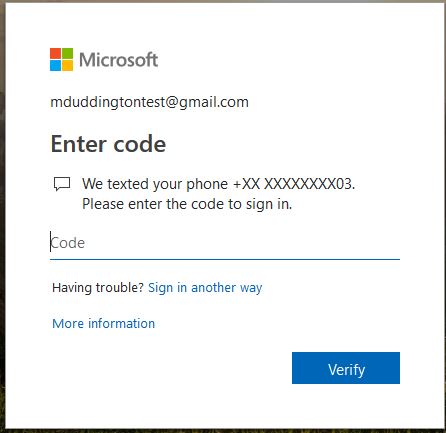
The user is now forced to register their MFA details, undergo verification and then they get access to the resource.
Subsequent authentications the user is prompted for MFA.
In summary, invited users can now use their GoogleID to access Azure AD integrated resources. Your organisation also has the ability to enforce a stronger level of authentication with Conditional Access to ensure a higher level of protection for your companies resources.
Thanks for reading!!
MD