Cloud Identity Overview - Part 1 (Authentication)
Hi,
I spend a lot of time with customers talking about Cloud Identity so I thought I'd put together a series of posts that provide an overview of the Microsoft Cloud Identity Story. In these posts I will aim to provide an overview of the technologies, describe the deployment options and answer frequently asked questions I get from customers.
When it comes to Microsoft Cloud Identity we can broadly break the topics into 3 areas, which I will cover in 3 posts.
- Authentication - types of authentication available for Microsoft Cloud Services.
- Authorisation - options to control what users can access, from where and from what device.
- Synchronisation - synchronisation of your corporate identities to Azure Active Directory.
Part 1 - Authentication
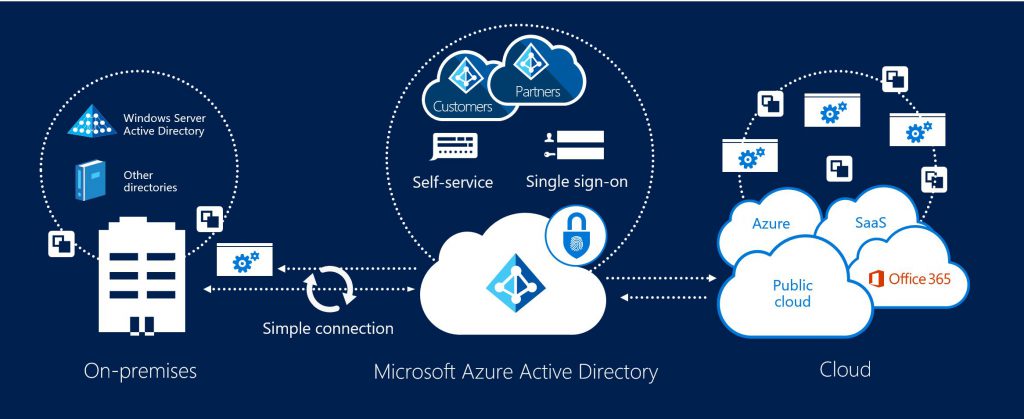
Azure Active Directory (AAD) is the authentication platform that underpins Microsoft Cloud Services. It underpins Azure, Office 365, Dynamics 365, thousands of Azure Marketplace apps and any SAML compliant application. There are 4 primary options for authentication with Microsoft Cloud all of which leverage AAD.
- Cloud ID - This is typically used by small businesses. You can think of this as equal to an hotmail.com account. It is an Identity which is created in AAD and there is no on-premises integration. The user has a separate Identity for Microsoft Cloud Services. They can have the same password but that relies on the user setting it so, in addition password expiration policies, etc may differ resulting in users potentially having different passwords at different times.
- Password Hash Synchronisation - This option is used by all types of organisation and is so popular due to the quick deployment and excellent on-premises integration. This option uses a synchronisation appliance called "AADConnect" to synchronise users, groups and contacts from the on-premises Active Directory to AAD. It also synchronises a "hash of a hash" of the users passwords so users are able to use the same credential to log on to Microsoft Cloud Services as they do their desktops. When a user changes their password on the on-premises Active Directory this change is synchronised to AAD within a couple of minutes so the user has that consistent experience.
- Pass Through Authentication - This is a new option (Currently in Preview at the time of writing this post) which is becoming very popular with enterprise customers. Like the Password Hash Synchronisation option AADConnect synchronises users, groups and contacts to AAD but no password hash is synchronised. Instead a connector is deployed (by default on the AADConnect appliance) which creates an encrypted tunnel between the on-premises AAD Connect Server and AAD. When a user authenticates the request is proxied from AAD into the customers network (via this outbound initiated tunnel) and the customers Active Directory authenticates the request and passes back the appropriate token. This is a good option for customers that want the excellent on-premises integration but aren't keen on synchronising a "hash of a hash" of a password. There are also HA options available to deploy multiple connectors to ensure that on-premises authentication for Microsoft Cloud Services using this method is continually available.
- Federated Logon - This involves using a federated authentication platform to authenticate against Azure AD. Active Directory Federation Services (AD FS) is the Microsoft offering in this space but many third party products are supported. This scenario also works in conjunction with AADConnect to synchronise users, groups and contacts to AAD but the entire authentication process is offloaded to the customers Federated Identity platform. AAD quite simply re-directs the user to AD FS and expects the appropriate token returned to allow\deny access. This option is very popular with large enterprises and prior to the release of Pass Through Authentication was the most popular option I was seeing with my customers. The reason for that being that it gives you complete control of the authentication process. All authentication is performed against the customers Active Directory so if you disable an account, set password strength or set logon hours then it implicitly applies to authentication against Microsoft Cloud Services. Also its provides the best SSO experience for domain joined machines on a customer's network.
So what's the best authentication option for my organisation?
Well that is the question! In reality it's something you really need to think about and ensure your chosen option meets your organisational requirements, but should you decide to start with one option and change later then don’t worry it is possible…in my personal opinion Pass Through Authentication is the sweet spot in terms of amount of complexity vs functionality, security and user experience. But every customers requirements are different and you should review with care. One thing worth noting is whatever option you chose you have great capabilities in Azure AD that can secure your organisation, such as Conditional Access and Azure Identity Protection.
See you in Part 2 - Authorisation
MD