How to Determine Which DNS Server(s) Have Scavenging Enabled Using PowerShell
One of my duties as a Microsoft Premier Field Engineer (PFE) is to make sure the products a customer is currently using are configured properly and the customer is getting all the functionality the product provides. Whenever I’m working with customers on any DNS issue I always check to see if they are using DNS scavenging. DNS scavenging enables your DNS server to remove stale records periodically based on parameters you set.
Customers tend to fall into two groups when it comes to DNS scavenging. The first group has scavenging configured and it is working well. The second group turned on scavenging in the past, caused an outage, and have refused to try and use scavenging since then. When someone tells me they had a bad experience with scavenging in the past I know they probably just “threw the switch” without doing any of the prep work required to insure critical records do not get deleted.
There are plenty of DNS Scavenging articles out there (see below) so I won’t repeat it here. The high-level steps required to enable scavenging are as follows:
- Disable scavenging on ALL DNS servers.
- Enable scavenging on the DNS zones and monitor the time stamps on all records in the zones for a week or two to confirm DNS hosts are updating the time stamps on the A (host) records. Pay close attention to servers to make sure their records are being updated.
- Configured the zone scavenging interval.
- Backup your zone data just in case.
- Enable scavenging on a single DNS server and monitor for desired results
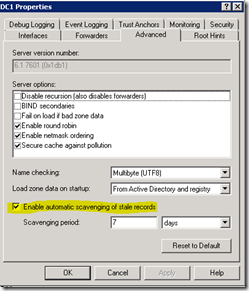
The remainder of this post will be about step 1 and how to find DNS server with scavenging enabled. If you only have a few domain controllers running DNS you can view the Properties for each DNS server as shown below.
If you have dozens or hundreds of domain controllers then you need an easier way. The PowerShell script shown below will dump the DNS server name and scavenging settings for each DNS server in your domain. If you see a scavenging interval greater than zero you know scavenging is enabled on the server.
#---------------BEGIN SCRIPT CODE------------------
####################################################
# DATE: June 13, 2013
# AUTHOR: Don Baker
# SCRIPT: GET-DNSScavengingData.ps1
# PURPOSE: Find DNS server(s) with scavenging enabled
#
#
# REVISON:
####################################################
cls
#get a list of domain controllers in domain (replace Contoso with your domain)
$DCs=(GET-ADDOMAIN -Identity Contoso).ReplicadirectoryServers
#loop through list of DCs and dump lines with "scavenging" in them
foreach ($dc in $DCs)
{
$output = dnscmd $DC /info
#Write-host $output |fl
$string =$output |Select-string "Scavenging"
Write-host $DC
Write-host $string
Write-host ""
}
#-----------------END SCRIPT CODE------------------
Sample Output
As you can see below server DC1 has scavenging enabled and set to 7 days (168 hours) and the other server has it disabled.
DC1.AD.CONTOSO.COM
ScavengingInterval = 168
DC2CORE.AD.CONTOSO.COM
ScavengingInterval = 0
Resources
Don't be afraid of DNS Scavenging. Just be patient
https://blogs.technet.com/b/networking/archive/2008/03/19/don-t-be-afraid-of-dns-scavenging-just-be-patient.aspx
Understanding Aging and Scavenging
https://technet.microsoft.com/en-us/library/cc771677(v=WS.10).aspx
Enable Aging and Scavenging for DNS
https://technet.microsoft.com/en-us/library/cc771362(v=WS.10).aspx