ZEN and The ART of ADFS Implementation–Part 5 of 5: ADFS Federation between Two forests
Since I don’t own a Public DNS name, My ADFS end point URL’s won’t be published externally and I will have to depend on Host header entries and I will enter the
First step we will ensure that we can ping the CHIADFS server from ZEN ADFS and Viceversa.
I will put a host header entry for Chiadfs.chi.local in ZENADFS
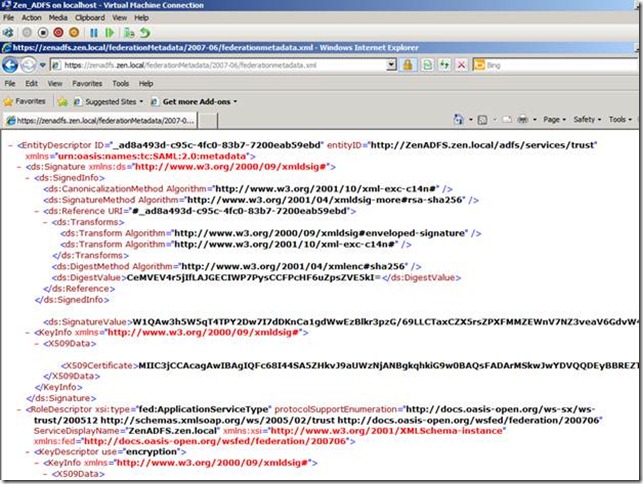
Browse https://zenadfs.zen.local/federationmetadata/2007-06/federationmetadata.xml.
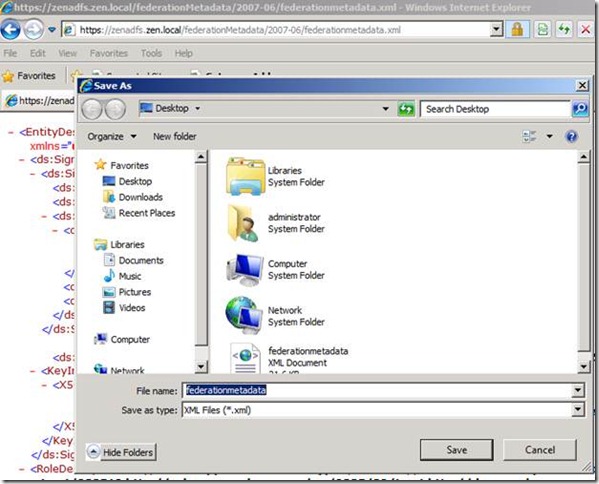
Save the Federationmetadata.xml file and save it on CHIADFS server and we will need it soon.
The same step has to be done from the CHI ADFS server by saving the Metdadat.xml file and saving it in the ZenADFS server.
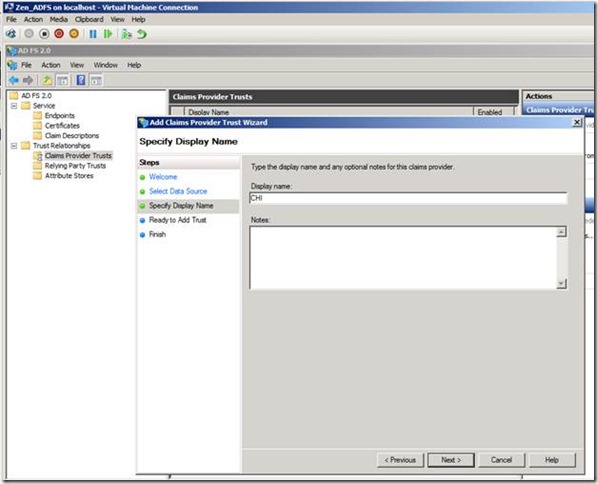
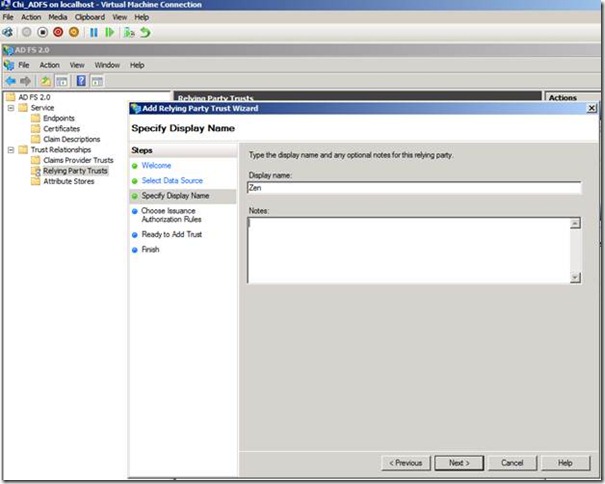
Next we will add the claims trust for the CHI ADFS in the ZEN ADFS server.
Run the wizard for adding a the claims provider Trust
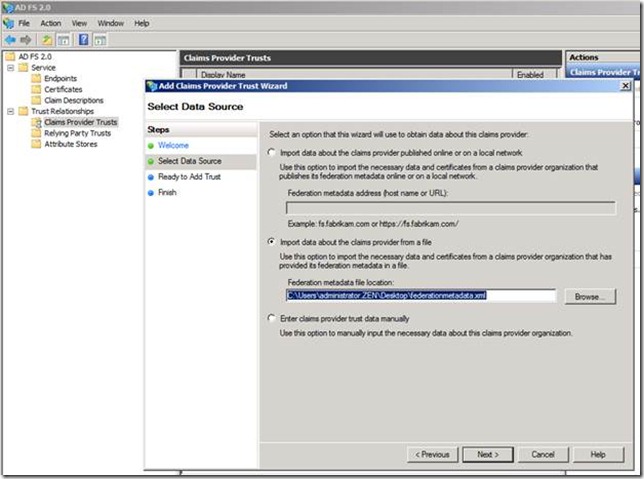
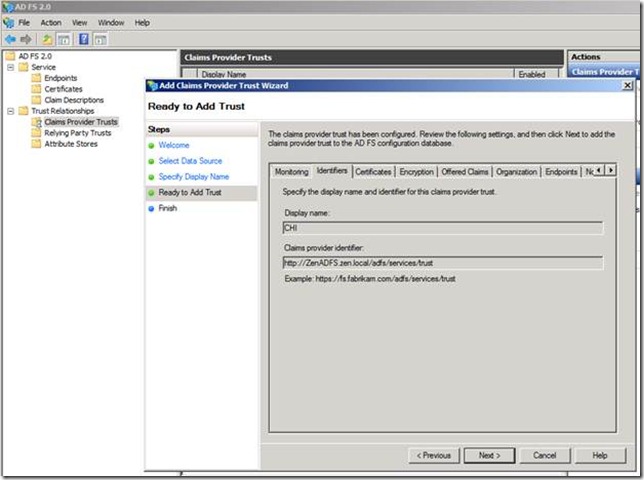
In the select data source we can provide the federation metadata file location of CHI ADFS ( Which we had earlier copied from the CHI ADFS server)
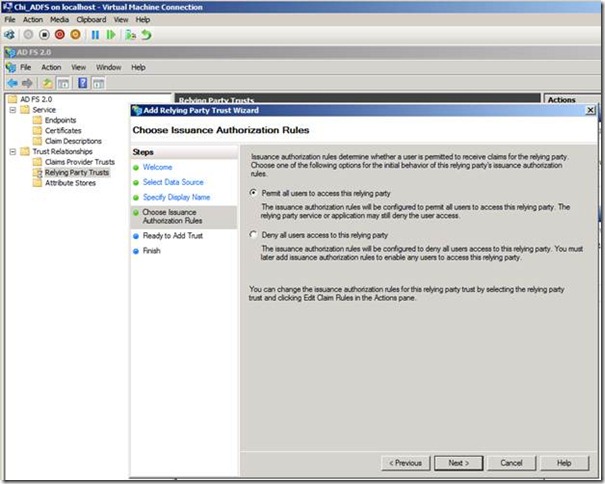
Run through the steps and complete the wizard.
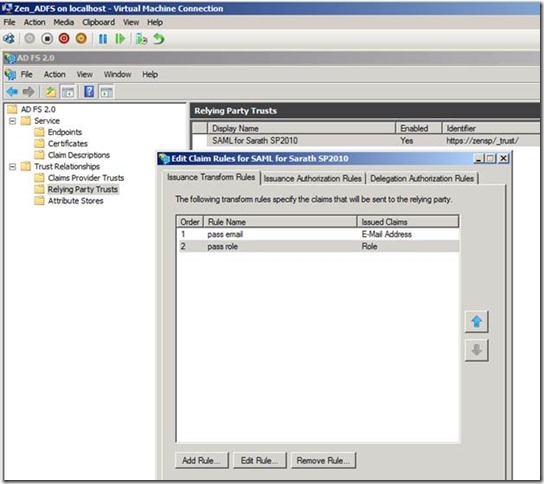
Once the Claims provider trust has completed the steps, next we will need to edit the claims rules.
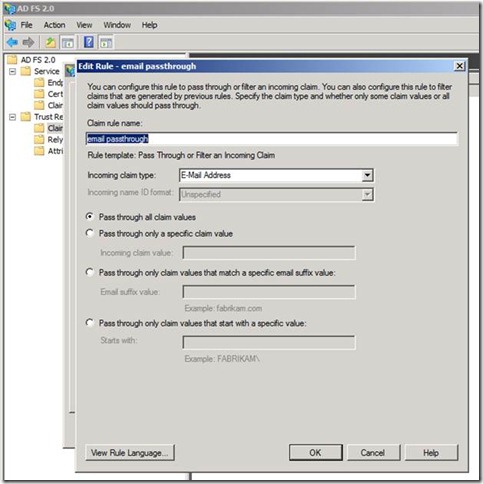
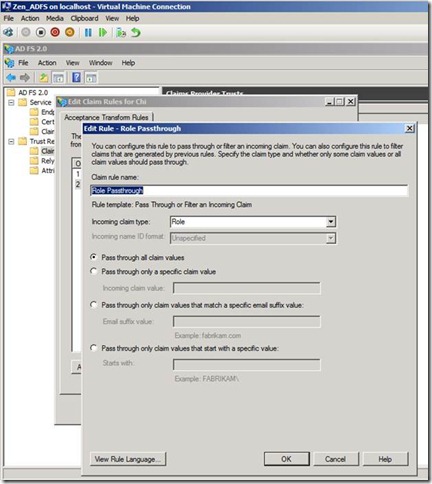
This time we will create two rules one for Email pass through and other for Role pass through.
Note: We have used the Rule template as: Pass through or Filter an incoming claim.
Using the Pass Through or Filter an Incoming Claim rule template in Active Directory Federation Services (AD FS) 2.0, you can pass through all incoming claims with a selected claim type. You can also filter the values of incoming claims with a selected claim type. For example, you can use this rule template to create a rule that will send all incoming group claims. You can also use this rule to send only user principal name (UPN) claims that end with @chi.local.
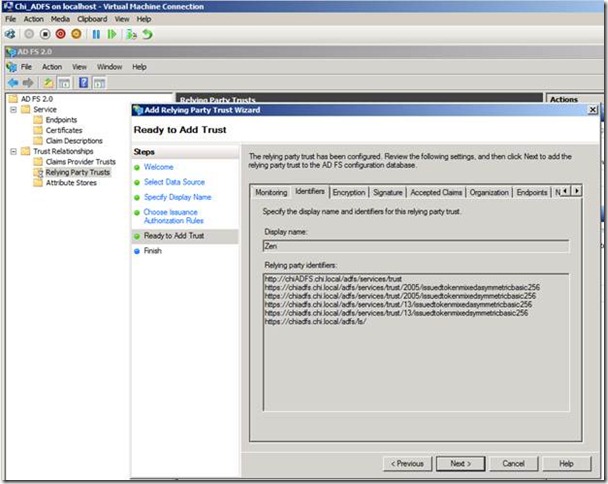
Ok next step is to access CHI ADFS server and add the Relying party trust wizard.
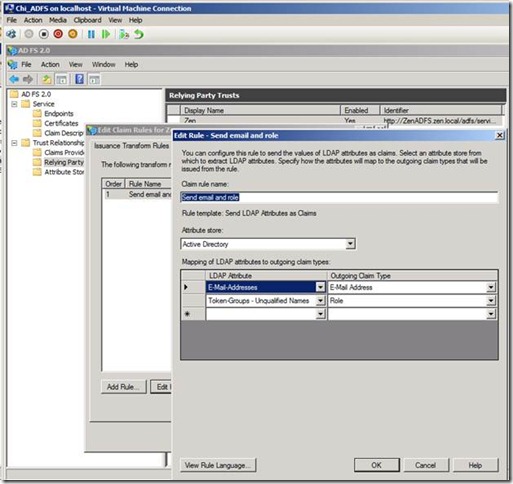
Once you have completed the Relying party trust we need to edit the claim rule as shown below.
This time we will use the template as Send LDAP Attribute as claims as the CHI ADFS server is
Using the Send LDAP Attributes as Claims rule template in Active Directory Federation Services (AD FS) 2.0, you can create a rule that will select attributes from a Lightweight Directory Access Protocol (LDAP) attribute store, such as Active Directory, to send as claims to the relying party.
For example, you can use this rule template to create a Send LDAP Attributes as Claims rule that will extract attribute values for authenticated users from the UPN and Role Active Directory attributes and then send those values as two different outgoing claims.
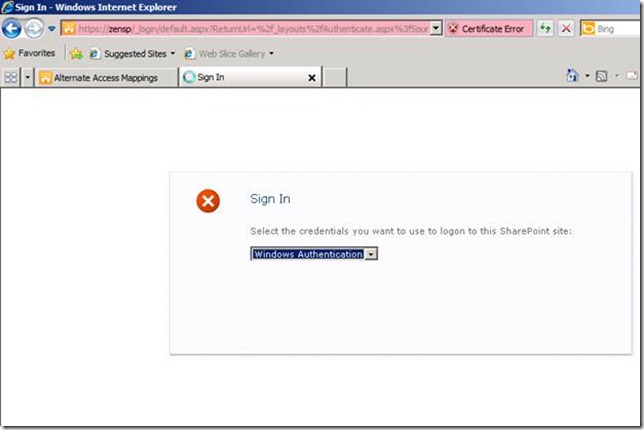
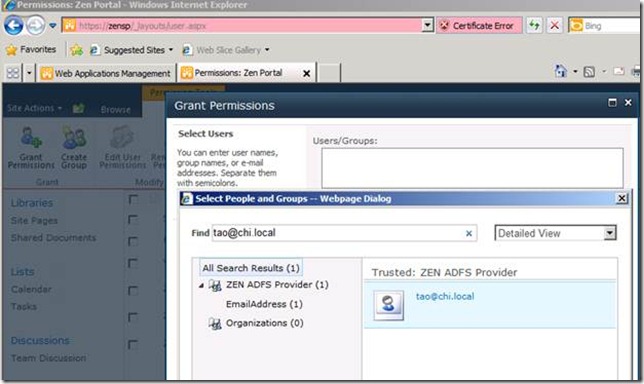
Next I will add a test user to the SharePoint site https://zensp . For this I will need to login using windows credentials, as shown below.
Now it is time for us to test the federation trust between these two forests.
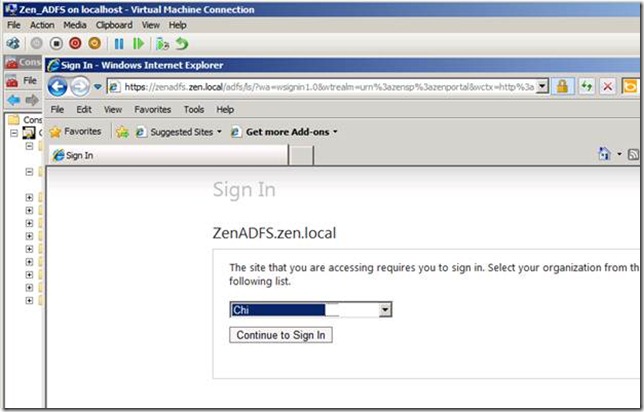
I will login to win7 machine (part of CHI forest) using the user Tao@chi.local .
Next, I will access the site https://Zensp and I will have to choose between the CHI and ZEN provider and
Special thanks to Rahul Gangwar for all the help in setting this up and reviewing this blog post.
I hope you enjoyed the entire series on SharePoint 2010 and ADFS 2.0 Integration. If you still have any questions or need more clarifications, feel free to reach out to me via the Contact link on my blog. I would be more than happy to respond to your queries.
Cheers,
Sarath